Implementation method and device for security gateway based on stream strategy
A technology of a security gateway and an implementation method, which is applied in the field of data communication, can solve problems such as poor parallelism, low utilization efficiency of processors, multi-core processors, and large repetitions, so as to improve the degree of parallelism, improve utilization efficiency, The effect of improving query efficiency
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0045] Embodiment one: if figure 2 As shown, the implementation process of the flow policy-based integrated multifunctional security gateway implementation method provided by the embodiment of the present invention is described in detail as follows:
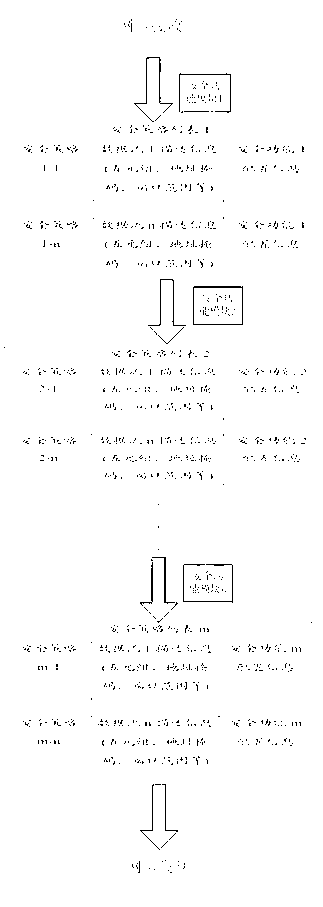
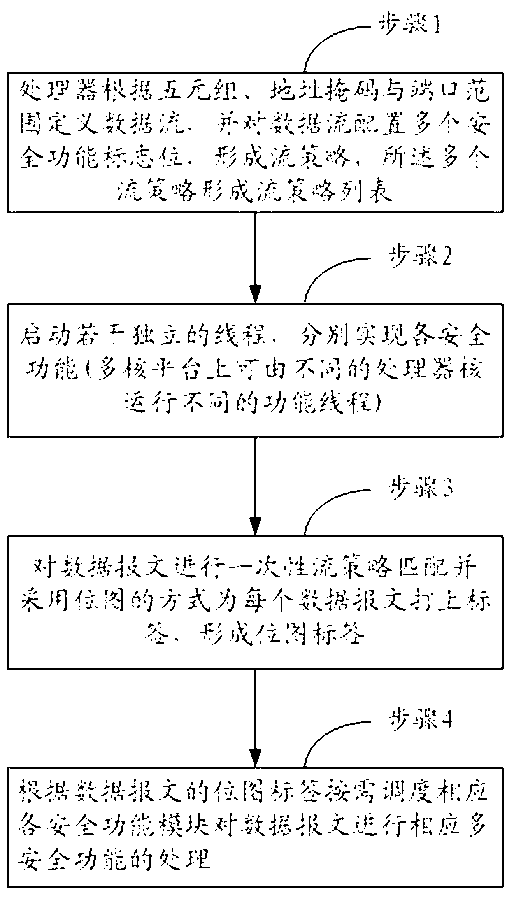
[0046] In step 1, the processor defines the data flow according to the quintuple combined with the address mask and the port range, and performs unified policy setting on the data flow, and configures only one flow policy covering a specific security function for the data flow. A flow policy forms a flow policy list;
[0047] In step 2, the processor starts a plurality of safety function detection threads to implement each safety function respectively. On a multi-core platform, different processor cores can run different function threads, so that each function module can achieve maximum parallelism.
[0048] In step 3, the processor queries and matches the data packet received by the network card with each flow policy in the fl...
Embodiment 2
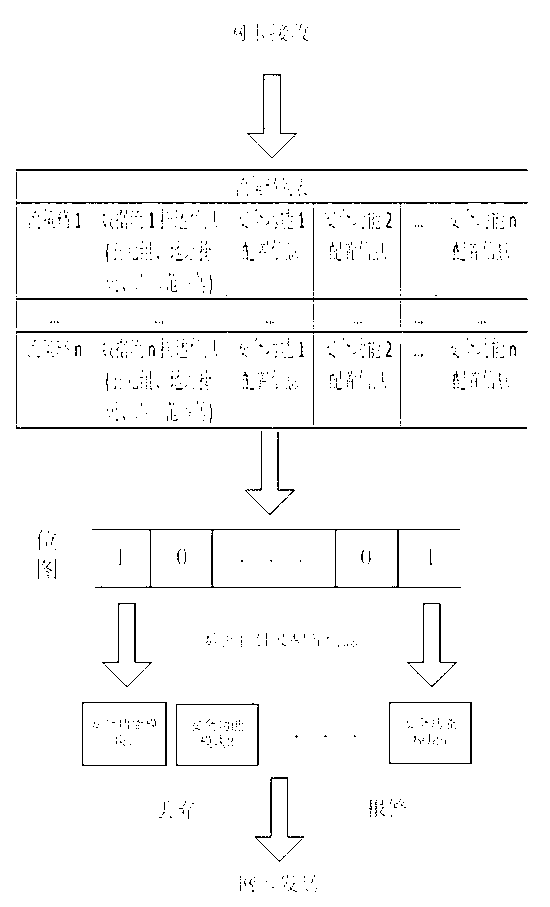
[0050] Embodiment 2: On the basis of Embodiment 1, the flow policy list in step 1 includes multiple flow policies, and the flow policies are different quintuple information, different address masks, different port ranges and multiple security function flags composed flow policy.
Embodiment 3
[0051] Embodiment three: on the basis of embodiment one or two, as image 3 As shown, the specific process of querying and matching the data message received by the network card in step 3 with each flow policy in the flow policy list is described in detail as follows:
[0052] Step 31: By ANDing the source IP address of the data message received by the network card and the destination IP address of the data message with the address mask of each flow policy, if the AND operation result is the same as the source IP address in the flow policy If the destination IP address of the traffic policy is the same, the source IP address of the data packet and the destination IP address of the data packet meet the conditions; otherwise, the data packet is deemed not to match the policy;
[0053] Step 32: By judging that the source port address of the data message received by the network card and the destination port address of the data message received by the network card correspond to the...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com