Security protection method based on public network data transmission information system
An information system and security protection technology, applied in the security protection field of network information systems, can solve the problems of easy eavesdropping and leakage of communication link data, easy impersonation of end users, and replay attacks, etc. The effect of attack, not easy to eavesdrop on leakage
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
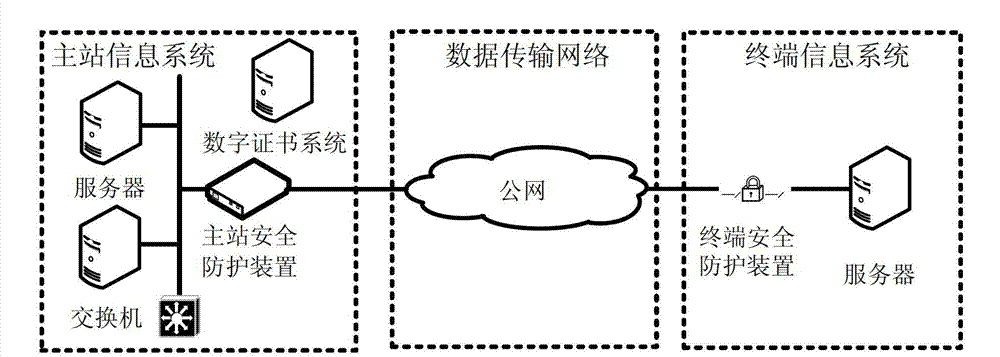
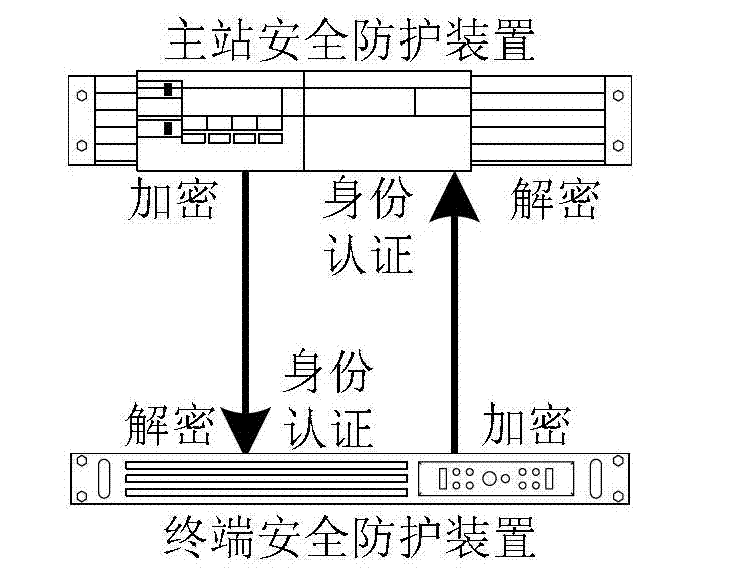
[0022] According to the security protection method based on the public network data transmission information system of the present invention, the information system adopts the working form from the main station to the terminal or from the terminal to the main station, and the method includes the following steps:
[0023] S1 Deploy a master station safety protection device with a first encryption and decryption module at the network boundary of the information system master station, that is, at the data exit of the information system master station;
[0024] S2 deploying a terminal security protection device with a second encryption and decryption module at the network boundary of the information system terminal, that is, at the data exit of the terminal information system;
[0025] S3 has an offline digital certificate system to issue digital certificates for the main station safety protection device and terminal safety protection device;
[0026] S4 The two parties in the com...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com