Classical channel message authentication method and device for quantum key distribution system
A technology of quantum key distribution and message authentication, applied in the field of classical channel message authentication
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
specific Embodiment approach
[0069] The present invention will be described in further detail below in conjunction with the accompanying drawings and embodiments. It should be understood that the specific embodiments described here are only used to explain the present invention, not to limit the present invention.
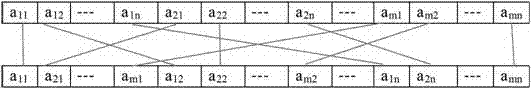
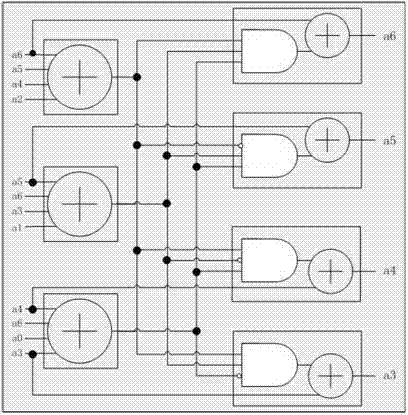
[0070] In this field, CRC-based MAC is a proven message authentication code with information theory security, and its security meets our requirements for the required authentication mechanism. In this system, the hash value of the authenticated message is obtained by using a general hash function, and then the hash value is filled with the one-time pad key as MAC and sent to the receiver together with the authenticated message. An authentication scheme based on cyclic check code CRC such as image 3 As shown, after receiving the message from the channel, the receiver first extracts the original message bit string M and the n-bit MAC value appended to it, and calculates the MAC value of M and ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com