Flash encryption method and device for vehicle-mounted terminal
An encryption method and a vehicle-mounted terminal technology are applied in the field of the vehicle-mounted terminal Flash encryption method and the device thereof, and can solve the problem that the cost cannot be borne by ordinary users.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0031] Below in conjunction with accompanying drawing, preferred embodiment of the present invention is described in further detail:
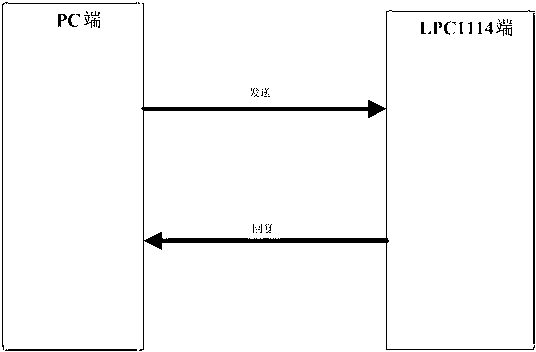
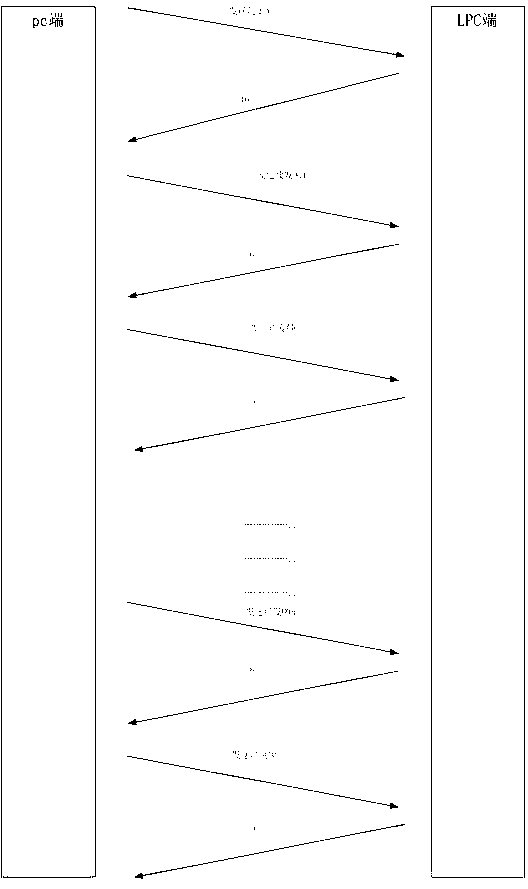
[0032] Such as figure 1 with figure 2 As shown, sending and transferring information between the PC end and the LPC end includes the following steps:
[0033] Step A: In the MCU, generate the ciphertext, compare it with the ciphertext passed from the upper position, if they are the same, the burning is successful;
[0034] Step B: analyze the ISP instruction on the MCU side at the host computer through the serial port, and obtain the serial number of the MCU;
[0035] Step C: pass in the obtained MCU serial number into the MD5 algorithm, and obtain 16-bit MD5 ciphertext after encryption;
[0036] Step D: Utilize the last data block of the MCU to save the corresponding verification information.
[0037] However, the solution of the present invention is not limited to generating ciphertext from the serial number of the MCU, and the ciphertex...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com