Charging method, server, mobile terminal and charging system
A mobile terminal and server technology, applied in the field of network communication, can solve problems such as inconvenient use for users and cumbersome use methods
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
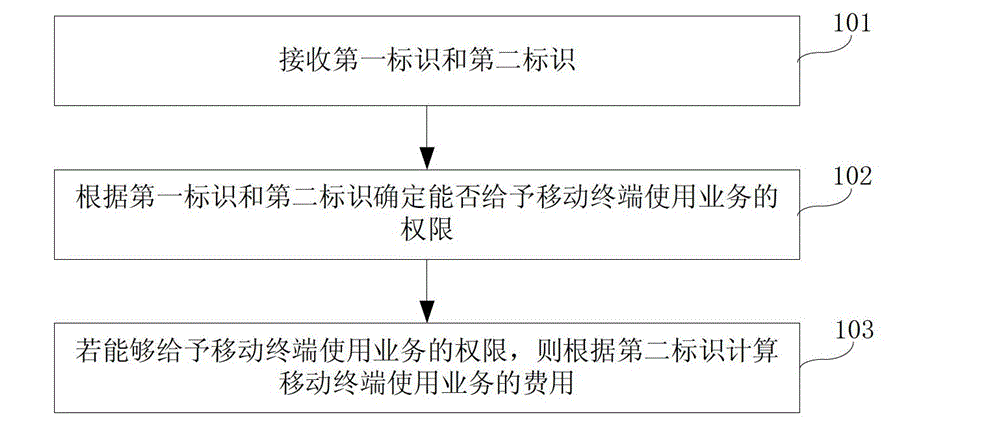
[0113] Please refer to figure 2 , which shows a method flowchart of the billing method provided in Embodiment 1 of the present invention, the billing method includes:
[0114] Step 101, receiving a first identification and a second identification;
[0115] When the mobile terminal needs to use the service, the server can receive the first identification and the second identification. Wherein, the first identifier includes an identifier representing the identity of the mobile terminal when using the service, and the second identifier includes an identifier used by the server to charge the mobile terminal.
[0116] Step 102, according to the first identification and the second identification, it is determined whether the right to use the service can be given to the mobile terminal;
[0117] After the server receives the first identifier and the second identifier, the server can determine whether the mobile terminal can be given the right to use the service according to the re...
Embodiment 2
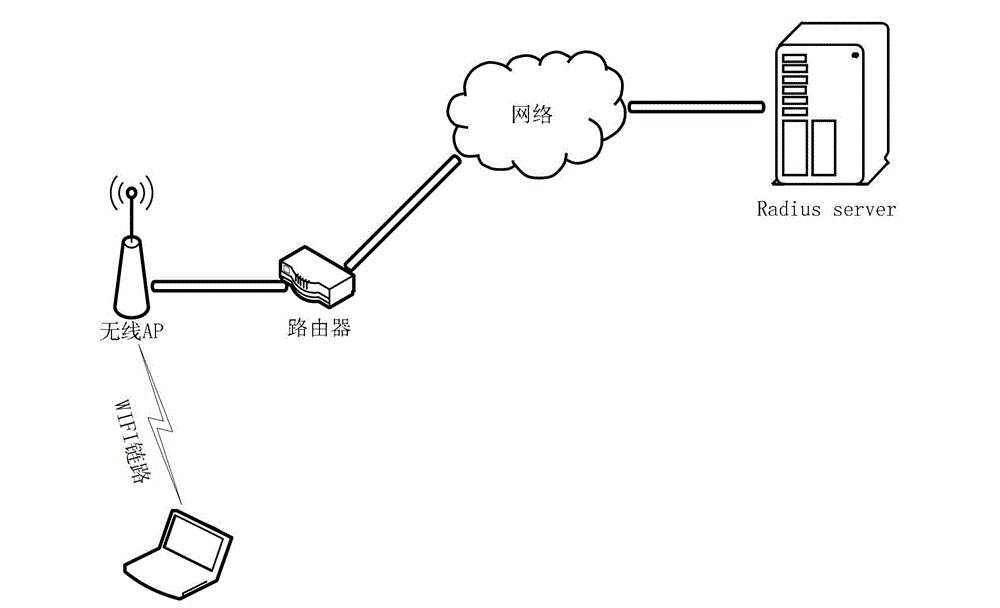
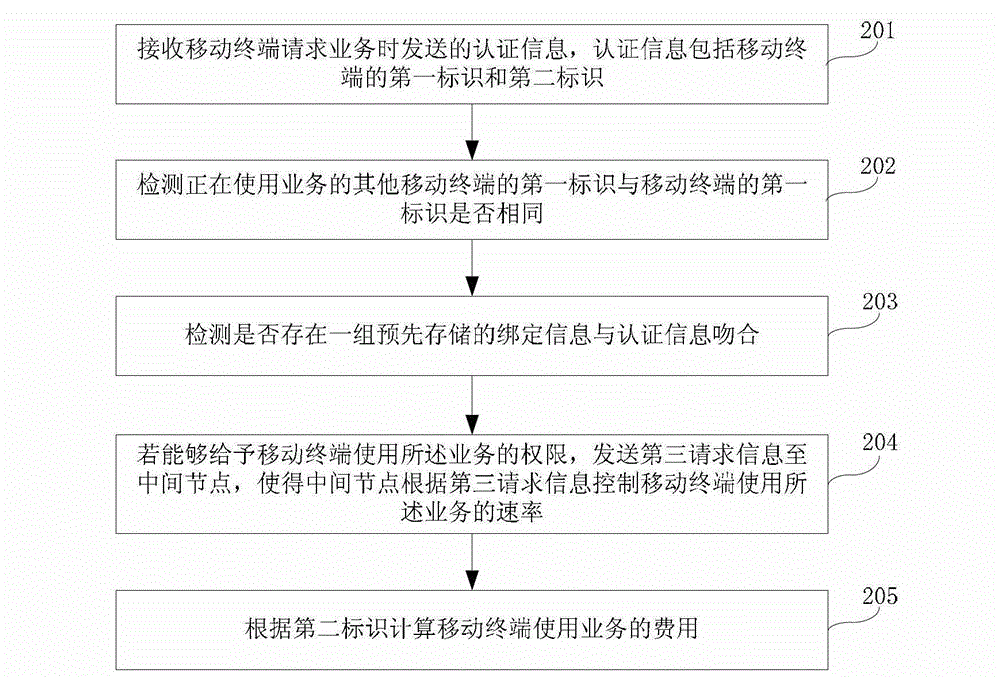
[0123] Please refer to image 3 , which shows the method flow chart of the charging method provided by the second embodiment of the present invention. In this embodiment, the charging method is mainly applied to WIFI charging for the mobile terminal with the second identification itself, and the server assigns the mobile terminal For example, the authentication information sent when using WIFI for the first time is stored as binding information. The billing method includes:
[0124] Step 201, receiving authentication information sent when the mobile terminal requests a service, the authentication information including the first identification and the second identification of the mobile terminal;
[0125] When the mobile terminal needs to use WIFI to surf the Internet, the mobile terminal can send authentication information to the server, and correspondingly, the server can receive the authentication information requesting to use WIFI sent by the mobile terminal.
[0126] Wher...
Embodiment 3
[0157] Please refer to Figure 5 , which shows the method flow chart of the billing method provided by Embodiment 3 of the present invention. In this embodiment, the billing method is still applied to the WIFI billing of the mobile terminal with the second identity itself as an example, but it is different from the implementation The difference in Example 2 is that in this embodiment, when the mobile terminal activates the WIFI service, the server may pre-store at least one set of binding information including the first identifier and the second identifier, and the charging method includes:
[0158] Step 301, pre-store at least one set of binding information, the binding information includes a first identifier and a second identifier;
[0159] When the mobile terminal activates the WIFI service, the server may store a set of binding information, where the binding information includes the first identifier and the second identifier.
[0160] Wherein, the first identifier includ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com