Network risk assessment method based on combination of Bayesian algorithm and matrix method
A Bayesian algorithm and risk assessment technology, applied in the field of network security assessment, can solve problems such as lack of, lack of overall consideration of network node relevance, lack of consideration of risk time occurrence probability, etc., to improve accuracy and improve practical guidance meaning effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
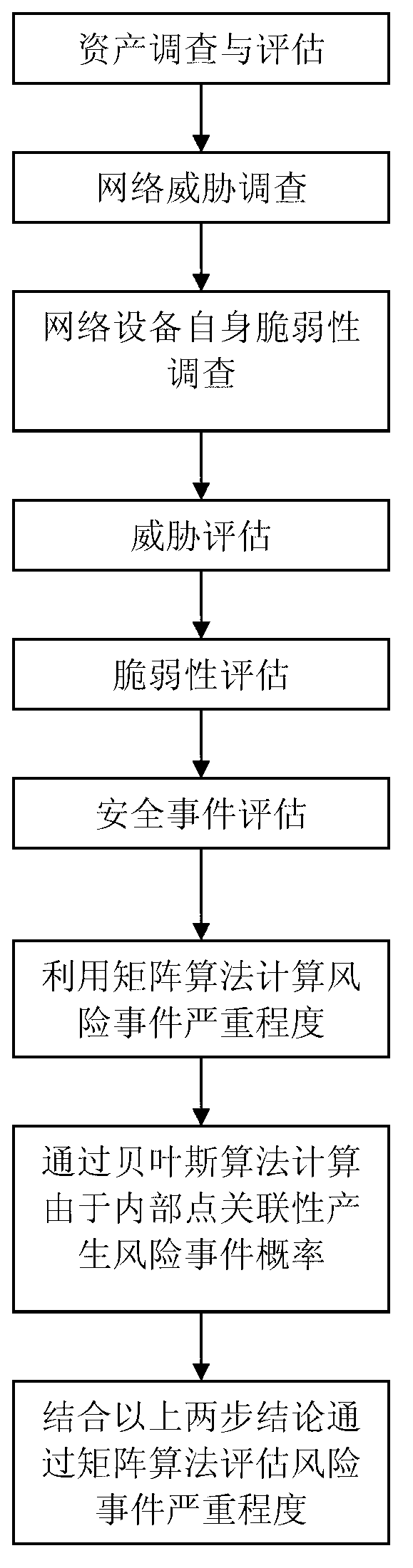
[0025] Step 1: Use the topology auto-discovery tool to use the SNMP protocol to automatically detect network devices and build a network topology. Collect the basic information of the network devices, and use the matrix algorithm or the geometric mean algorithm to evaluate the confidentiality, integrity, and availability of the collected devices equipment value.
[0026] Step 2: Build a threat knowledge base. Methods A threat questionnaire was established automatically based on the knowledge base to collect network threats and the frequency of threats.
[0027] Step 3: Build a vulnerability knowledge base. Vulnerabilities are mainly divided into technical vulnerabilities and management vulnerabilities. Technical vulnerabilities are mainly automatically discovered and identified through vulnerability scanning tools. The vulnerability of the management category is automatically established through the knowledge base to collect the vulnerability through the vulnerability quest...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com