Optical fiber web encryption communication system based on time hidden signal channel
An encrypted communication system and covert channel technology, applied in the field of optical fiber network encryption communication system based on time covert channel, can solve problems such as powerlessness, data encryption technology crisis, reduced difficulty in deciphering passwords, etc., to achieve good integrity and reliability, maintain Integrity and reliability, strong anti-interference ability
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
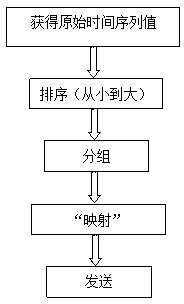
[0028] combine figure 1 , the time covert channel adopted by the present invention "replays" previously recorded events through a simple but effective triple strategy:
[0029] An optical fiber network encryption communication system based on time covert channel, comprising the following steps:
[0030] [1] Obtaining the original time series value of the sender;
[0031] [2] The sender sorts the obtained time series values, and divides the sorted time series values into 2 groups, one group corresponds to binary 0, and the other group corresponds to 1;
[0032] [3] The sender makes a one-to-one correspondence between the data to be sent and the sorted and grouped time series values;
[0033] [4] The sender controls the sending rate according to the time series value;
[0034] [5] Decoding of the receiver.
Embodiment 2
[0036] combine figure 1 , the time covert channel adopted by the present invention "replays" previously recorded events through a simple but effective triple strategy:
[0037] An optical fiber network encryption communication system based on time covert channel, comprising the following steps:
[0038] [1] Obtaining the original time series value of the sender;
[0039] [2] The sender sorts the obtained time series values from large to small, finds the median of the sorted sequence values, divides them into two groups according to the median, and divides the sorted time series values into 2 Group, one group corresponds to binary 0, and the other group corresponds to 1;
[0040] [3] The sender makes a one-to-one correspondence between the data to be sent and the sorted and grouped time series values;
[0041] [4] The sender controls the sending rate according to the time series value;
[0042] [5] Decoding of the receiver.
Embodiment 3
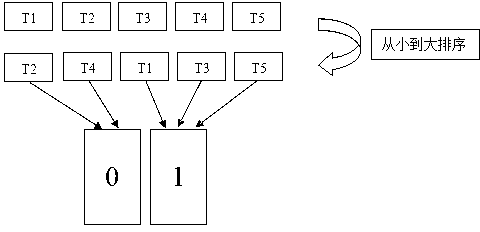
[0044] combine figure 2 , after obtaining the previously recorded time series value, sort it from largest to smallest. The median t of the sorted sequence values can then be obtained, in figure 2 The median T1 is this median. Finally, according to the median, both parties use the same rule to divide the sequence into two parts: [0, t) and [t, max], the former part corresponds to binary 0, and the latter part corresponds to binary 1.
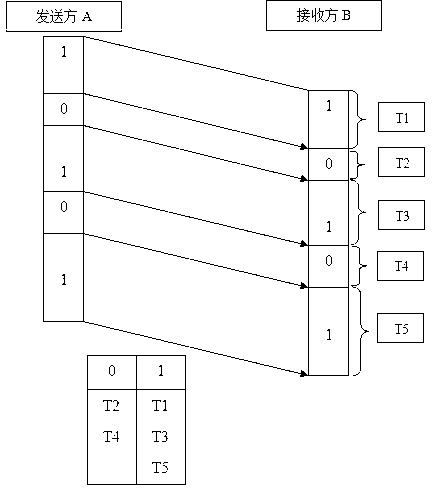
[0045] combine image 3 , in order to leak consecutive bits to B, A generates a sequence of packets and encodes the covert information by adjusting the arrival time interval between these packets. To further simulate legitimate behavior and avoid generating normal packet sequences, the packet timing is adjusted according to previously recorded normal sequences. Therefore, the choice of sequence interval directly affects the concealment of the channel, and the more the input arrival sequence interval can imitate legitimate behavior, the be...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com