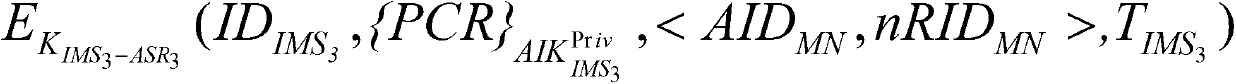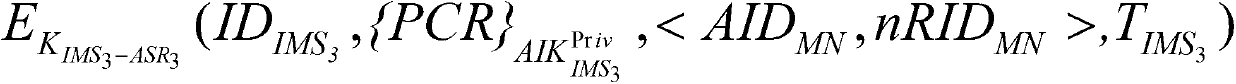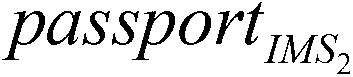Mapping updating authentication method among credible regions in separation mechanism networks
A technology of mapping update authentication and separation mechanism network, applied in the field of computer security, can solve problems such as failure to provide identity authentication, platform tampering virus infection, security defects, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0067] Such as figure 1 In the embodiment shown, the trusted inter-domain mapping update authentication model framework is as follows figure 1 shown.
[0068] In the above model, all domains have only one public AC and Privacy-CA. The access switch router ASR (Access Switch Router) is a trusted access switch router embedded with a TPM chip, the MN is a mobile terminal, and the IMS is a trusted mapping server, which is used to store the mapping relationship of terminals in the domain. In the local domain, the MN accesses the network through the ASR. The connection between the local domain and the foreign domain is realized by the General Switch Router (GSR).
[0069] AC is responsible for verifying the identities of terminals, routers, and mapping servers, and issuing passports for mapping servers. Privacy-CA is responsible for verifying the IMS platform and distributing AIK platform certificates to it.
[0070] Assume that the mobile terminal MN from the ASR 2 move to AS...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com