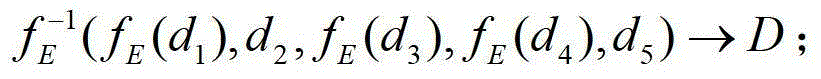Unstructured data security exchange method based on user behavior credibility
A technology of unstructured data and secure exchange, which is applied in the field of data security exchange, can solve the problems of insufficient consideration of data exchange security, and achieve the effect of improving flexibility or scalability, improving scalability, improving efficiency and security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0041] The technical solutions in the embodiments of the present application will be clearly and completely described below in conjunction with the drawings in the embodiments of the present application.
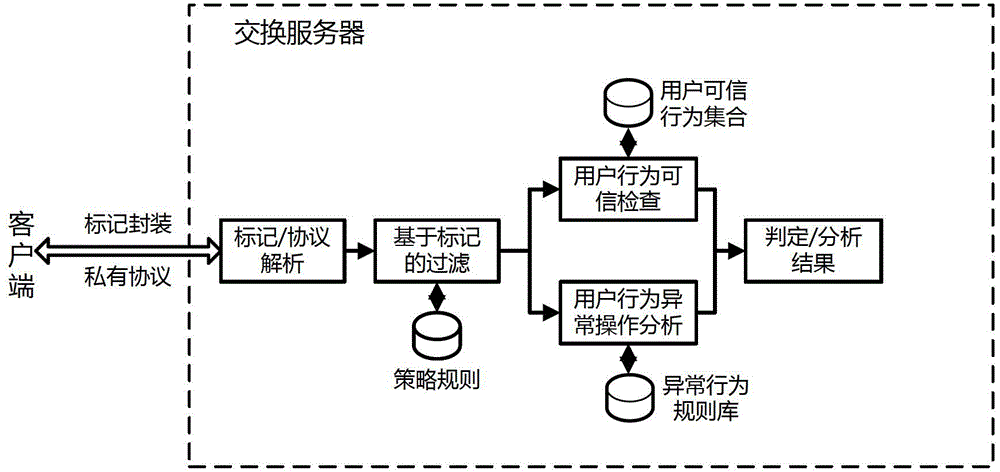
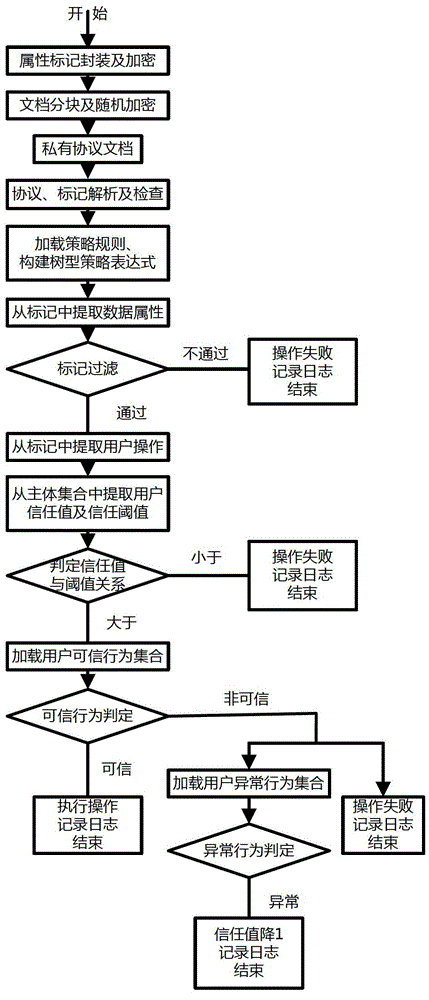
[0042] figure 1 It shows a component structure diagram of a method for safe exchange of unstructured data provided by the present invention; the unstructured data in this embodiment is a part of user A's information exchanged from the Internet network to the internal network of the enterprise through the isolated exchange system. Secret document D. in,
[0043] ①: Data attribute A of the confidential document D D It is: the document mentioned is a confidential document, the secret level is the first level of business secret, the key word of the document is a technical report, and the catalog that is allowed to be uploaded is a budget report;
[0044] ②: User operation behavior U op It is: the source IP address is IP1, the source port is Port1, the destination IP address ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com