File breaking encryption-based file security protection method
A technology of security protection and encryption algorithm, applied in the field of document security protection based on file fragmentation and encryption, it can solve the problems of encryption algorithm restoration, illegal acquisition of document keys, etc., and achieve the effect of solving leakage.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
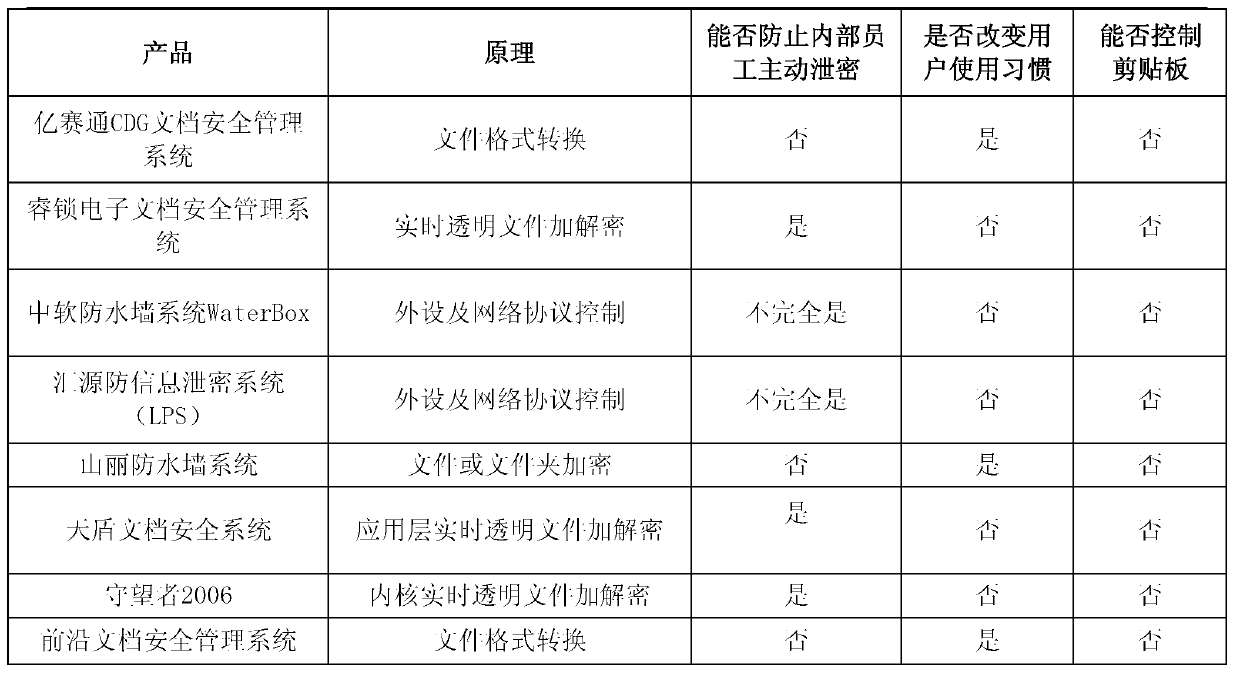
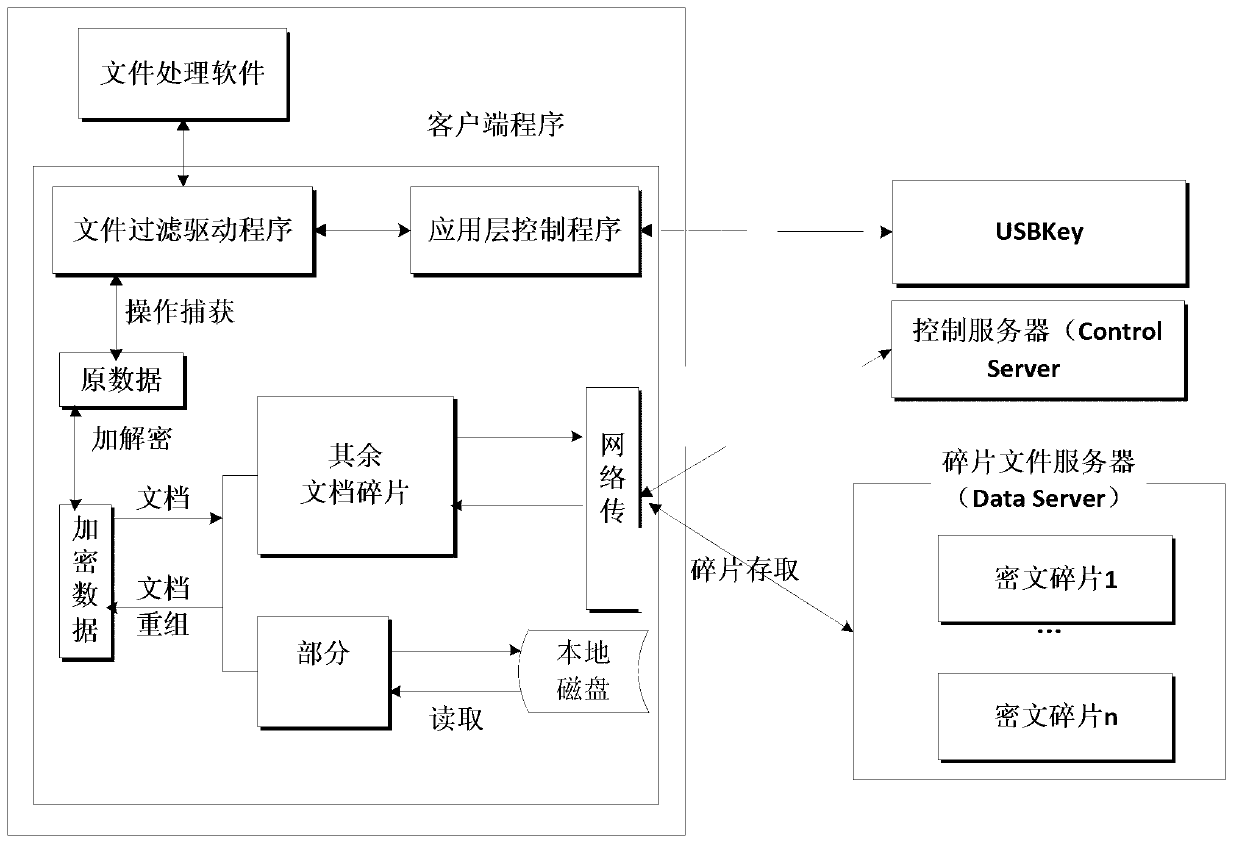
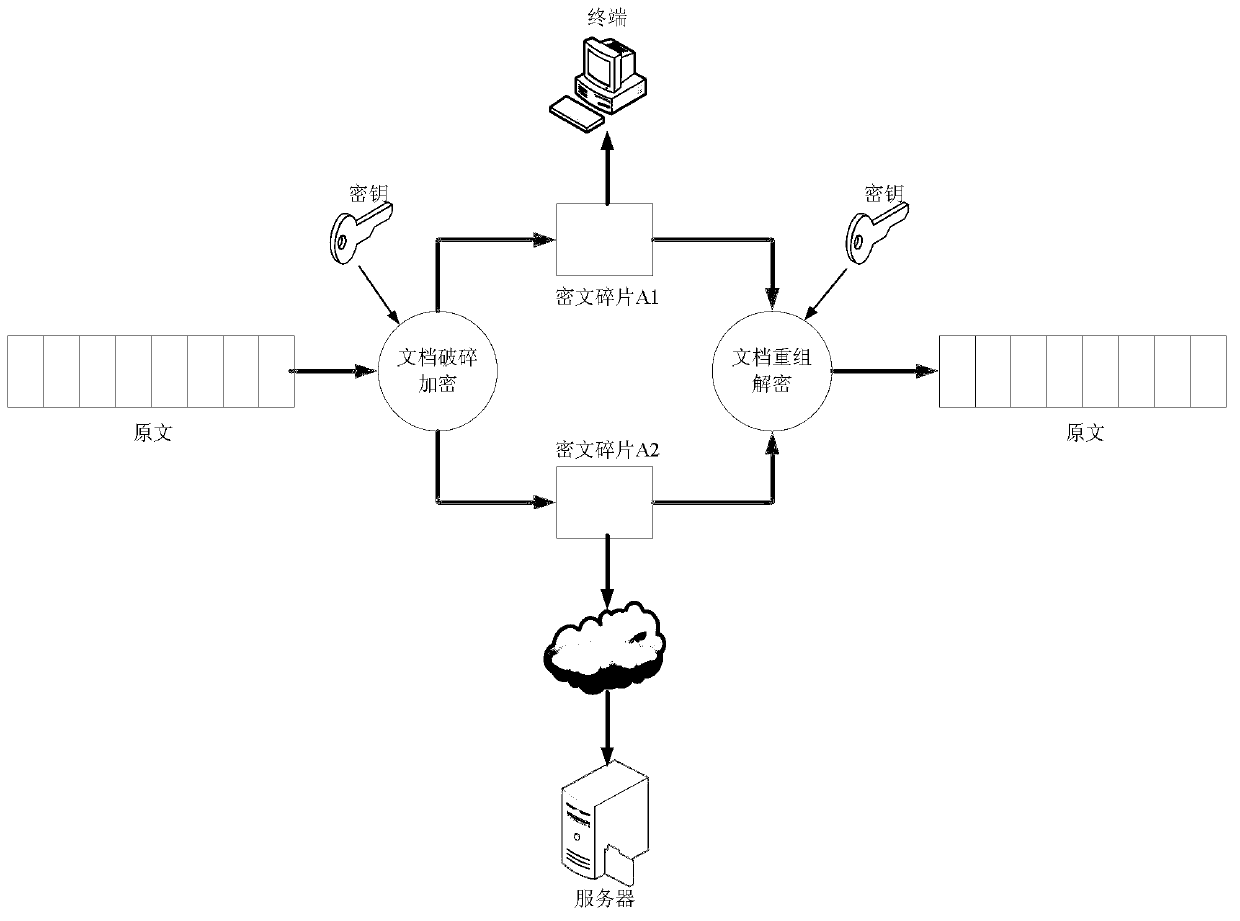
[0025] The main innovation in the file security protection method based on file fragmentation encryption provided by the present invention is the document fragmentation and reorganization technology: traditional encryption systems use keys and encryption algorithm strengths to ensure the security of encrypted data. Based on the traditional encryption method, the present invention introduces "ciphertext fragmentation" technology to further enhance the security of file access. The basic idea of "ciphertext fragmentation" technology is: use the document fragmentation algorithm to fragment the original file A into file header A0 and multiple ciphertext fragments A1, A2...An, and store A1, A2...An in the user terminal and the dedicated server respectively superior. No matter which fragment is obtained, it is very difficult to restore the original information from it. When the user opens the file and clicks the file header A0 on the user terminal, the system authenticates the use...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com