Data file security management system and method based on information separation
A data file and security management technology, applied in the direction of digital data protection, etc., can solve the problems of illegal theft of information and data, difficulty in obtaining encryption algorithms, and difficulty in achieving low-cost and high-intensity security management for core data, so as to prevent illegal theft Or crack, prevent the effect of random spread
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
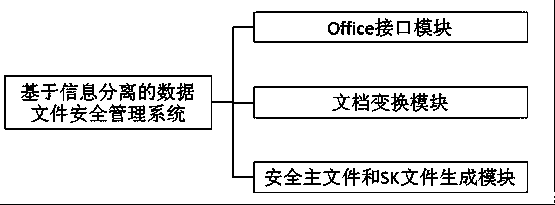
[0016] Attached below figure 1 The data file security management system based on information separation of the present invention is further described:
[0017] The nouns appearing in this article are explained as follows:
[0018] Featureless data file: A linear transformation algorithm is used to crush the format information of the target file, so that the information content of the document is evenly distributed,
[0019] SK file: The extracted data and location information form an SK file, which is stored in a dedicated SK disk as the key file used to open the corresponding document, and can only be saved in a dedicated SK disk. The SK file cannot be viewed or opened by ordinary methods ;
[0020] Security master file: the subject of the file after random extraction of the featureless data file, it needs to cooperate with the SK file to restore the original file;
[0021] Confidential file: security master file and Sk file from the same file;
[0022] SK disk: U disk de...
PUM
 Login to view more
Login to view more Abstract
Description
Claims
Application Information
 Login to view more
Login to view more - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap