Network safety access control method based on ICAP
A network security and access control technology, applied in the field of network access control, can solve the problems of low accuracy and poor real-time flow control, and achieve the effect of strong real-time performance, low maintenance cost and performance improvement.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment
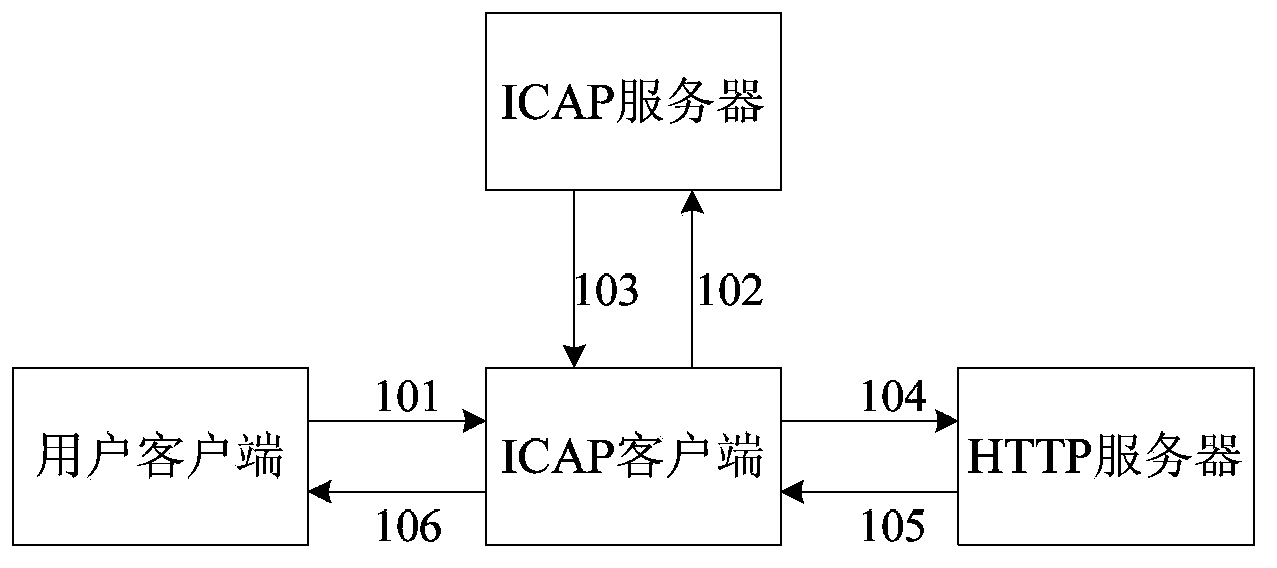
[0033] The network security access control method based on the ICAP protocol of the present invention includes URL filtering control and HTTP flow control, such as figure 1 The URL filtering control shown is the security control when the user client sends an HTTP request to the HTTP server, including the following steps:
[0034] Step 101: the user client sends an HTTP request to the ICAP client;
[0035] Step 102: The ICAP client HTTP request is encapsulated as an ICAP Preview-based ICAP request and sent to the ICAP server;
[0036] Step 103: the ICAP server sends corresponding action instructions to the ICAP client according to the URL address in the ICAP request to the decapsulated ICAP request, the action instructions include blocking action instructions, warning action instructions, and detection and recording action instructions;
[0037] Step 104: The ICAP client sends return information to the user client according to the received action instruction, and sends the HTT...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com