Method and device for controlling malicious domain name and illegal access
A technology of illegal access and control methods, applied in electrical components, transmission systems, etc., can solve problems such as being unsuitable for black and white list filtering services, affecting system availability, and small number of users, improving storage and search efficiency, and shortening single locks. Time, deployment and flexible effects
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0038] The present invention will be further described below in conjunction with the accompanying drawings.
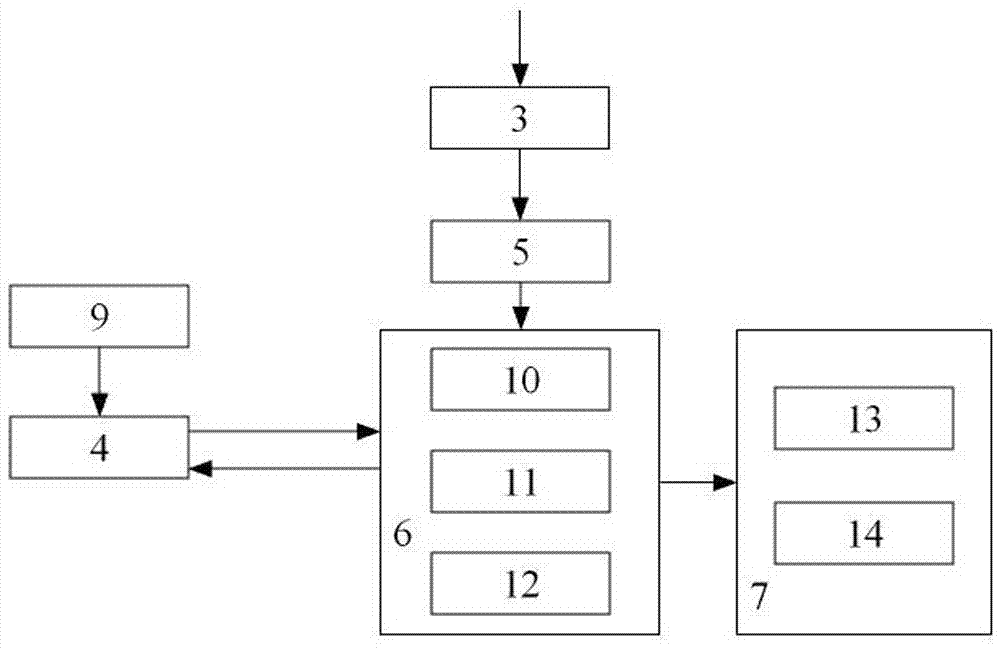
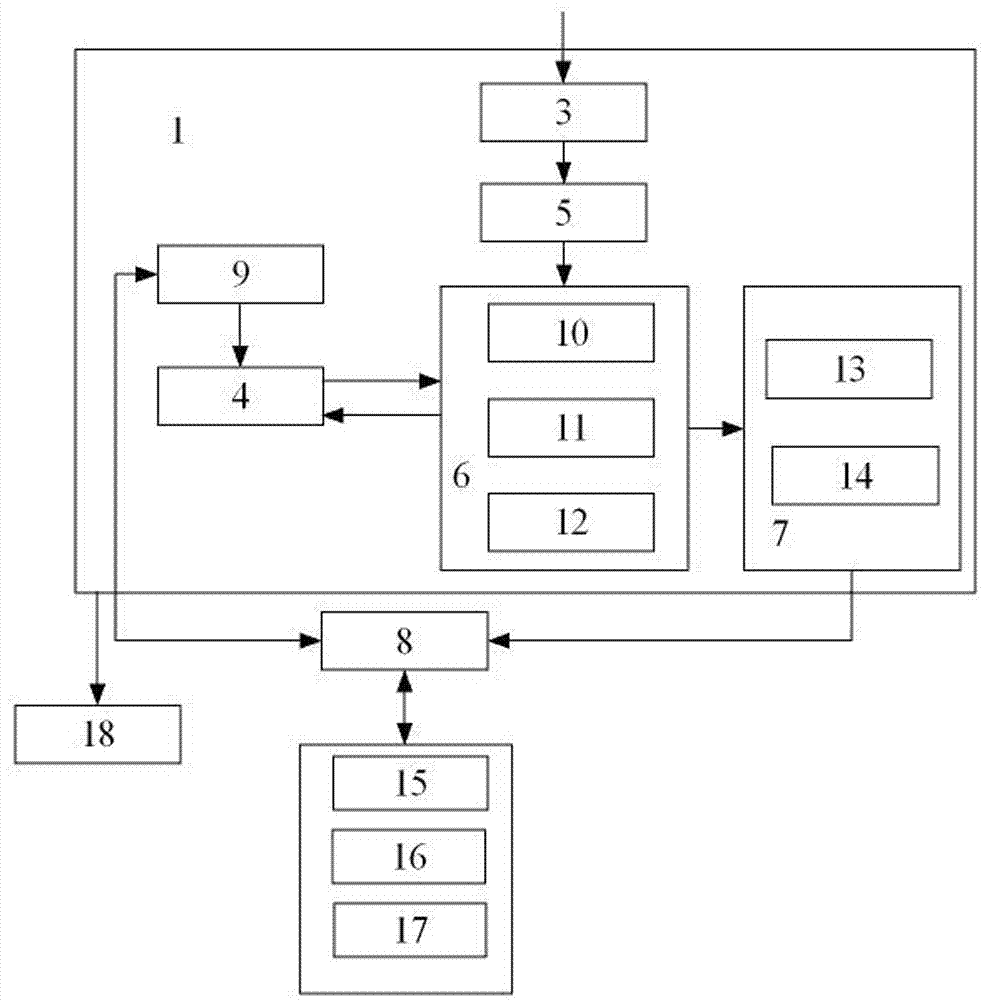
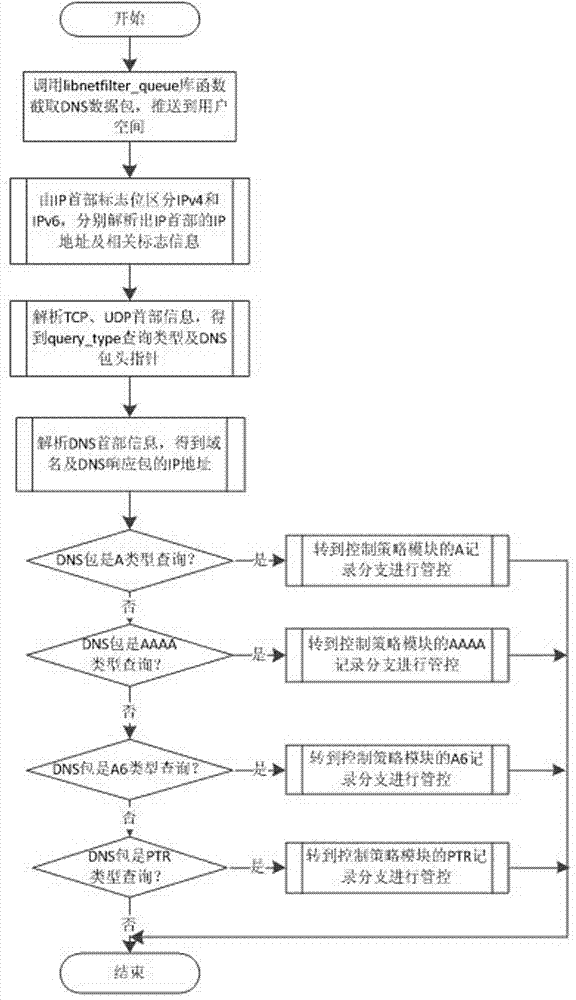
[0039] Aiming at the deficiencies of the prior art, the present invention proposes a control method and device for malicious domain names and illegal access that can efficiently control malicious domain names and illegal access, wherein the secure domain name server middleware 1 is deployed on the DNS server, such as attached figure 1 As shown, it includes a kernel mode protocol stack packet interception module 3, a user mode DNS parsing module 5, a black / white list matching module 4, a black / white list index database 9, a control policy module 6 and a log module 7. The kernel mode protocol stack data packet interception module 3 is connected with the user mode DNS analysis module 5, the user mode DNS resolution module 5 is connected with the control strategy module 6, the control strategy module 6 is connected with the blacklist matching module 4, and the blacklist ma...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com