Secure network transaction method
A transaction method and network security technology, applied in secure communication devices, payment systems, transmission systems, etc., can solve the problems of scratch card usage limit, cumbersome operation, loss of USBKey or dynamic password or being stolen by others, and achieve Safe online transactions, high security, and easy operation
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
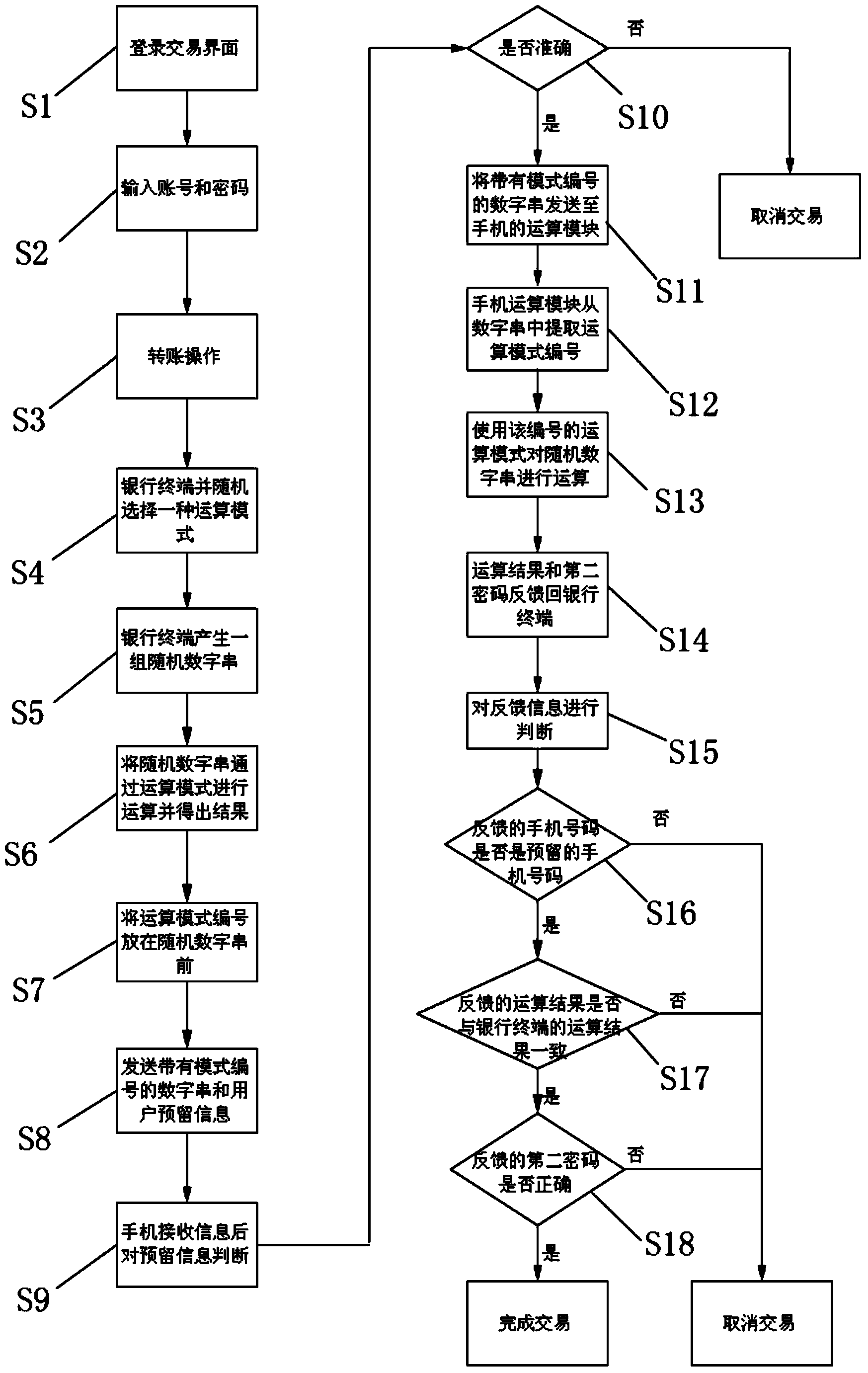
[0022] see figure 1 , which is a flow chart of the network security transaction method of the present invention. The network security transaction method includes the following steps:
[0023] S1: The user uses the client host to log in to the trading interface;
[0024] S2: Enter the bank account number and password;
[0025] S3: carry out the transfer operation;
[0026] S4: The bank terminal randomly selects an operation mode;
[0027] S5: The bank terminal generates a set of random number strings;
[0028] S6: the bank terminal operates the digital string in the operation mode of step S4, and stores the operation result in the bank terminal;
[0029] S7: Put the operation mode number before the random number string;
[0030] S8: Send the digital string with the mode number and the reservation information of the user at the bank terminal to the user's mobile phone;
[0031] S9: judge the reserved information;
[0032] S10; when the reserved information is correct inf...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com