Cluster group call security encryption synchronization method
A security encryption and group call technology, which is applied in the field of communication, can solve problems such as passwords are easy to be cracked, the duration of secure calls is short, and the security of trunk group calls cannot be met, so as to achieve the effect of improving security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0023] In order to make the object, technical solution and advantages of the present invention more clearly, the present invention will be further described in detail below in conjunction with the accompanying drawings and specific embodiments.
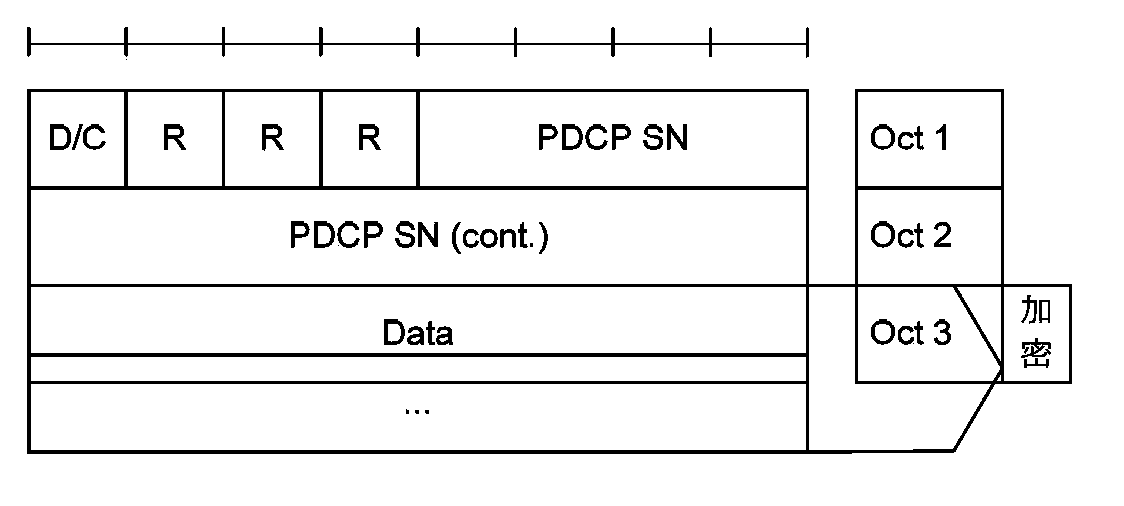
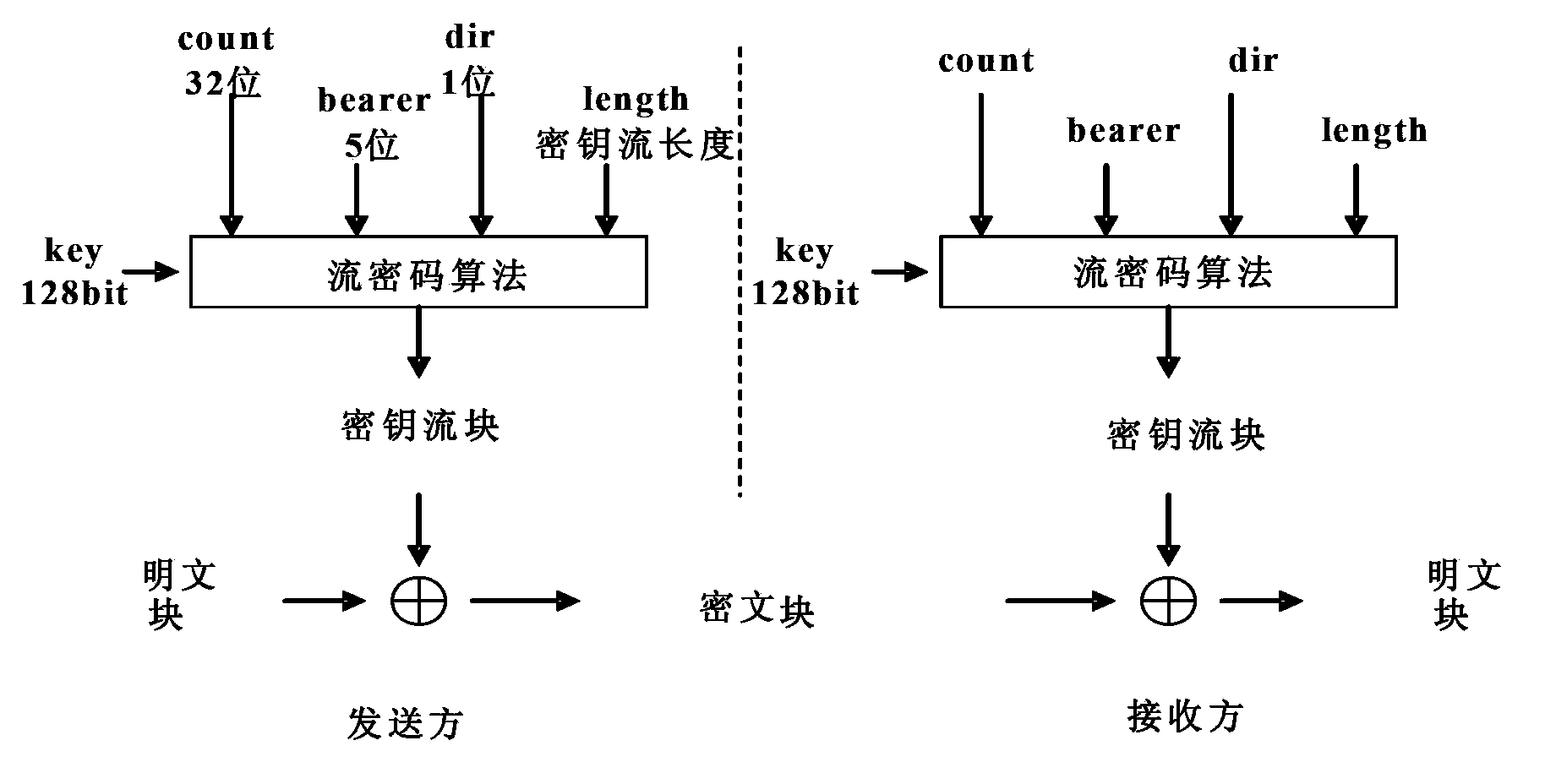
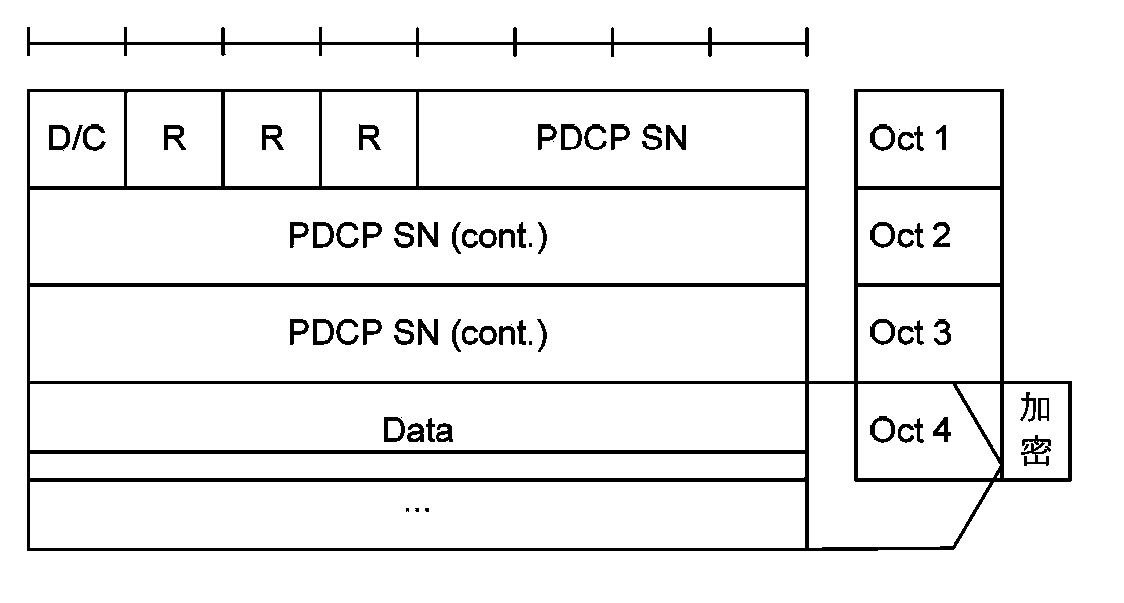
[0024] In the embodiment of the present invention, the number of SN digits in the PDU header is extended by N bits, the COUNT is composed of the extended SN and HFN, and the total length is still 32 bits; the encryption and decryption is performed by the COUNT including the extended SN using the stream cipher algorithm Password sync. Due to the adoption of the above technical solution, N is determined by the group call time limit. On the one hand, the safe call time can meet the needs of group calls. On the other hand, the SN will not overflow during a call. Therefore, eNB and UE do not need to maintain the HFN value. In addition, since the SN becomes longer and no longer overflows, the out-of-sync probability of the communication sys...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com