Weak password analysis method and system
An analysis method and weak password technology, applied in the field of weak password analysis methods and systems, can solve problems such as slow verification of weak passwords, inability to quickly check weak passwords, idle computing resources, etc., to make up for the overload of server resources and fast The effect of weak password verification work and reasonable allocation of computing resources
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0066] In order to make the object, technical solution and advantages of the present invention clearer, the implementation manner of the present invention will be further described in detail below in conjunction with the accompanying drawings.
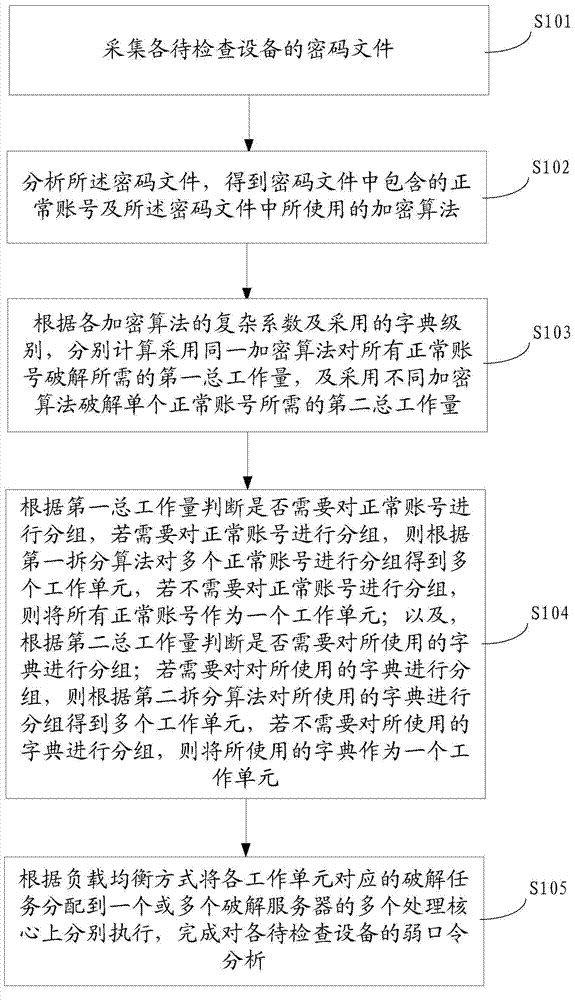
[0067] The embodiment of the present invention analyzes the weak password situation based on the weak password dictionary, optimizes the weak password analysis method, achieves the purpose of rationally allocating computing resources and quickly performing weak password verification work. Solving the problem of slow verification of weak passwords and making full use of hardware resources not only saves a lot of manpower and material resources, but also greatly improves the efficiency of device weak password analysis and verification, and overcomes the shortcomings of unbalanced distribution of computing resources, laying a solid foundation for security.
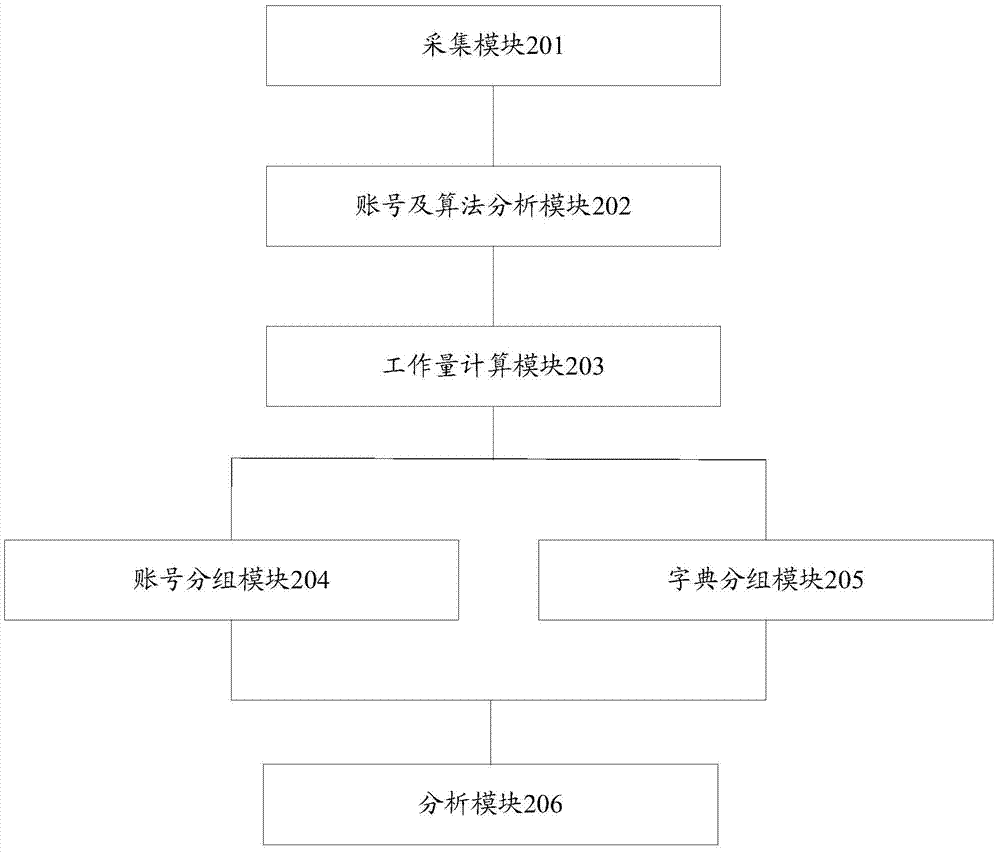
[0068] see figure 1 , the embodiment of the present invention provides a weak pas...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com