Control method and control system for accessing to computer file contents
A technology of file control and control method, applied in computer security devices, computing, special data processing applications, etc., can solve problems such as information protection defects, file security management system without network communication analysis and monitoring functions, and incomplete information protection, etc., to achieve Significant practical significance, advanced technology, and the effect of solving information security problems
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
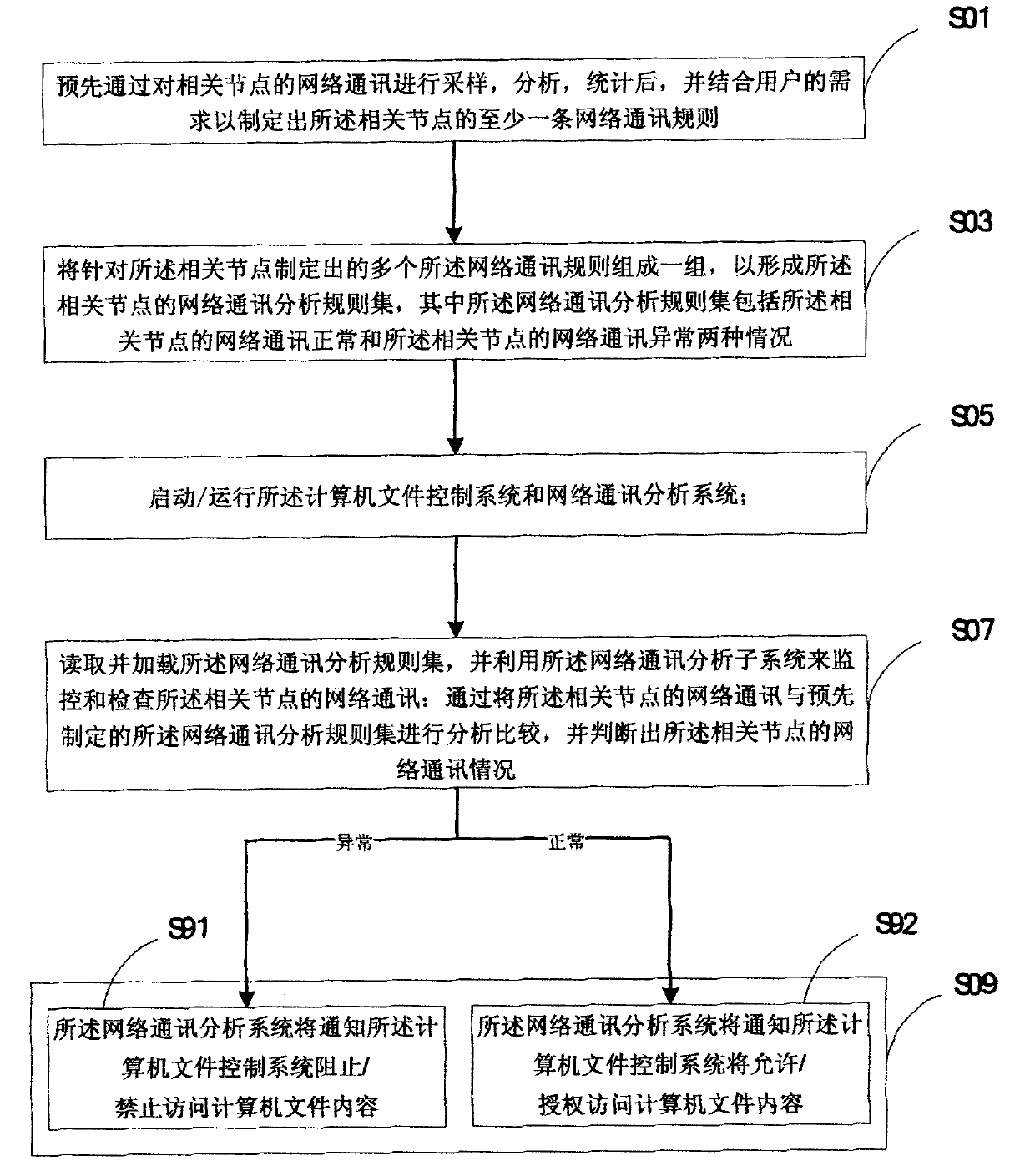
[0053] In this embodiment, the operation of restricting access to file content through a remote desktop network connection is used as an example to illustrate, and it is applied in a systematic manner, and the network communication analysis system runs in the network equipment of the access layer, and the situation of distributed deployment is not considered here , the computer file control system runs on multiple terminals, and the terminals have network connections with the network device.
[0054] First, set the network communication analysis rule set based on the above S01 and S03. The specific method is: include the remote desktop network connection in the network communication exception rules to form a corresponding network communication analysis rule set; here the remote desktop network The judgment of the connection can be based on the following characteristics: TCP protocol, TPKT protocol, COTP protocol, etc.; the setting of the target address (MAC) is set in the way o...
Embodiment 2
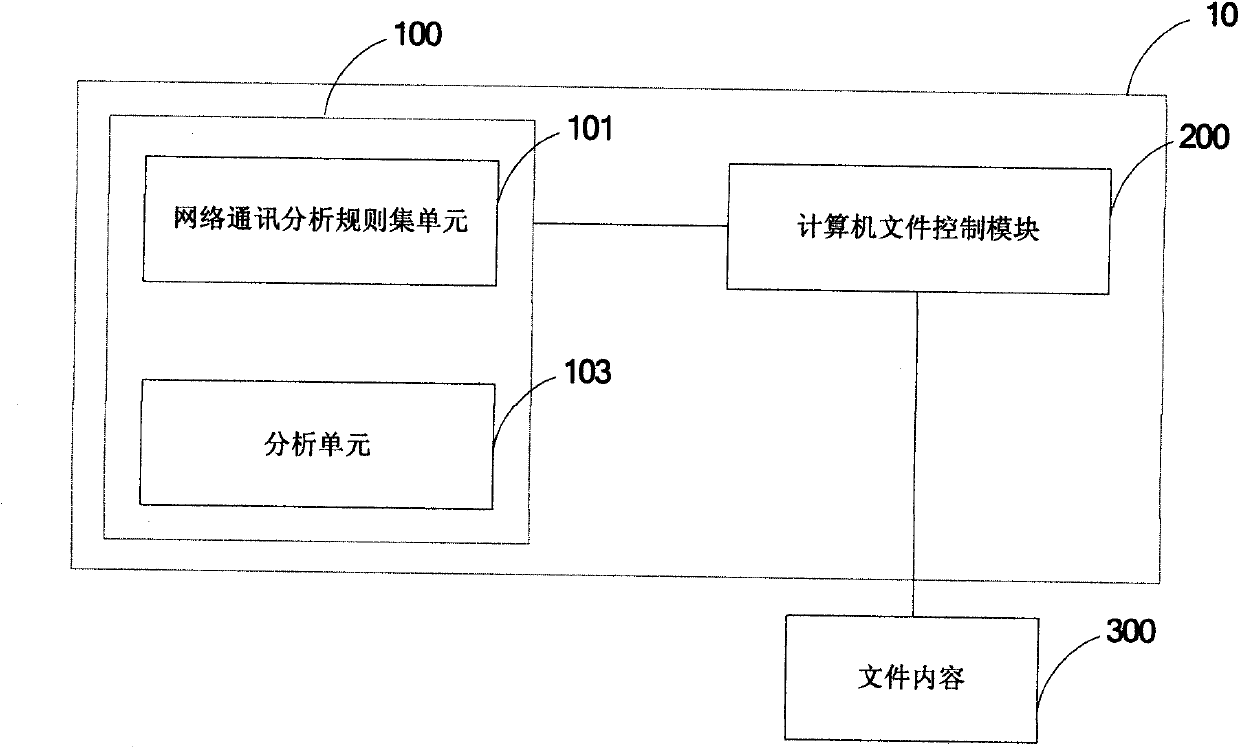
[0067] This embodiment is illustrated by a control system 10 for accessing computer file content by restricting access to file content 300 through a remote desktop network connection mode, and implementing the network communication analysis module 100 and the computer file control module 200 to run on the same on a terminal.
[0068] First, the user needs to set the network communication analysis rule set unit 101, and include the remote desktop network connection in the network communication exception rules. Here, the judgment of the remote desktop network connection can be based on the following characteristics: TCP protocol, TPKT protocol, COTP protocol, etc.; The network communication analysis module 100 and the computer file control module 200 run on the same terminal, so the setting of the target / source address (MAC) is manually set, and the terminal address (MAC) can be obtained through some software tools or other software techniques. ), and then recorded in the networ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com