A Virtualization-Based High-Availability System Design Method
A system design and virtualization technology, applied in the direction of platform integrity maintenance, etc., can solve the problems of system impact, reduce system performance, and restore available means relying on detection, etc., to achieve the effect of small performance loss, prevention of attacks, and improved availability.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment
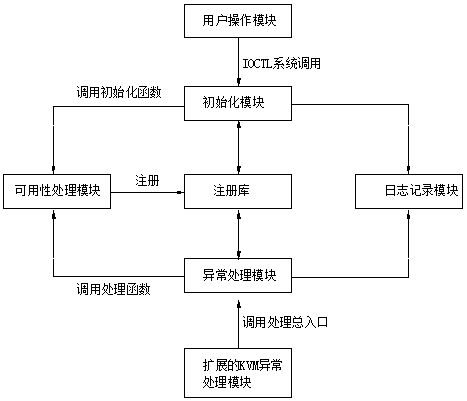
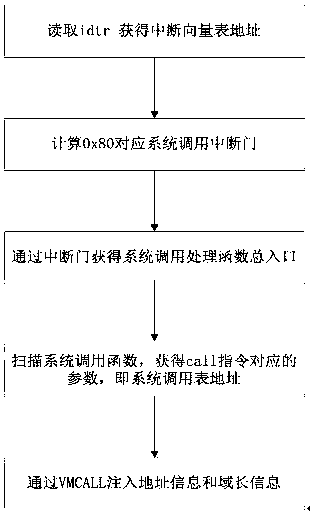
[0047] The following describes the process of realizing the architecture of the present invention with a specific embodiment:
[0048] Using the override process to hide, according to its realization principle, the purpose of hiding the process is realized by using the current terminal as a backdoor program;
[0049] First, echo $$ indicates the current process id. In the demonstration case, the current process id is 2573, and then in the / root / Desktop / ha / rk directory, it is rootkit override. After loading, switch to the / proc file system , through the ls command, you can see that the current process information 2573 can exist in the directory, and then create a new directory grid-hide-pid-2573 in the / dev directory. This process will trigger the chdir system call, and this system call will also be reset Orientation, the chdir system call will add the 2573 process information to the hidden queue, and hide the created directory at the same time, and then go to the / proc file sy...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com