Network transmission data virus detection processing method
A virus detection and network transmission technology, applied in transmission systems, digital transmission systems, data exchange networks, etc., can solve problems such as affecting normal network communication, difficult synchronization upgrades, and complex implementations, to solve performance expansion problems, simplify upgrades and Maintenance, coupling reduction effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
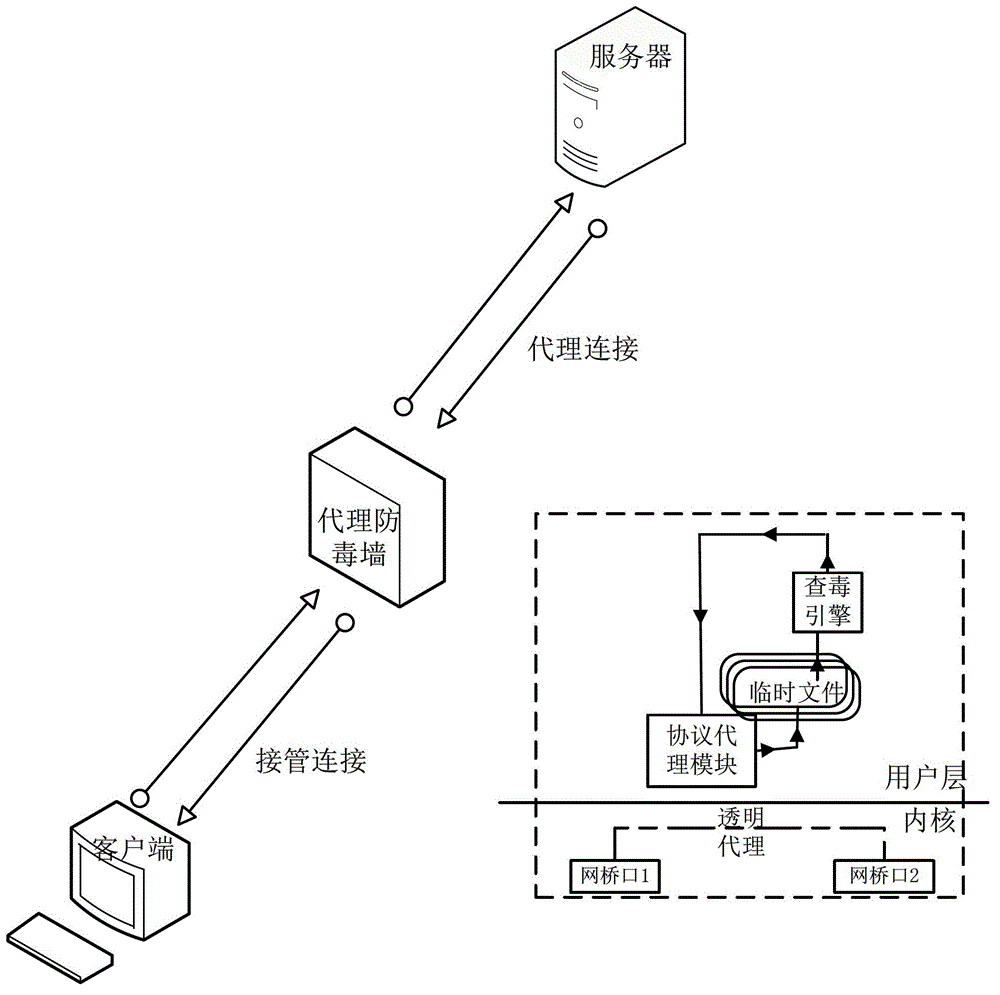
[0058] The specific implementation manner of the virus detection and processing method for network transmission data in the embodiment of the present invention will be described below with reference to the drawings in the description.
[0059] The embodiment of the present invention network transmission data virus detection processing method, comprises the following steps:
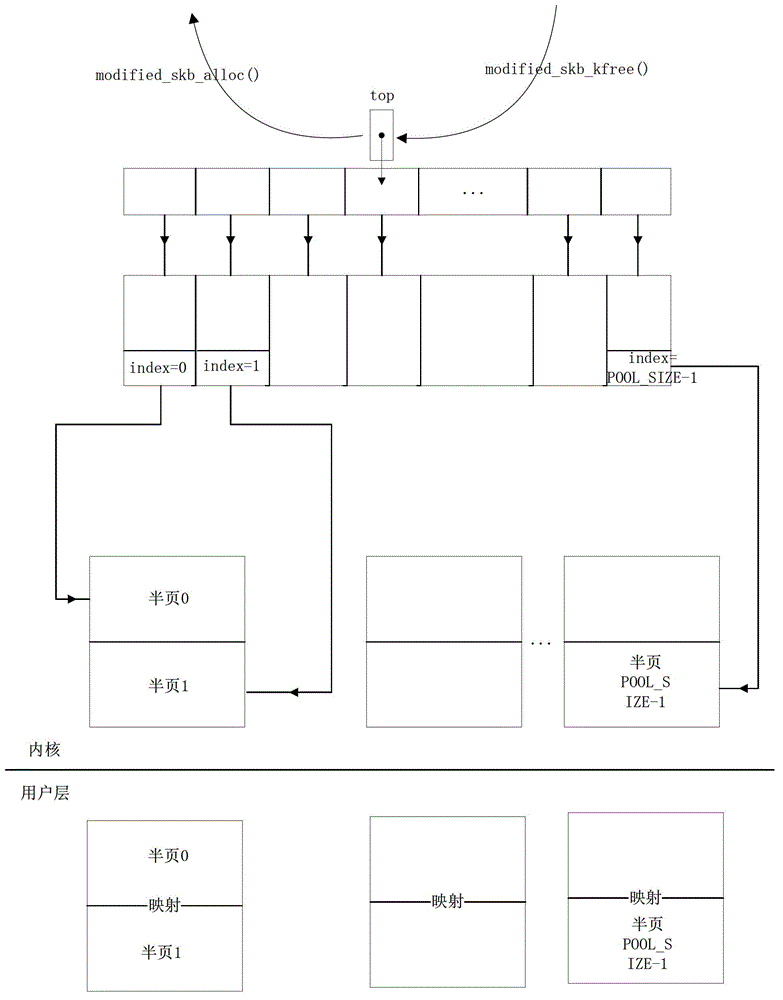
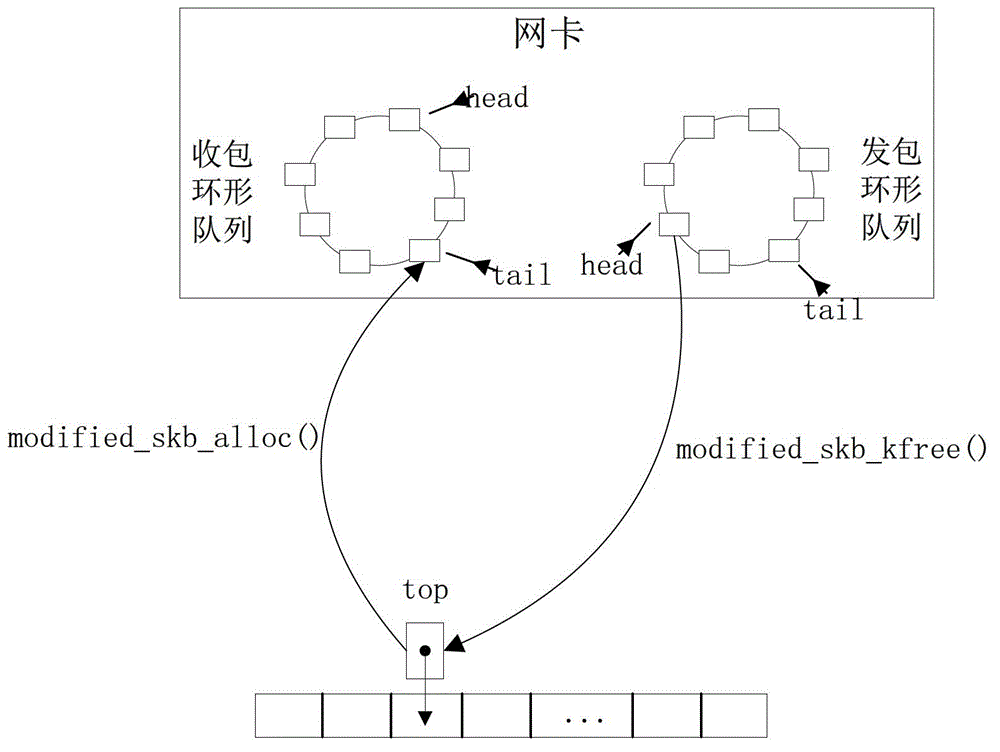
[0060] Step S100, set the resident memory of the preset size in the kernel layer of the network card as the zero-copy memory, and configure it as a stack allocation queue of the zero-copy sk_buff structure, and set the receiving memory corresponding to the index of the stack allocation queue at the kernel layer Queues and release queues are used to allocate and release sent and received data packets transmitted by the network.
[0061] Set a preset fixed-size resident memory in the kernel layer of the network card as zero-copy memory for allocation and release of the network card receiving queue.
[0062]...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com