Method and system of CCN trusted addressing based on DNS and extension protocol thereof
A technology for extending protocols and addressing methods, applied in the network field, can solve the problems of no proposed data management model, lack of boundary management of CCN, huge overhead, etc., to ensure scalability, alleviate huge overhead and delay, and ensure efficiency Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0048] The present invention will be further described below through specific embodiments and accompanying drawings.
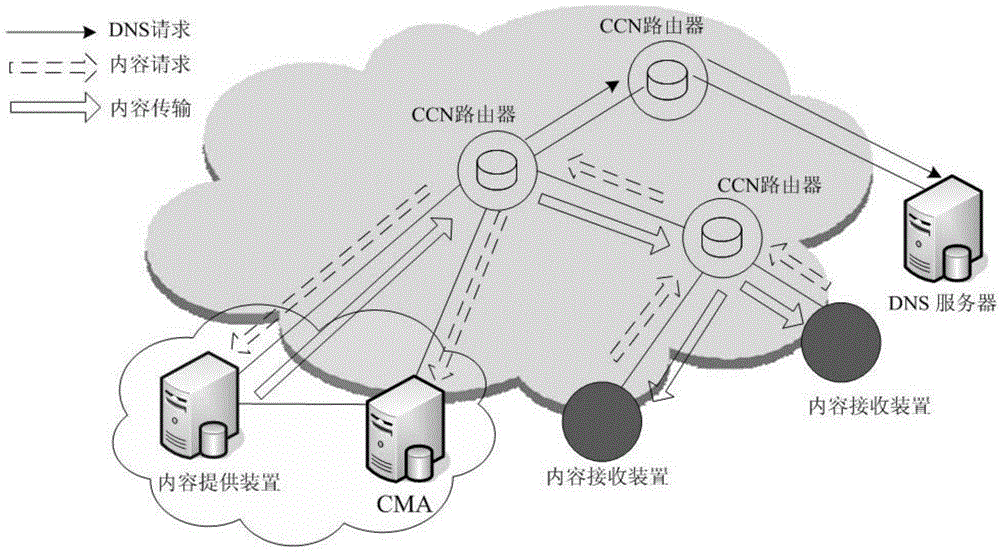
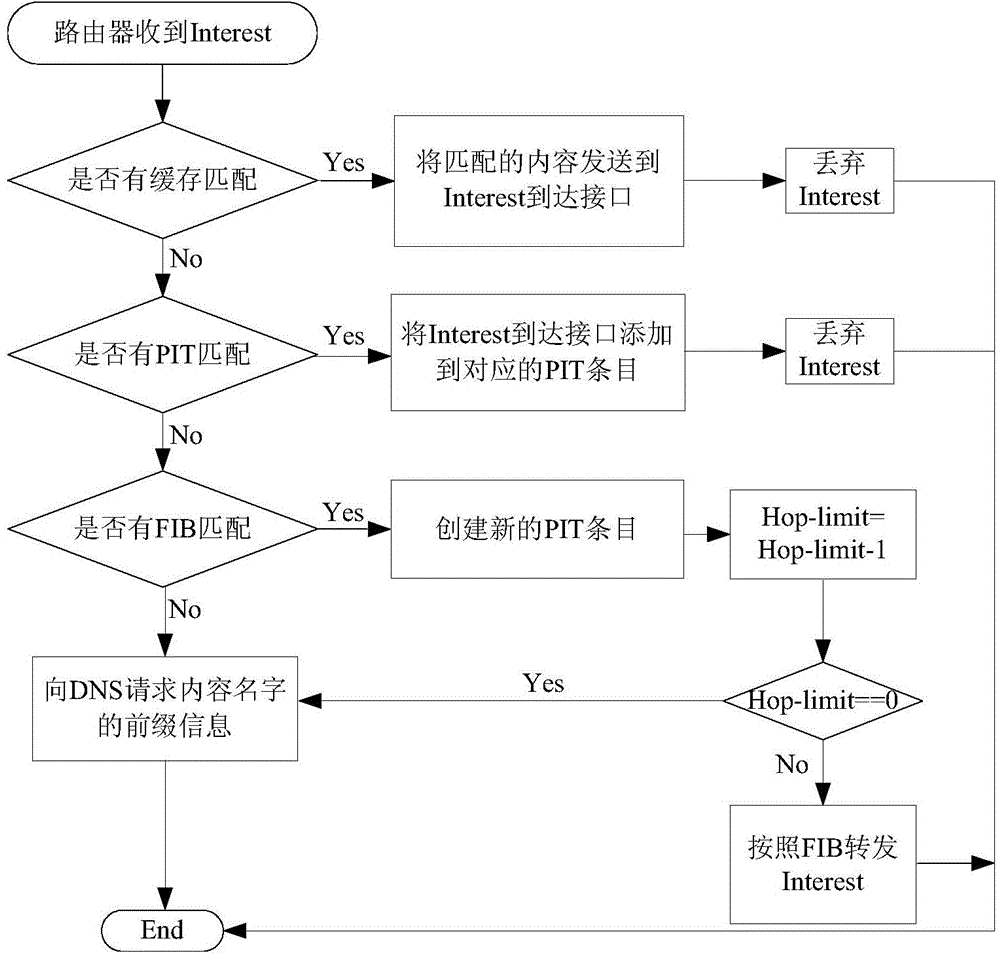
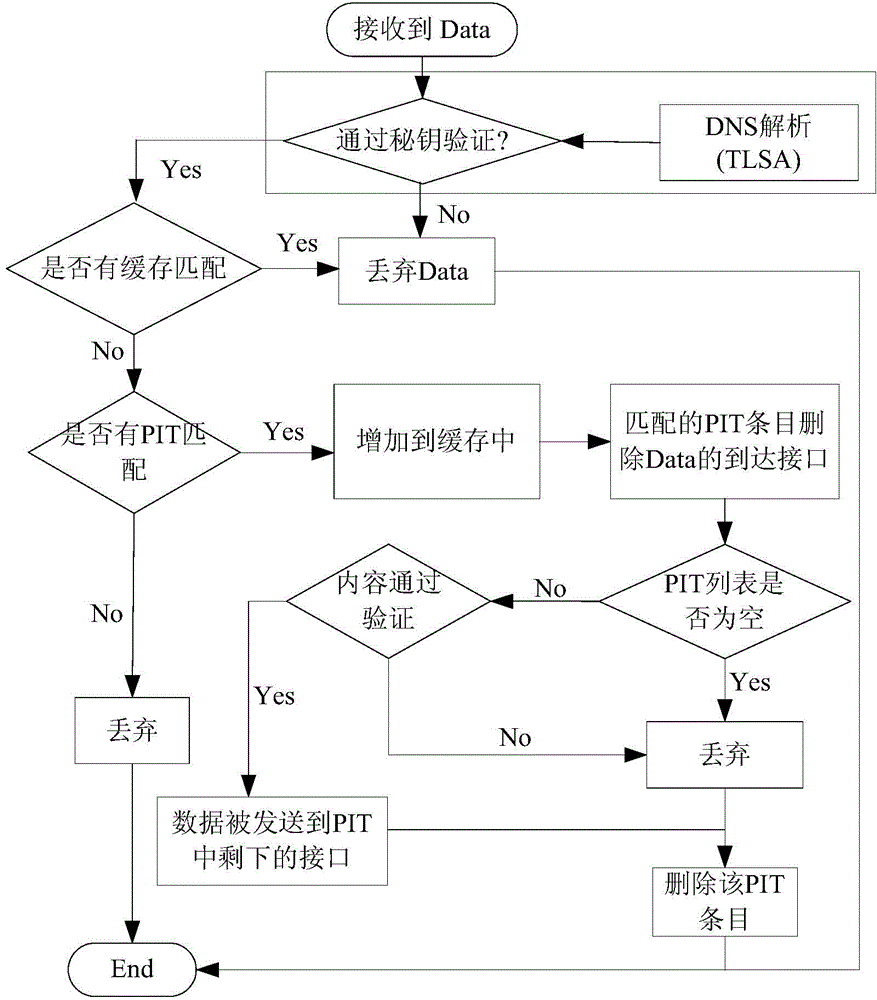
[0049] The region-based content management of the present invention can ensure the scalability of massive data management in the future. Each region deploys a content management anchor (Content Management Anchor, CMA), which is responsible for the location information of the source content in the region and the related information of the roaming source node. for maintenance. figure 1 It is a schematic diagram of the network architecture of the content management model in this embodiment. As shown in the figure, a content management anchor (CMA) is deployed in each content prefix area of the content-centric network, as a management node of a content area, for maintaining Information about the content and its corresponding source node location; the DNS server follows the hierarchical connection relationship of DNS in the current Internet, and is used to mainta...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com