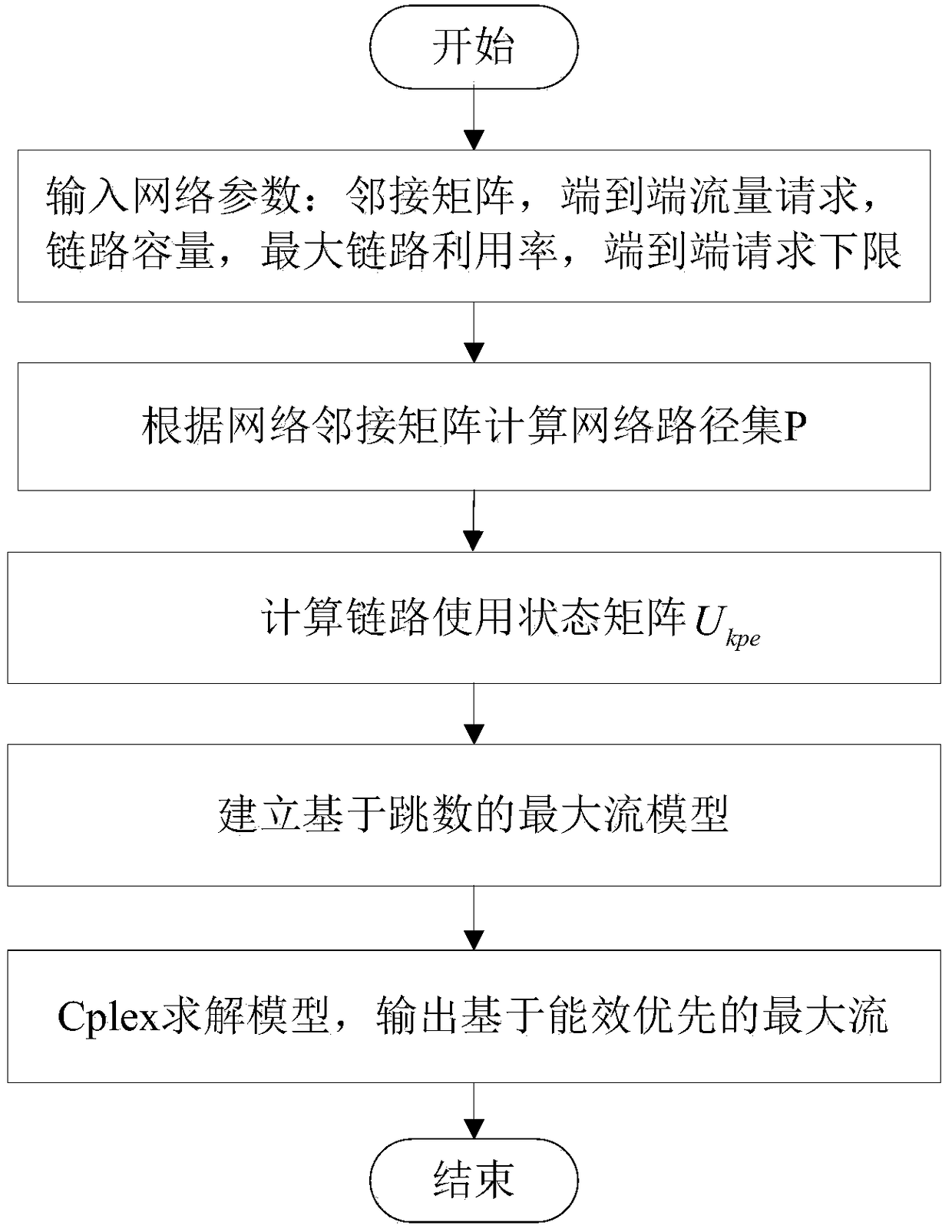
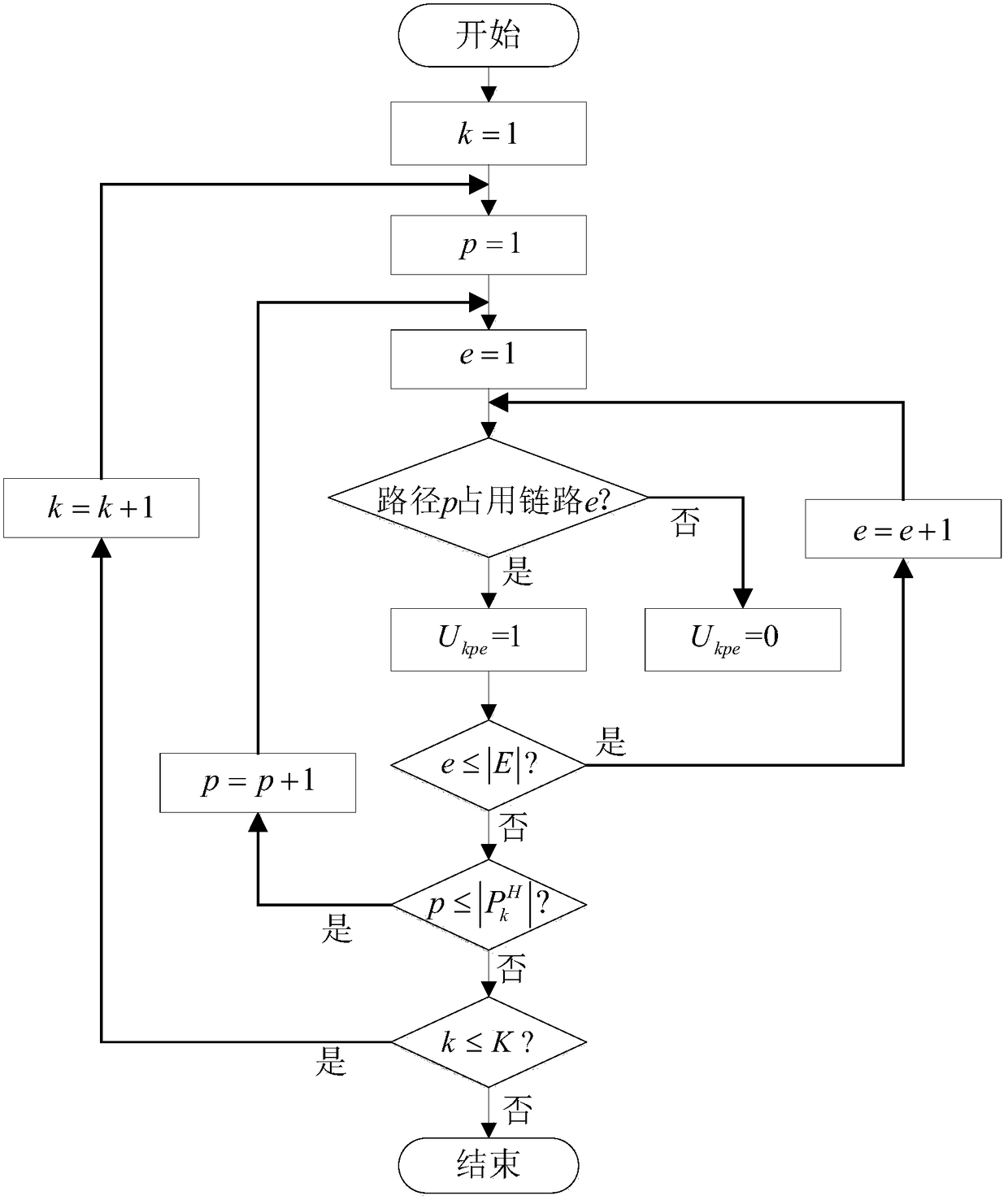
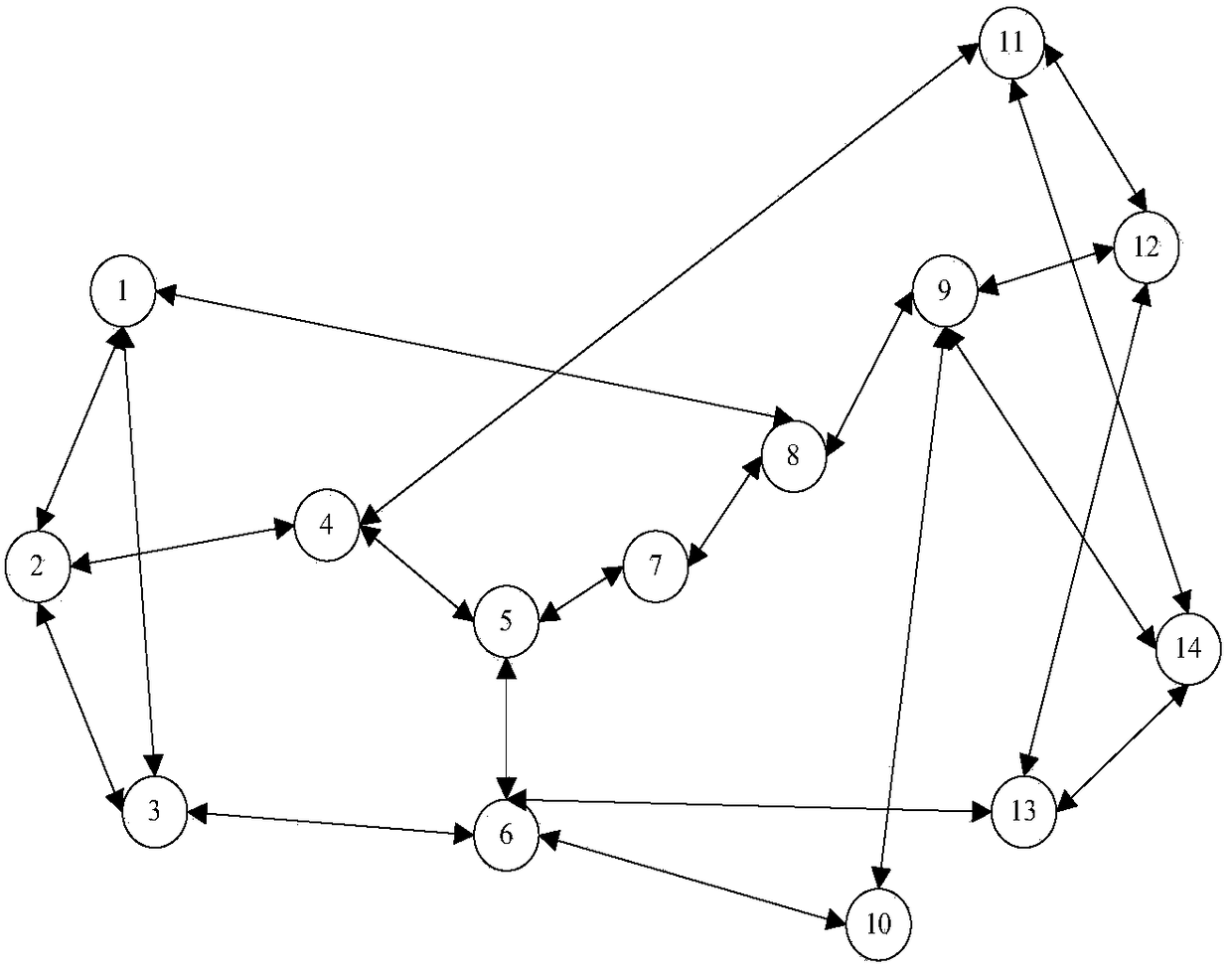
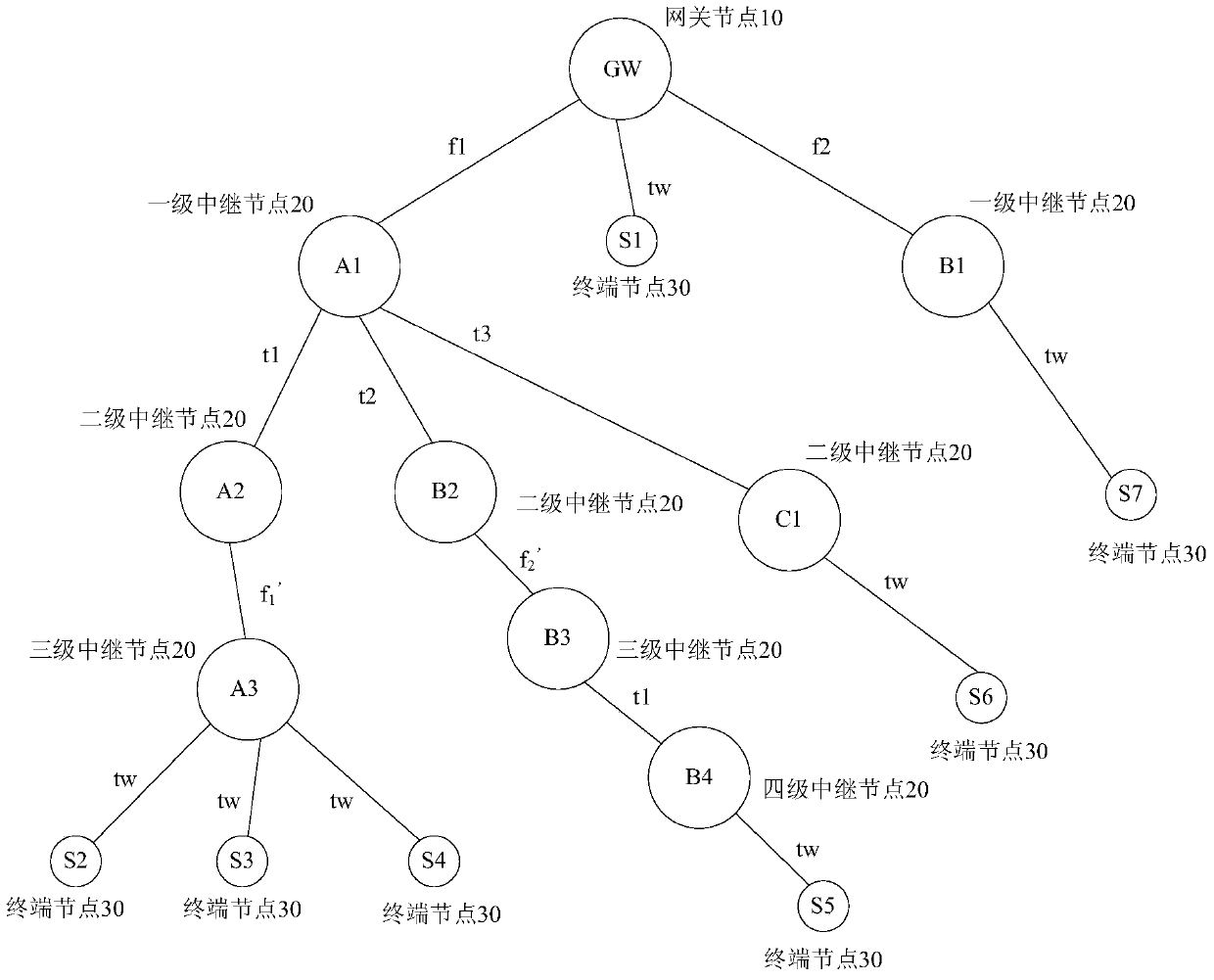
Patents
Literature
40 results about "Hop (networking)" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
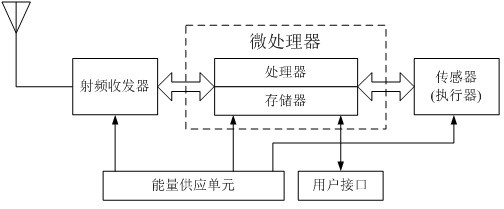
In computer networking, including the Internet, a hop occurs when a packet is passed from one network segment to the next. Data packets pass through routers as they travel between source and destination. The hop count refers to the number of intermediate devices through which data must pass between source and destination.
Popularity-based equilibrium distribution caching method for named data networking
InactiveCN104901980AReduce redundancyQuick responseData switching networksTraffic capacityNetwork packet
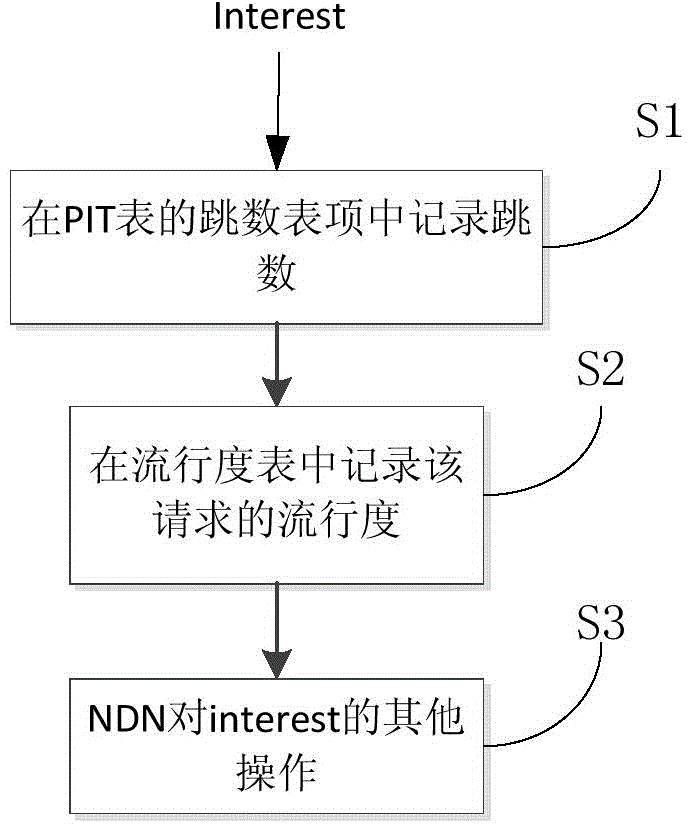
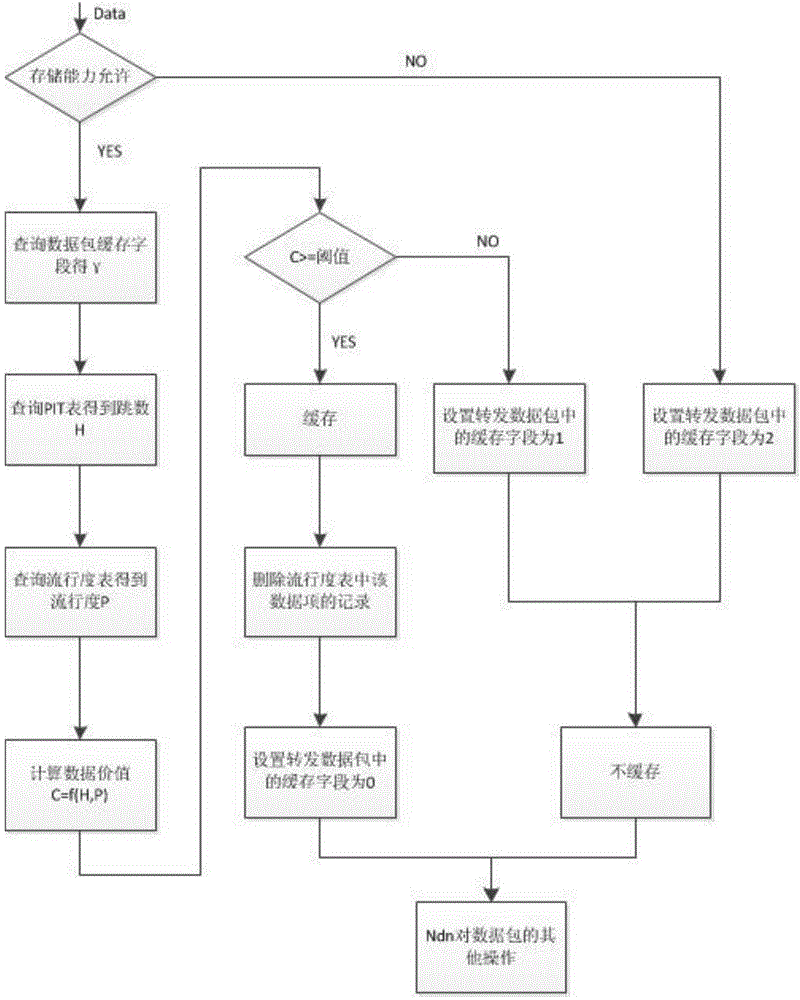
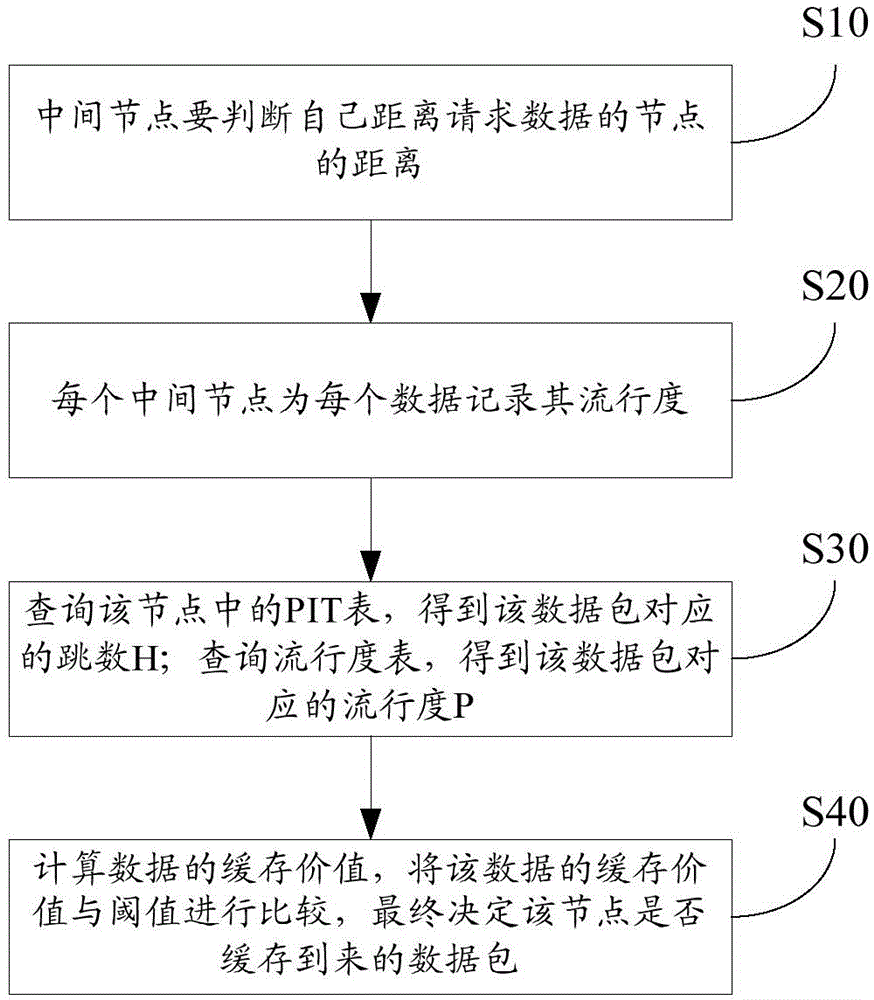
The invention provides a popularity-based equilibrium distribution caching method for named data networking and relates to the technical field of caching in named data networking. The method comprises the steps as follows: an intermediate node judging the distance between the intermediate node itself and a node of requested data; recording popularity for each data at each intermediate node; querying a PIT table in the node to obtain a hop count H corresponding to a data package; querying a popularity table to obtain popularity P corresponding to the data package; calculating the caching value of the data, comparing the caching value of the data with a threshold value, and finally determining whether to cache the arrived data package. The popularity-based equilibrium distribution caching method of the invention improves response speed and reduces network flow, simultaneously gives consideration to cache capacity of mobile nodes and reduces the redundancy degree of data in the network.
Owner:BEIJING UNIV OF TECH
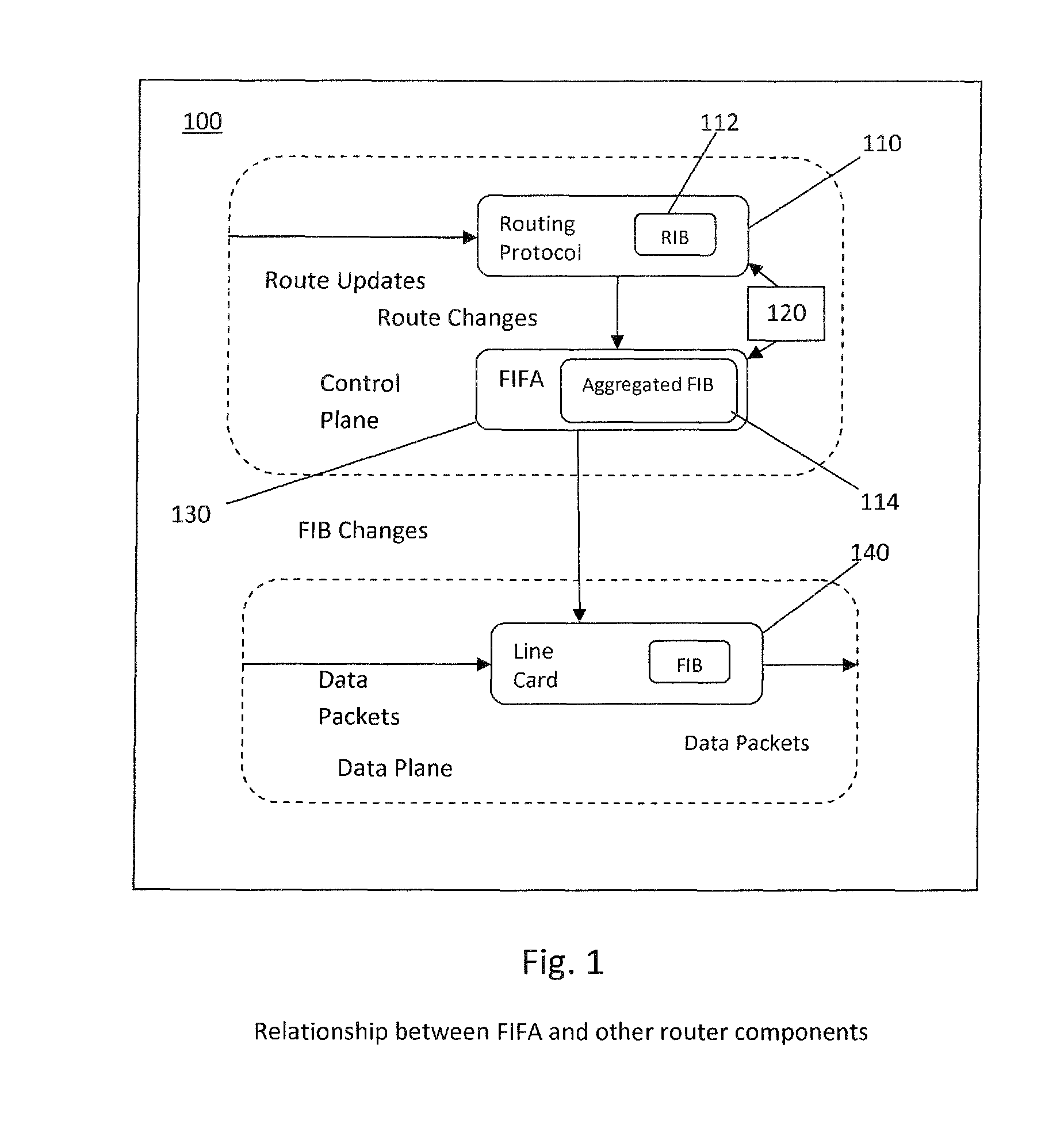
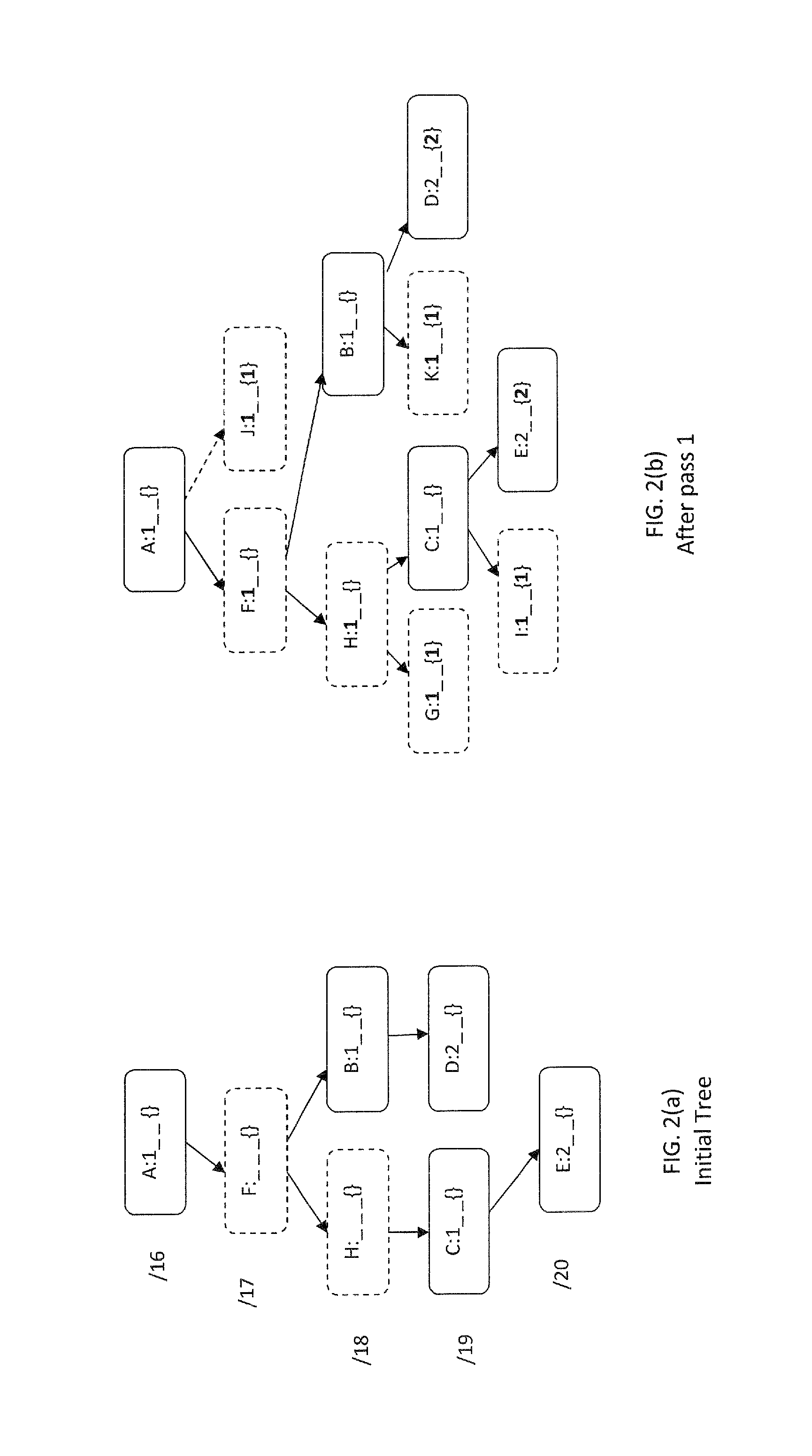
Devices and methods for forwarding information base aggregation
InactiveUS9491087B1Network can be highReducing table sizeData switching networksInformation repositoryBinary tree
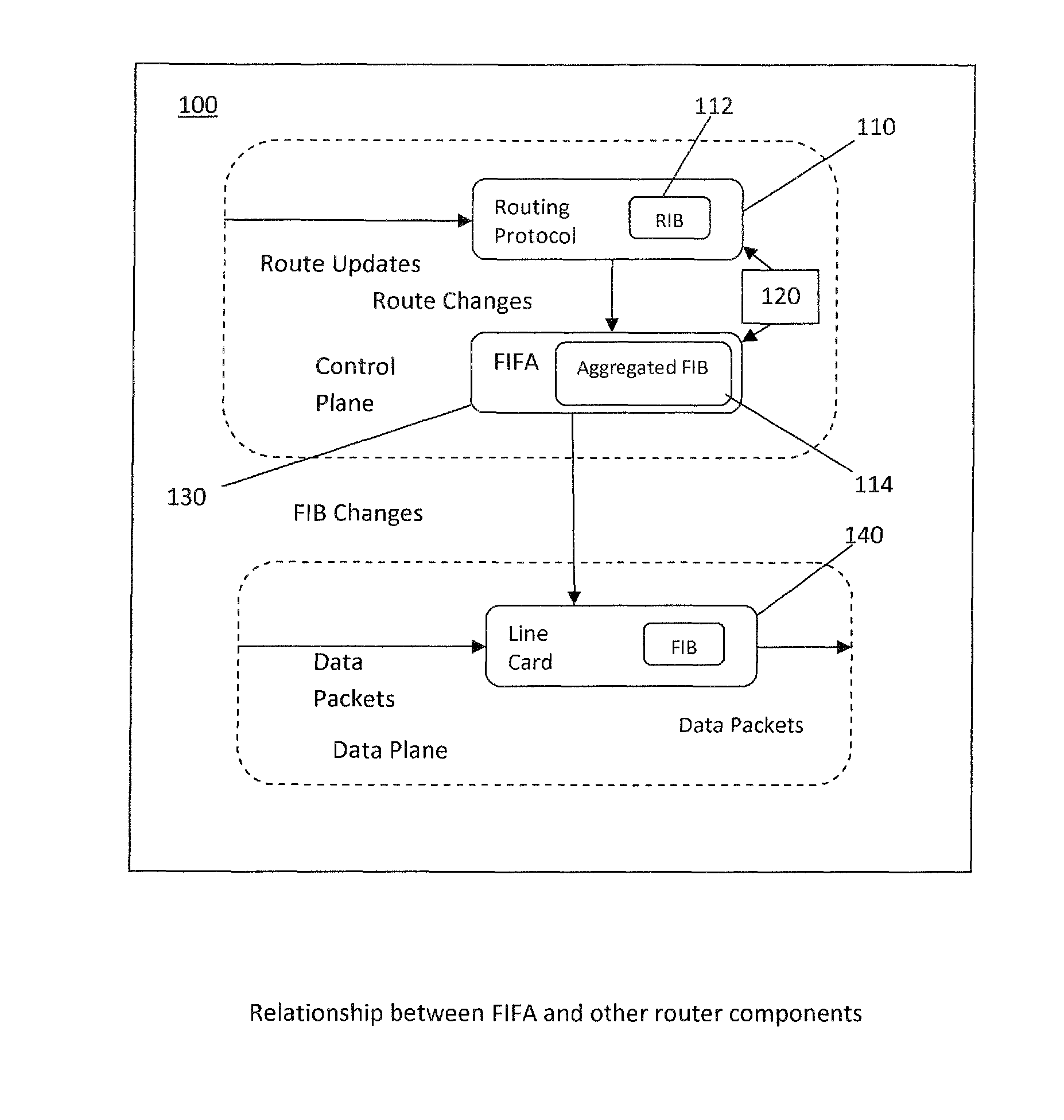
Networking devices and methods for forwarding information base (FIB) aggregation are provided. A networking device includes a processor operable to access entries in a FIB, and aggregate the FIB entries to produce an aggregated FIB with strong forward correctness. In aggregating the FIB entries, the processor is operable to: (a) associate the FIB entries with nodes (n) in a patricia trie; (b) traverse the patricia trie depth-first in post-order and determine for each node a next-hop set, without expanding the trie, by merging what would be the next-hop sets of its imaginary children nodes if there is a complete binary tree; and (c) traverse the patricia trie depth-first in pre-order, select for the root node a next-hop from its next-hop set and include the FIB entry associated with the root node in the aggregated FIB, for each node having a selected next-hop that appears in its child's next-hop set, select that next-hop for the child as its next-hop and exclude the FIB entry associated with the child node from the aggregated FIB, and for each child node which does not have in its next-hop set the selected next-hop of its parent, select a next-hop from its next-hop set and include the FIB entry associated with the child node in the aggregated FIB.
Owner:UNIVERSITY OF MEMPHIS RESEARCH FOUNDATION +1
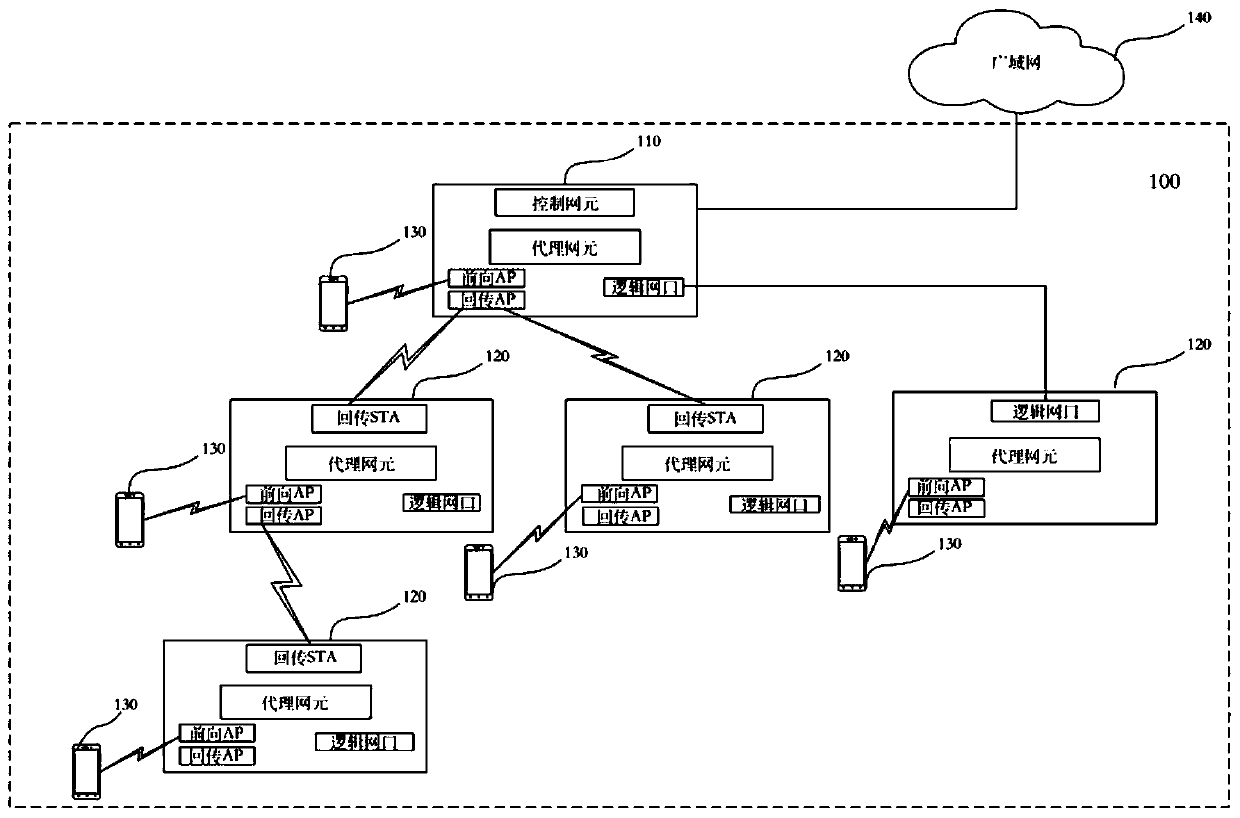
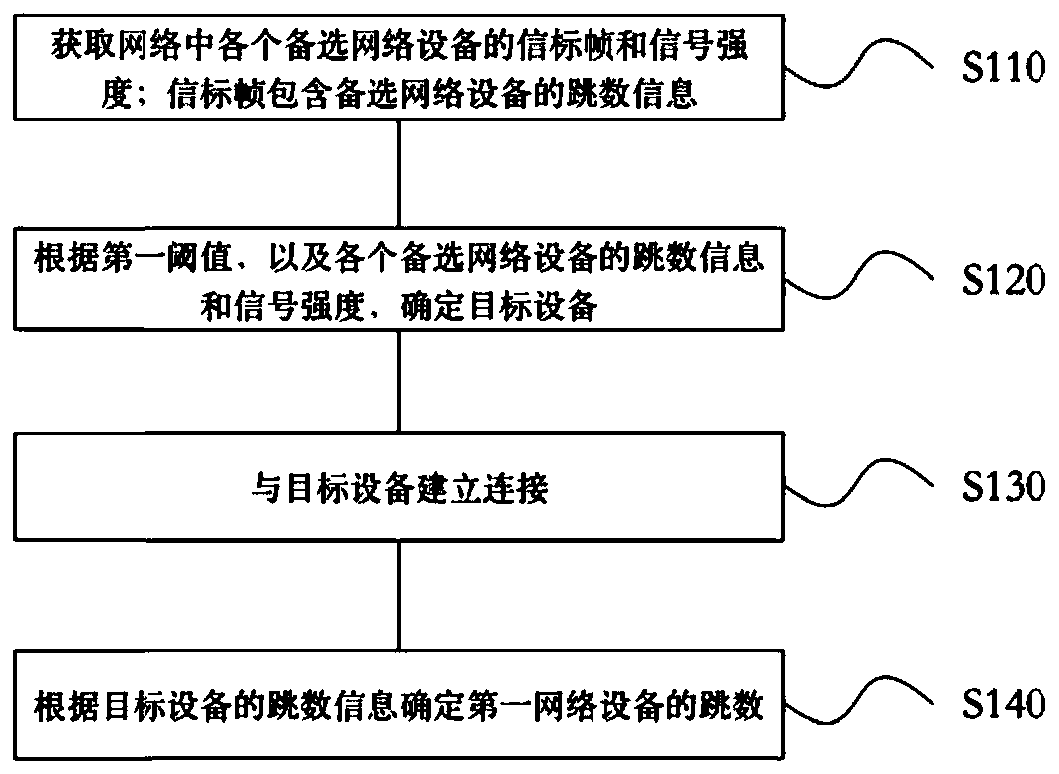
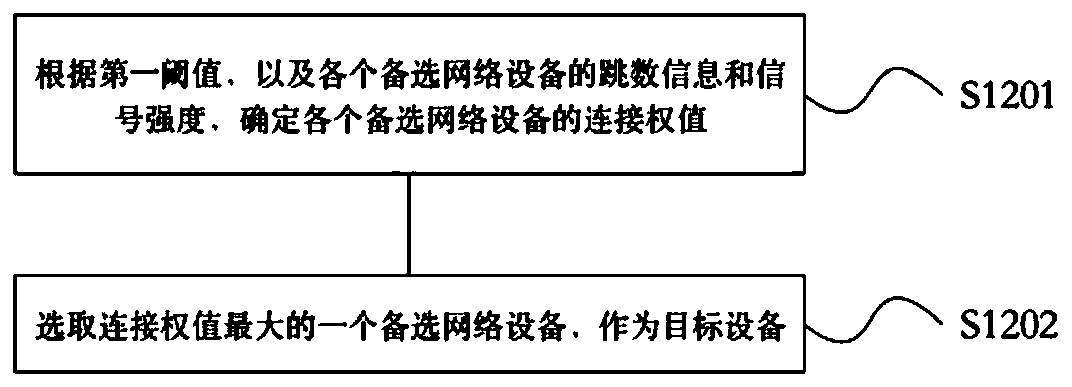
Backhaul station connection establishment method, network equipment and storage medium
The invention is applicable to the technical field of communication, and provides a backhaul station connection establishment method, which comprises the following steps: acquiring beacon frames and signal strength of each piece of alternative network equipment in a network; wherein the beacon frames comprise hop count information of the alternative network equipment; determining target equipmentaccording to a first threshold value and the hop count information and the signal intensity of each piece of alternative network equipment; establishing a connection with the target equipment; and determining the hop count of first network equipment according to the hop count information of the target equipment. The first network equipment determines whether to be connected with one of the alternative network equipment according to the hop count value in the beacon frame sent by the alternative network equipment and the signal intensity of the alternative network equipment. Because the factorsof the hop count and the signal intensity are considered at the same time, the networking convergence speed can be improved, and a loop is avoided.
Owner:SHENZHEN GONGJIN ELECTRONICS CO LTD
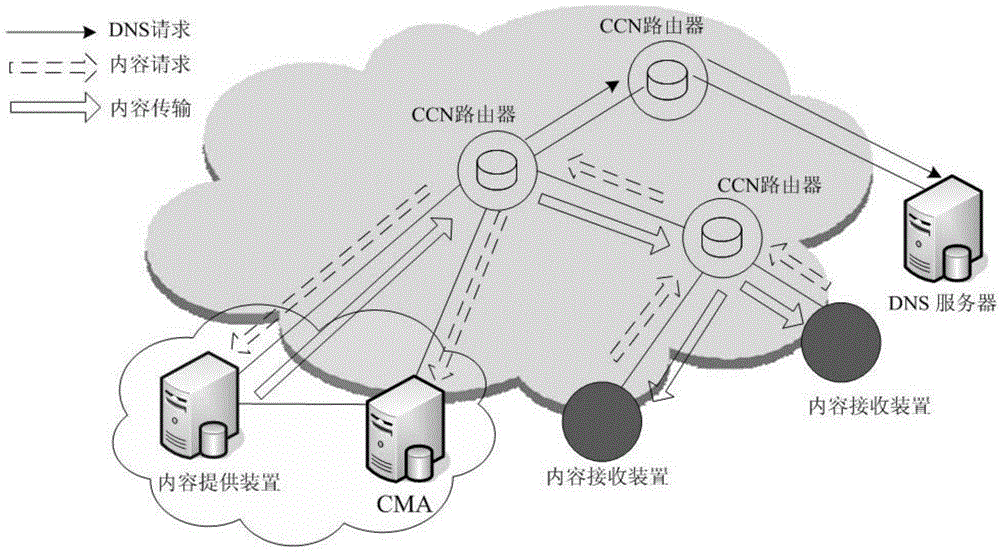
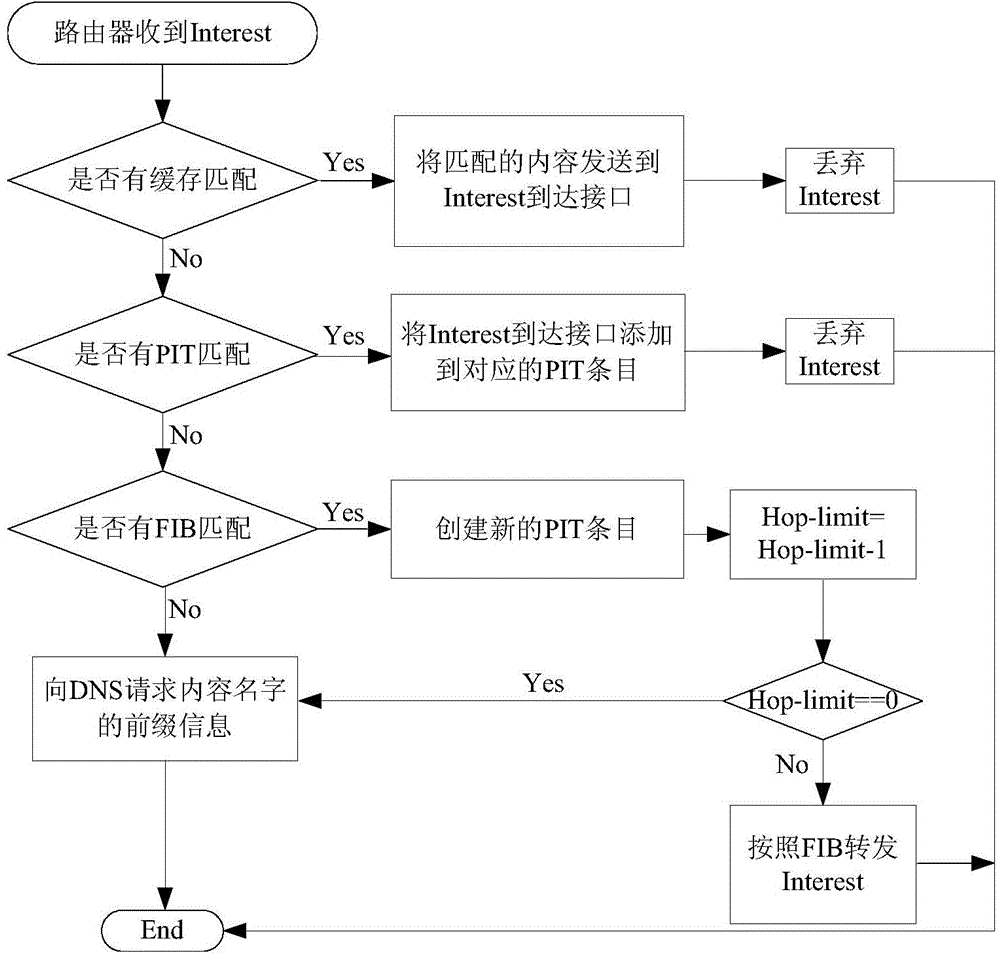
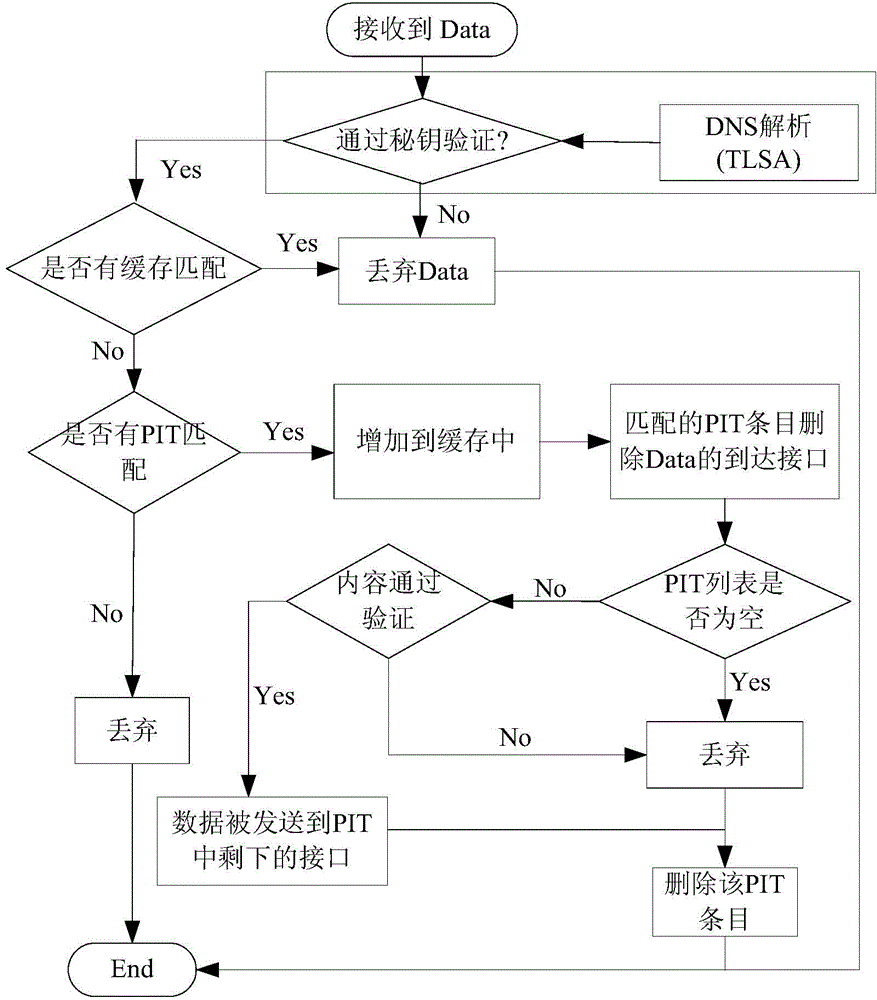
Method and system of CCN trusted addressing based on DNS and extension protocol thereof
ActiveCN104065760AGuaranteed acquisition efficiencyGuaranteed scalabilityUser identity/authority verificationEngineeringChain of trust
The invention relates to a method and a system of CCN (Content-Centric Networking) trusted addressing based on a DNS (Domain Name System) and an extension protocol thereof. The method comprises the steps of deploying content management anchor points in every regions of the content-centric networking (CCN) and registering the content management anchor points in the DNS based on the content prefixes of all the regions, next, carrying out addressing in a hop-by-hop addressing manner and a centralized DNS addressing manner in the content-centric networking, establishing a complete trust chain by virtue of a DNSSEC (Domain Name System Security Extensions) protocol to provide security guarantee in the name resolution process, providing public key information verification by virtue of a DANE (DNA-Based Authentication of Named Entities) protocol and then realizing trusted verification on contents and finally obtaining the desired contents. The method and the system have the advantages that the existing base facilities of the current internet are well combined and a data management model capable of supporting future mass services is provided, and especially for the deployment of the future CCN in the mobile internet, the dynamic content management can be effectively supported and the flexible and efficient mass content addressing process can be realized.
Owner:CHINA INTERNET NETWORK INFORMATION CENTER
Creation and transmission of part of protocol information corresponding to network packets or datalink frames separately
ActiveUS20080043737A1Network congestion can be reduced and avoidedImprove efficiencyData switching by path configurationElectric digital data processingData packOperational system
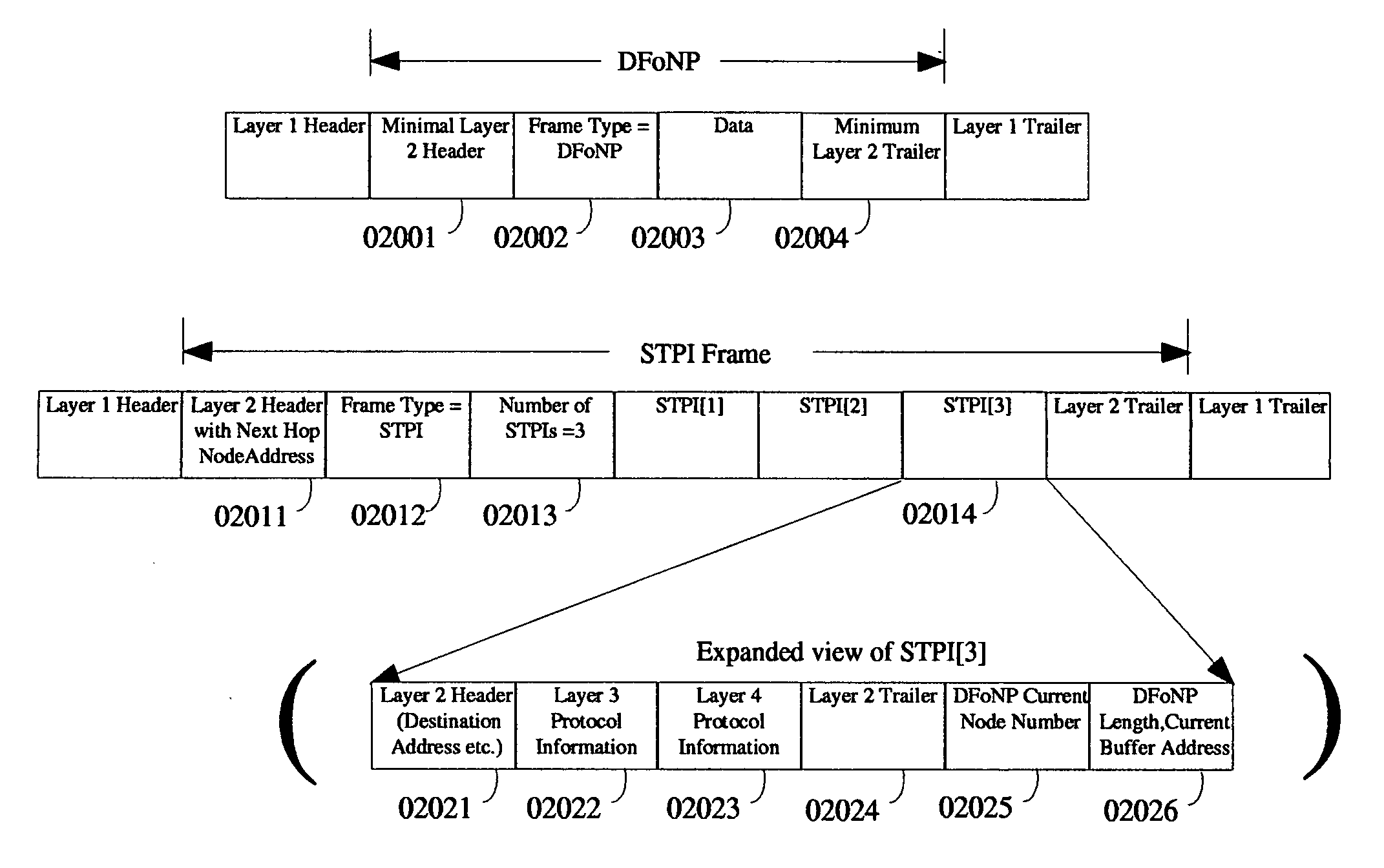
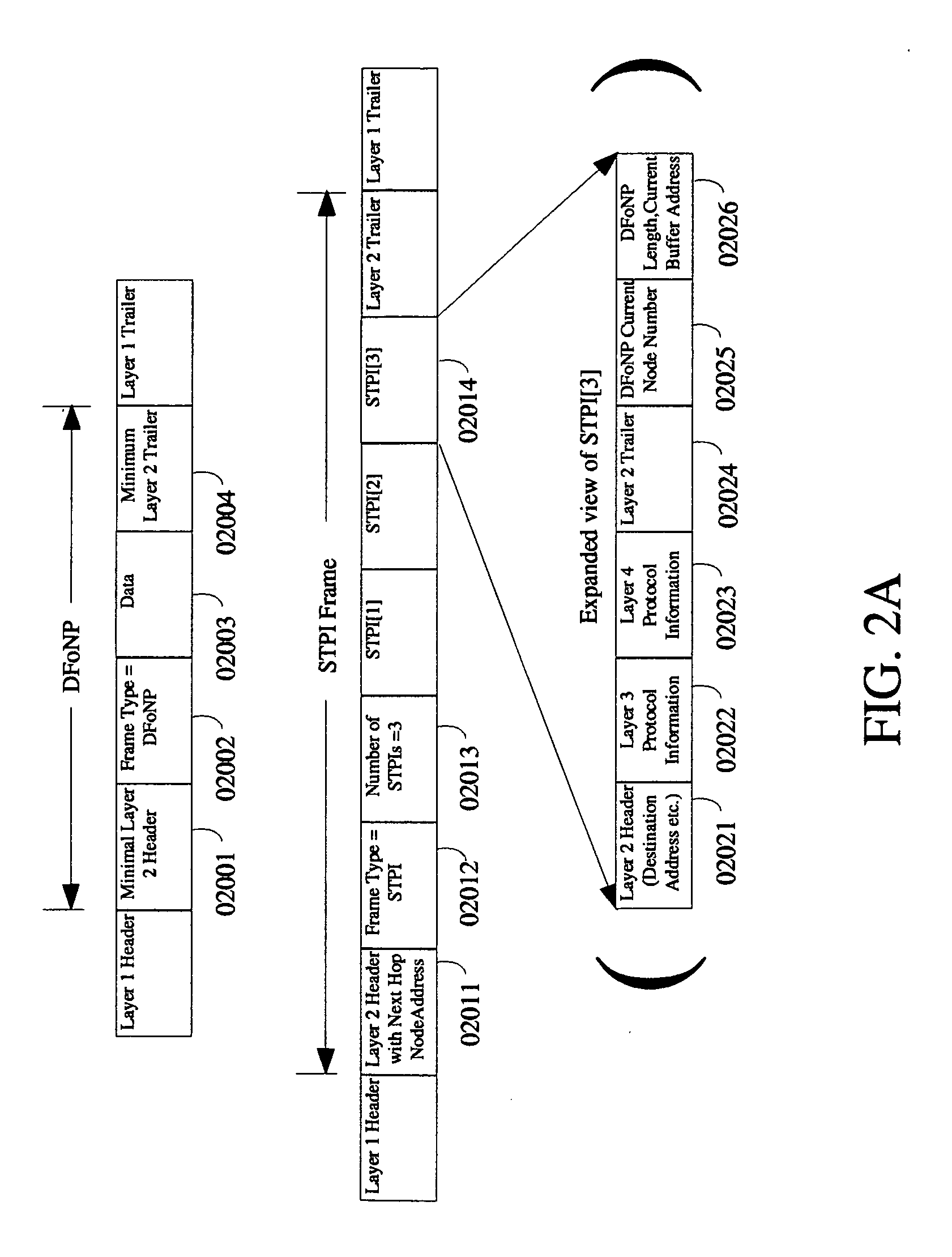
Datalink frames or networking packets contain protocol information in the header and optionally in the trailer of a frame or a packet. We are proposing a method in which part of or all of the protocol information corresponding to a frame or a packet is transmitted separately in another datalink frame. The “Separately Transmitted Protocol Information” is referred to as STPI. The STPI contains enough protocol information to identify the next hop node or port. STPI can be used avoid network congestion and improve link efficiency. Preferably, there will be one datalink frame or network packet corresponding to each STPI, containing the data and the rest of the protocol information and this frame / packet is referred to as DFoNP. The creation of STPI and DFoNP is done by the originator of the frame or packet such as an operating system.
Owner:GEORGE GEORGE MADATHILPARAMBIL +2
Seismic data transmission system based on UWB multi-hop network architecture
PendingCN110716229ALess likely to be disturbedShort pulse durationSeismic signal receiversSeismic signal transmissionData transmissionHop (networking)
The invention relates to a seismic data transmission system based on a UWB multi-hop network architecture. The system comprises three parts of a UWB seismic acquisition station acquisition system, a multi-hop networking system and a data center supervision system. The UWB seismic acquisition station acquisition system is used for acquiring seismic information; the collected seismic information issent to the data center supervision system through the multi-hop networking system, the multi-hop networking system is based on an ultra-wideband technology and adopts a network architecture with peer-to-peer network serial access, the link benefit is maximized by using an improved AODV routing algorithm, the collected information can be transmitted to the data center supervision system in the most efficient manner, and the data center supervision system is used for recovering and processing data in real time and monitoring the whole network system in real time. The system has the outstandingcharacteristics of low power consumption, real-time data recovery, wide monitoring range, labor saving and the like.
Owner:JILIN UNIV
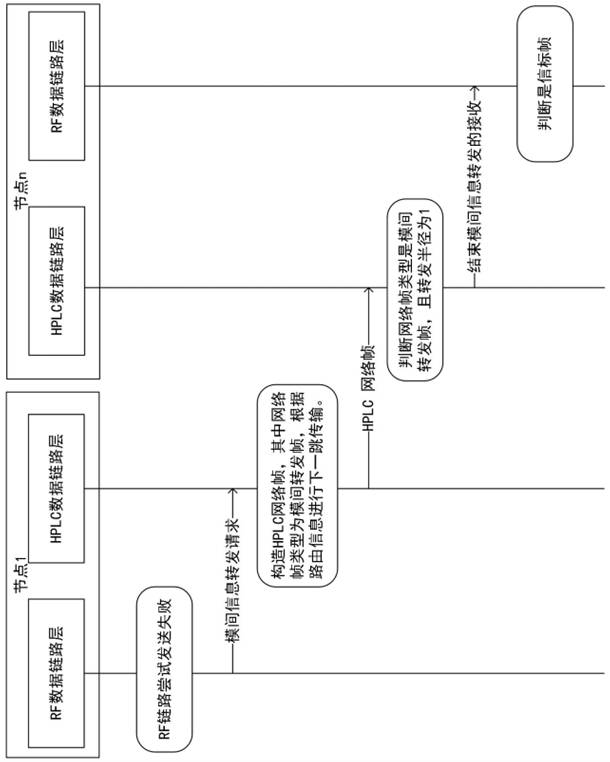
Dual-mode inter-mode cooperation method and electric Internet of Things system
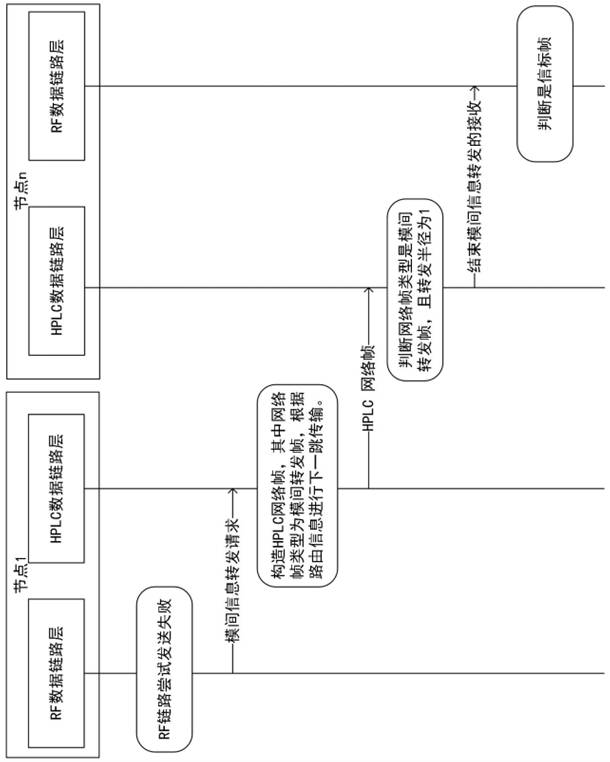
The invention provides a dual-mode inter-mode cooperation method and an electric Internet of Things system, and belongs to the field of electric Internet of Things wireless communication. The method comprises the steps that if a mode A of a sending node is disconnected through communication of a link A, the sending node performs inter-mode cooperation, requests a mode B of the sending node to construct a network frame and forwards the network frame through a link B, wherein the type of the network frame is an inter-mode forwarding frame; and after a receiving node receives the inter-mode forwarding frame through the mode B, inter-mode cooperation is carried out, and the inter-mode forwarding frame is sent to the mode A of the receiving node, so that the mode A of the receiving node obtains communication data. According to the method, a collaborative networking function is provided, inter-mode beacon frame and networking command frame forwarding is realized, and the network networking reliability is improved; and a single-hop service transmission path backup and a selection function is provided, data frame and command frame forwarding between single-hop modes is realized, and the network data transmission reliability is improved.
Owner:BEIJING SMARTCHIP MICROELECTRONICS TECH COMPANY +3
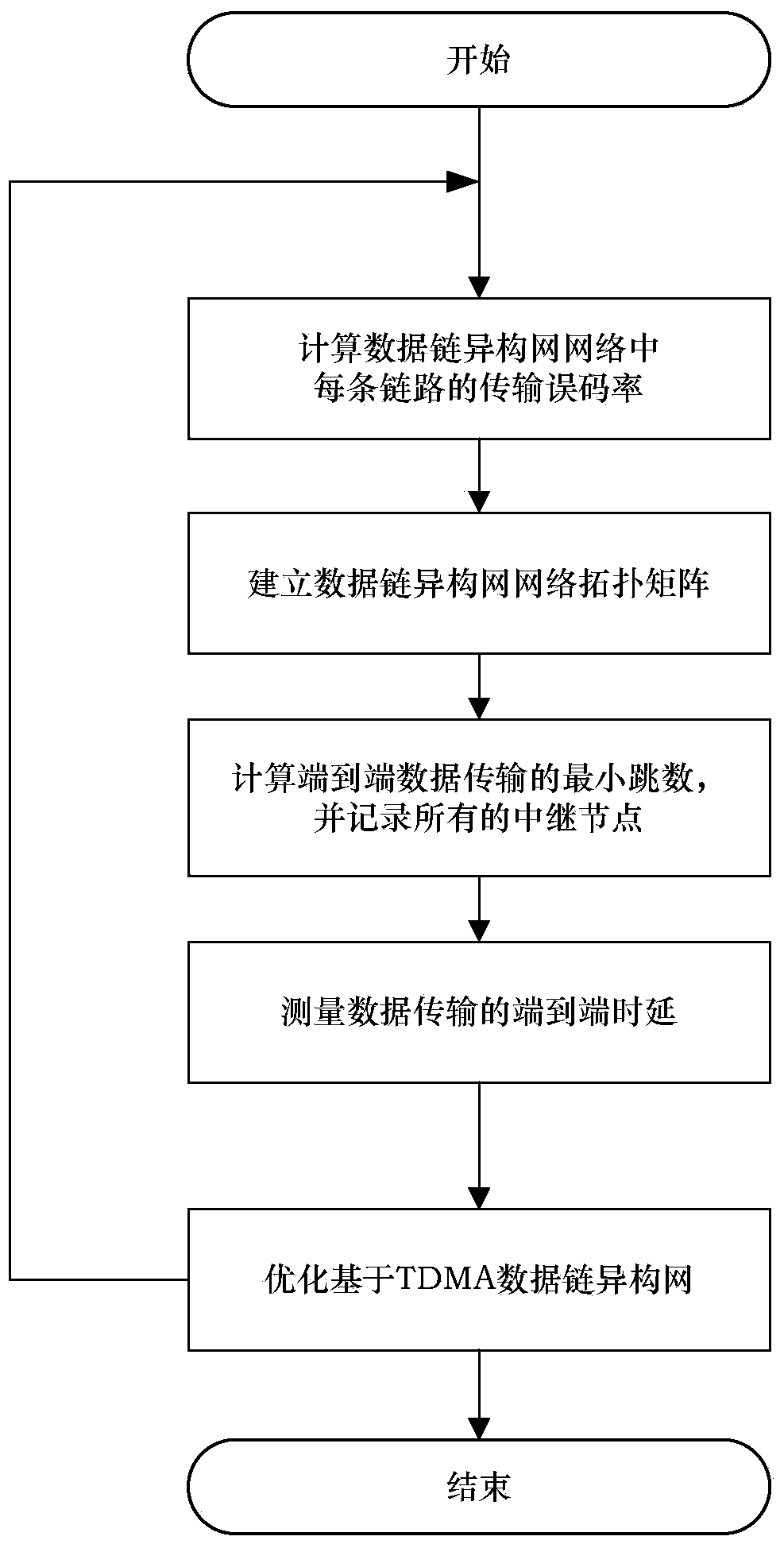
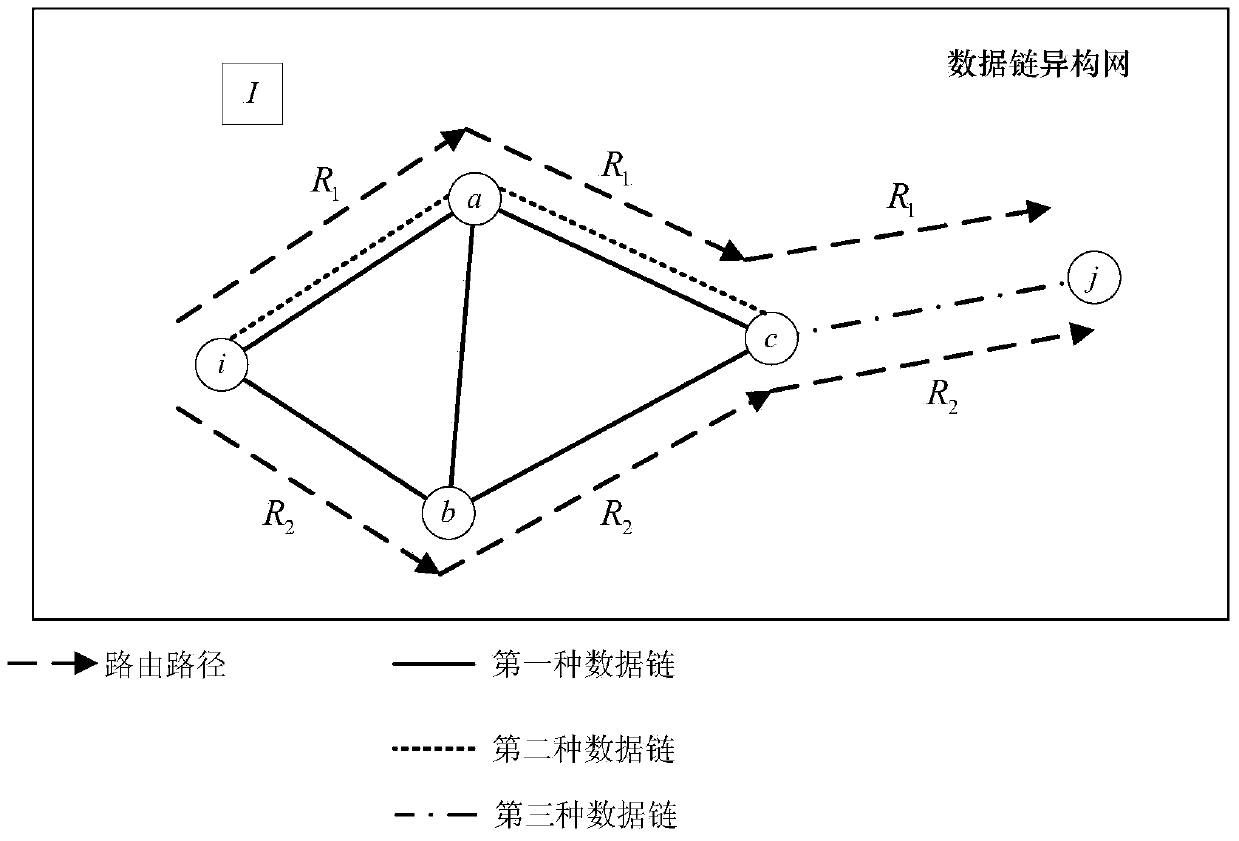
Method for measuring and optimizing end-to-end delay based on TDMA (time division multiple address) data link heterogeneous network
ActiveCN103402219AAccurate end-to-end delayImprove design efficiencyWireless communicationTrunkingEngineering
The invention discloses a method for measuring and optimizing end-to-end delay based on a TDMA (time division multiple address) data link heterogeneous network. The method comprises the steps of calculating the transmission bit error rate of each link, establishing and superposing single data link network topology matrixes of each type of the data links to acquire a network topology matrix of the data link heterogeneous network, calculating the minimum hop count of end-to-end data transmission and recording all relay nodes, measuring the end-to-end delay generated by the data transmission, and optimizing the data link heterogeneous network. The method disclosed by the invention gives full consideration to influences imposed on the end-to-end delay of the TDMA data link heterogeneous network by channels, links and networking in the data transmission process, thereby not only being capable of acquiring more accurate end-to-end delay, but also reducing the design cost of the data link heterogeneous network, and optimizing the network performance in the design stage.
Owner:BEIHANG UNIV
Next hop determining method and device
InactiveCN106506367AAvoid long-term traffic interruptionsEasy to chooseData switching networksComputer networkReal-time computing
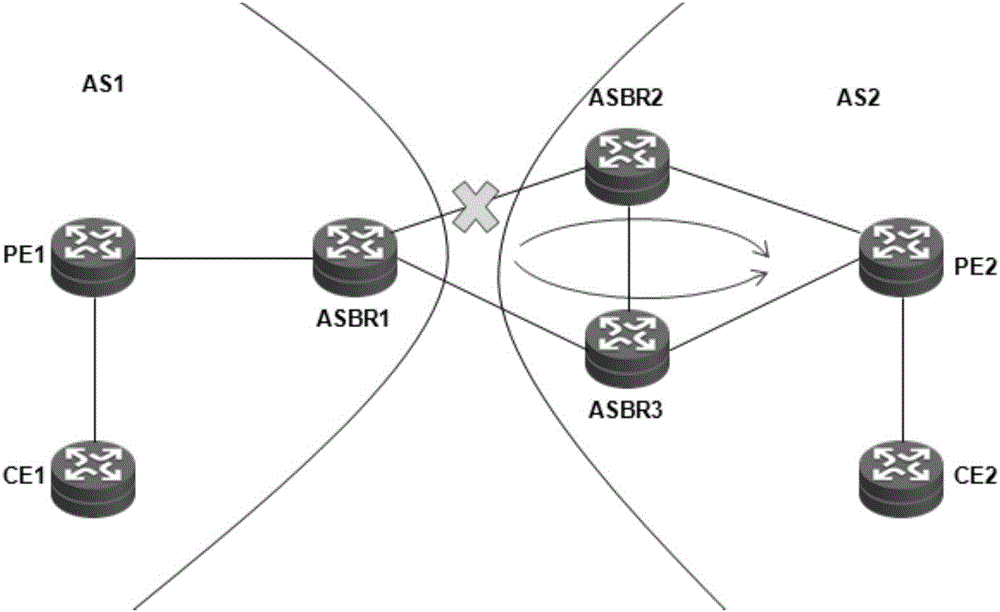
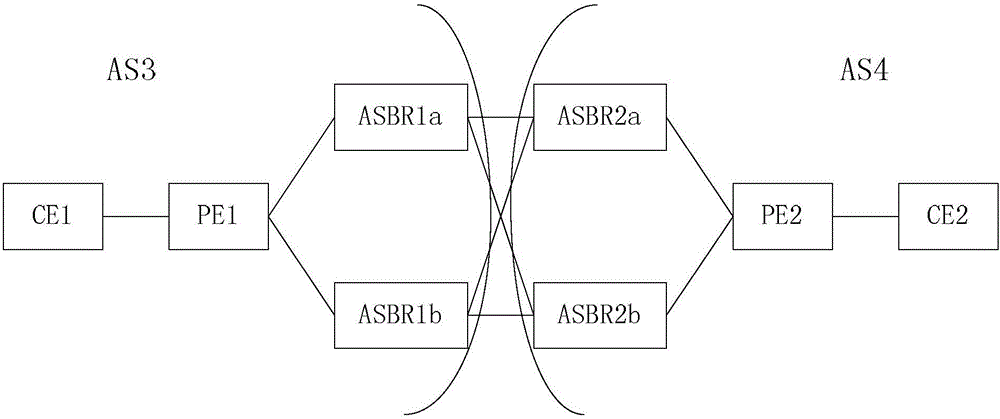
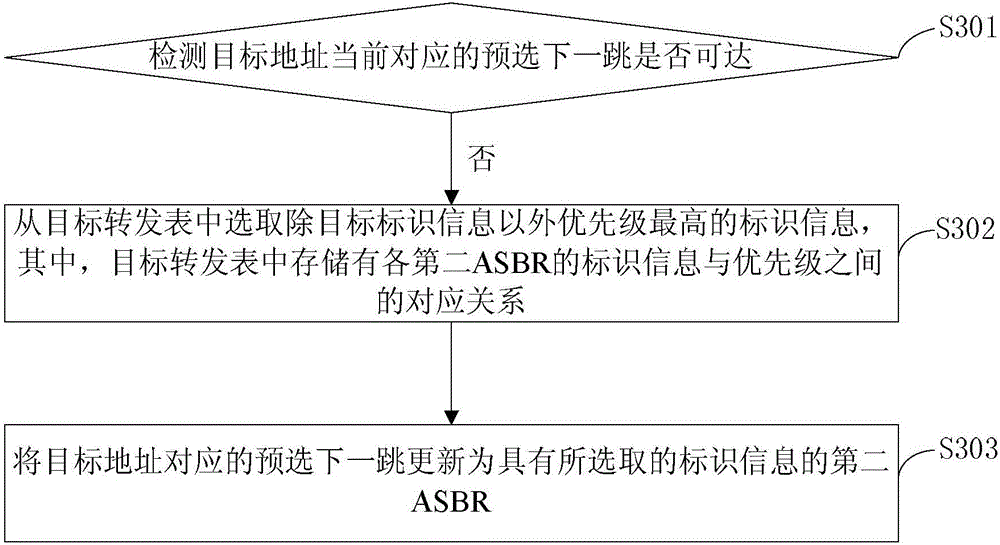
The embodiment of the invention provides a next hop determining method and device. The method is applied to a first ASBR in a first autonomous system. A first autonomous system and a second autonomous system carry out cross-domain networking in an Option B mode. The second autonomous system comprises at least two second ASBRs. The method comprises the steps of detecting whether a preselection next hop currently corresponding to a target address is reachable or not, wherein the target address is the address of a target CE in the second autonomous system, the preselection next hop is the second ASBR with target identification information in a target forwarding table, and the target forwarding table is the forwarding table which is stored by the first ASBR and corresponds to the target address; if the preselection next hop is unreachable, selecting the identification information with the highest priority except the target identification information from the target forwarding table, wherein corresponding relationships between the identification information and the priorities are stored in the target forwarding table; and updating the preselection next hop corresponding to the target address to be the second ASBR with the selected identification information. Visibly, according to the scheme, the condition that traffic is interrupted for a long time among the autonomous systems which carry out cross-domain networking in the Option B mode can be avoided well.
Owner:NEW H3C TECH CO LTD
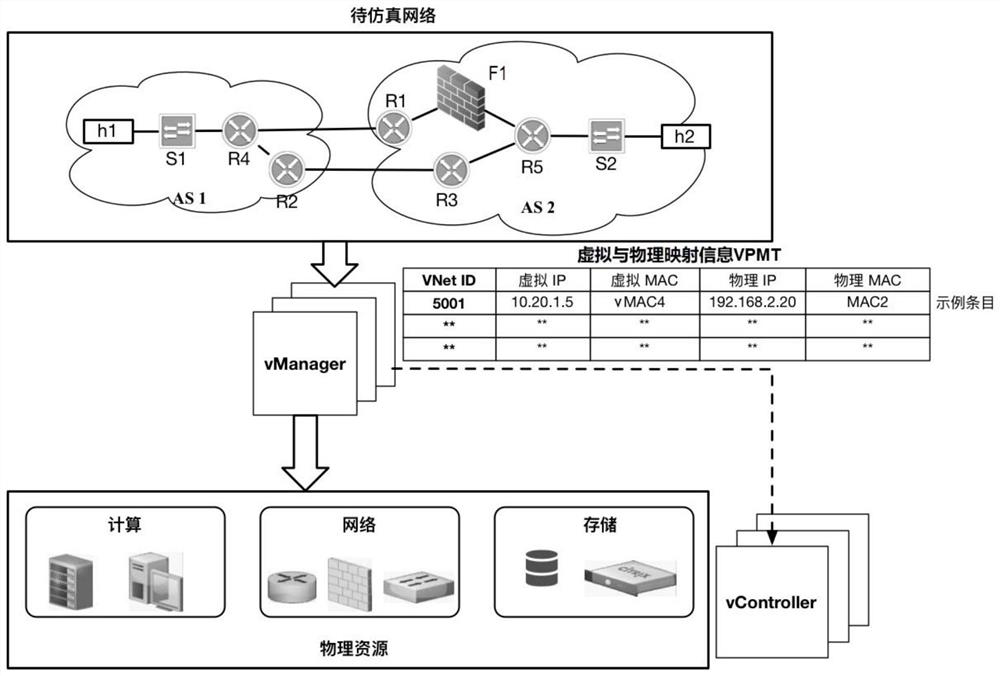
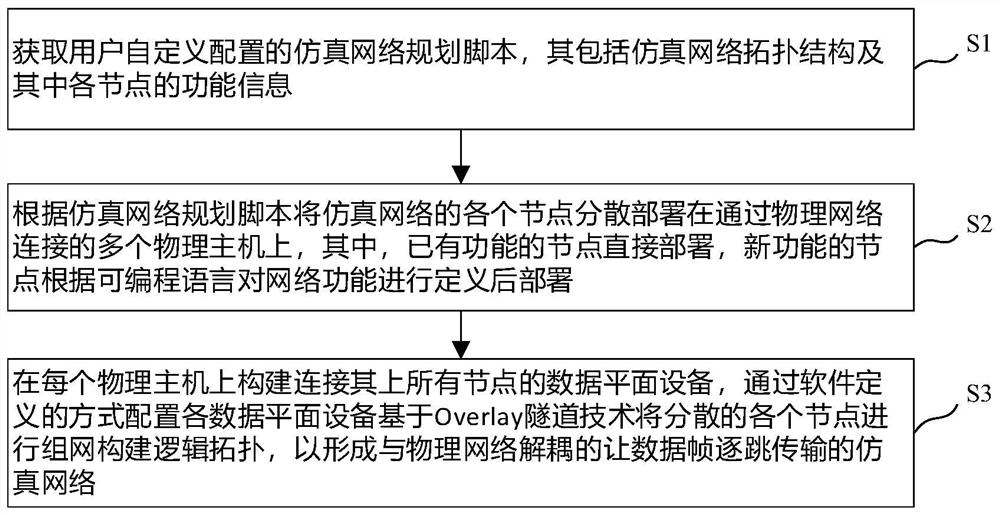
Method for constructing virtual-real decoupling simulation network
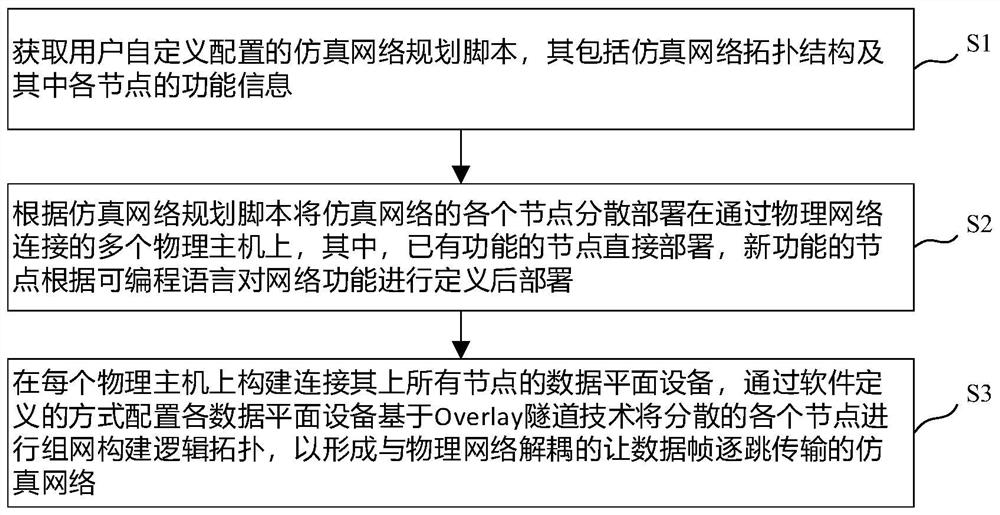
The embodiment of the invention provides a method for constructing a virtual-real decoupling simulation network, and the method comprises the steps: S1, obtaining a simulation network planning scriptwhich is configured in a user-defined manner and comprises a simulation network topological structure and the function information of each node in the simulation network topological structure; S2, according to the simulation network planning script, dispersing and deploying each node of the simulation network on a plurality of physical hosts connected through a physical network; and S3, constructing data plane equipment connected with all nodes on each physical host on each physical host, wherein each data plane equipment is configured in a software definition mode to perform networking on each dispersed node based on an Overlay tunnel technology to construct a logic topology so as to form a simulation network which is decoupled with the physical network and enables data frames to be transmitted hop by hop. According to the method, the construction process is completely transparent to the physical network cluster, and any virtual-real decoupling simulation network topology structure can be constructed without relying on or changing networking and configuration of the physical network cluster.
Owner:INST OF COMPUTING TECH CHINESE ACAD OF SCI
Internet-of-Things communication system and construction method thereof
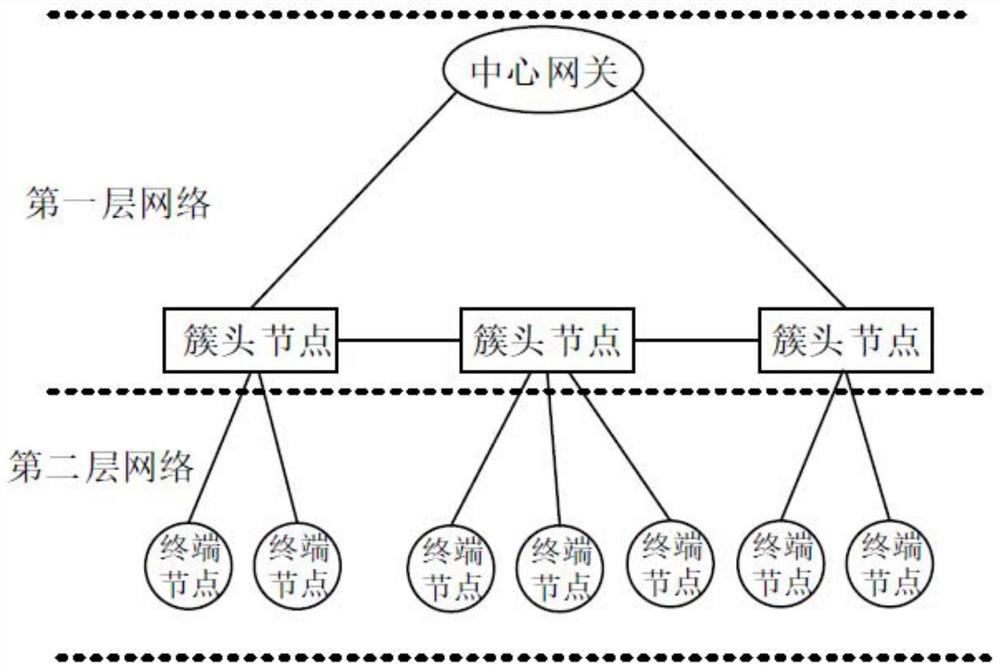
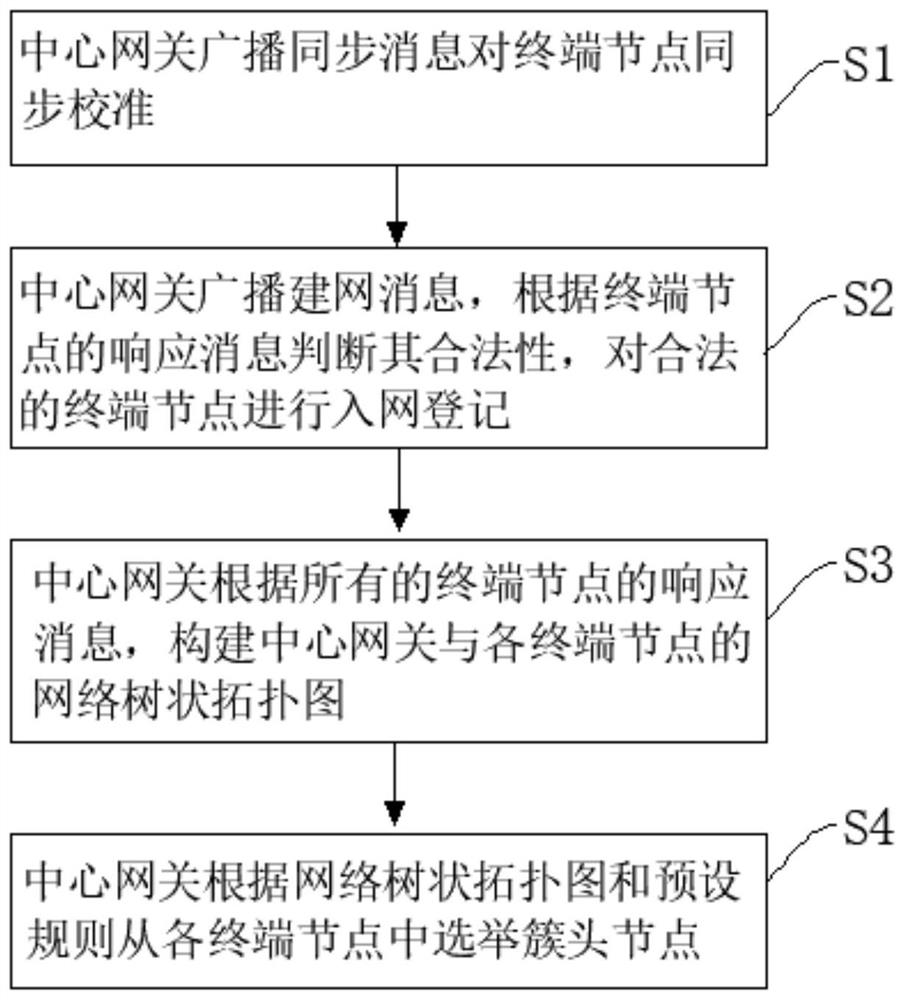
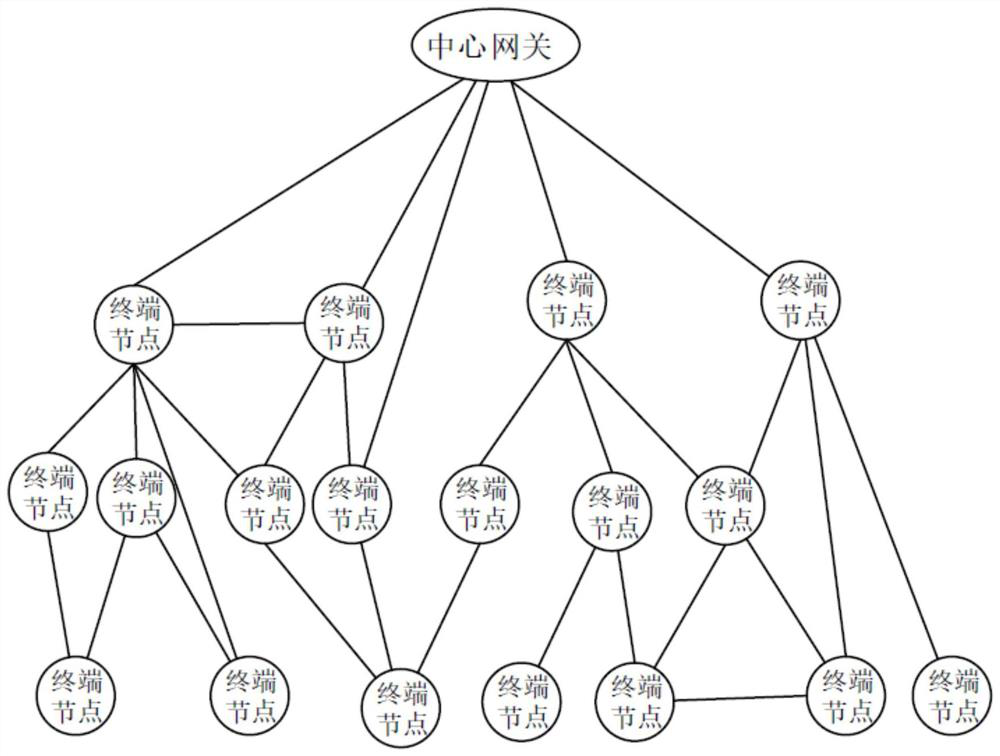
ActiveCN112105072AImprove throughputImprove communication efficiencyStar/tree networksHigh level techniquesCommunications systemThe Internet
The invention relates to the field of Internet of Things, and provides an Internet-of-Things communication system and a construction method thereof. The Internet-of-Things communication system comprises a first-layer network and a second-layer network, wherein the first-layer network is a multi-hop network which is constructed by a central gateway and a cluster head node and takes the central gateway as a root node; the second-layer network is a point-to-multipoint single-hop cellular network constructed by the cluster head node and the terminal node; and the cluster head node is generated byelecting from the terminal node according to a preset rule and is used for converging and forwarding data sent by the terminal node. In the networking initialization process of the terminal nodes, thecluster head node is elected according to the preset rule, it is guaranteed that the number of multi-hop levels from the center gateway of the first-layer network to the cluster head node is as smallas possible, the end-to-end time delay is reduced, and the throughput and the network transmission efficiency of the network are improved. The second-layer network is a point-to-multipoint single-hopcellular network, so that the communication requirement of low time delay during high-frequency concurrent data transmission of a large number of terminal nodes can be met.
Owner:SMART SHINE MICROELECTRONICS TECH CO LTD
MAC layer transmission protocol design method with limited control overhead
ActiveCN109348492AApplicable networking requirementsAvoid congestion or even paralysisNetwork topologiesWireless network protocolsTransmission protocolClear to send
The invention belongs to the field of communication and specifically relates to a MAC layer transmission protocol design method with limited control overhead. The method comprises the steps of initializing to generate a DATA message, sending an RTS (Request to Send) message, receiving the RTS message, sending a CTS (Clear to Send) message, receiving the CTS message, sending the DATA message, receiving the DATA message, sending a REQ message, receiving the REQ message, sending an SRQ (Selective Automatic Repeat Request) message, receiving the SRQ message, sending an ACK (Acknowledgement) message, receiving the ACK message and so on. By monitoring a channel reservation request RTS message sent by the next hop node and the REQ message of the next second hop node, the MAC layer transmission protocol design method with limited control overhead can judge correctness of the message transmission thereof, and accordingly can adjust and modify path information in time to solve problems of circumvention of invalid relay nodes and restoration of an interrupted transmission link. Network congestion, even network paralysis, caused by invalidity of transmission links, is avoided efficiently without adding any extra control message field within the limited control overhead, robustness of message transmission links is accordingly enhanced, the network lifecycle is prolonged and the MAC layer transmission protocol design method with limited control overhead is enabled to be more applicable to wireless sensor networking demands.
Owner:HARBIN ENG UNIV
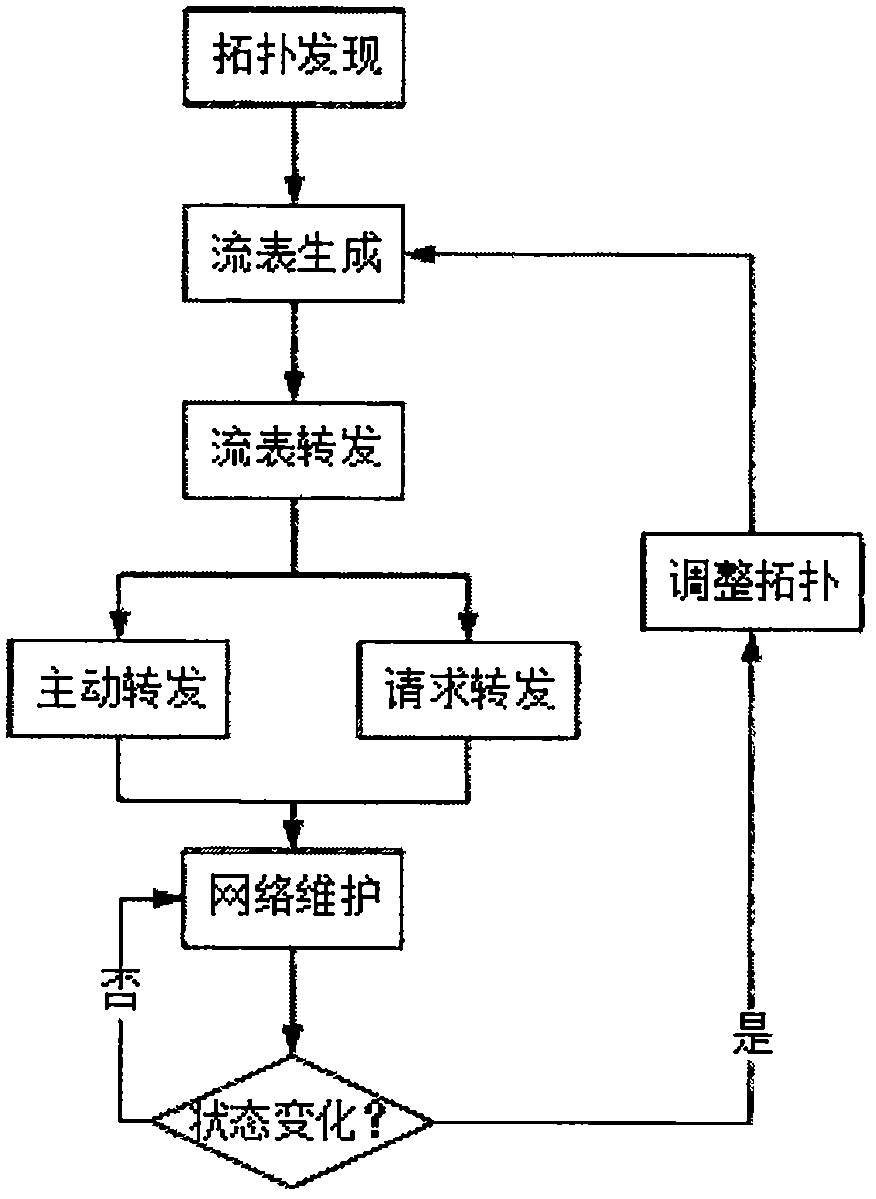
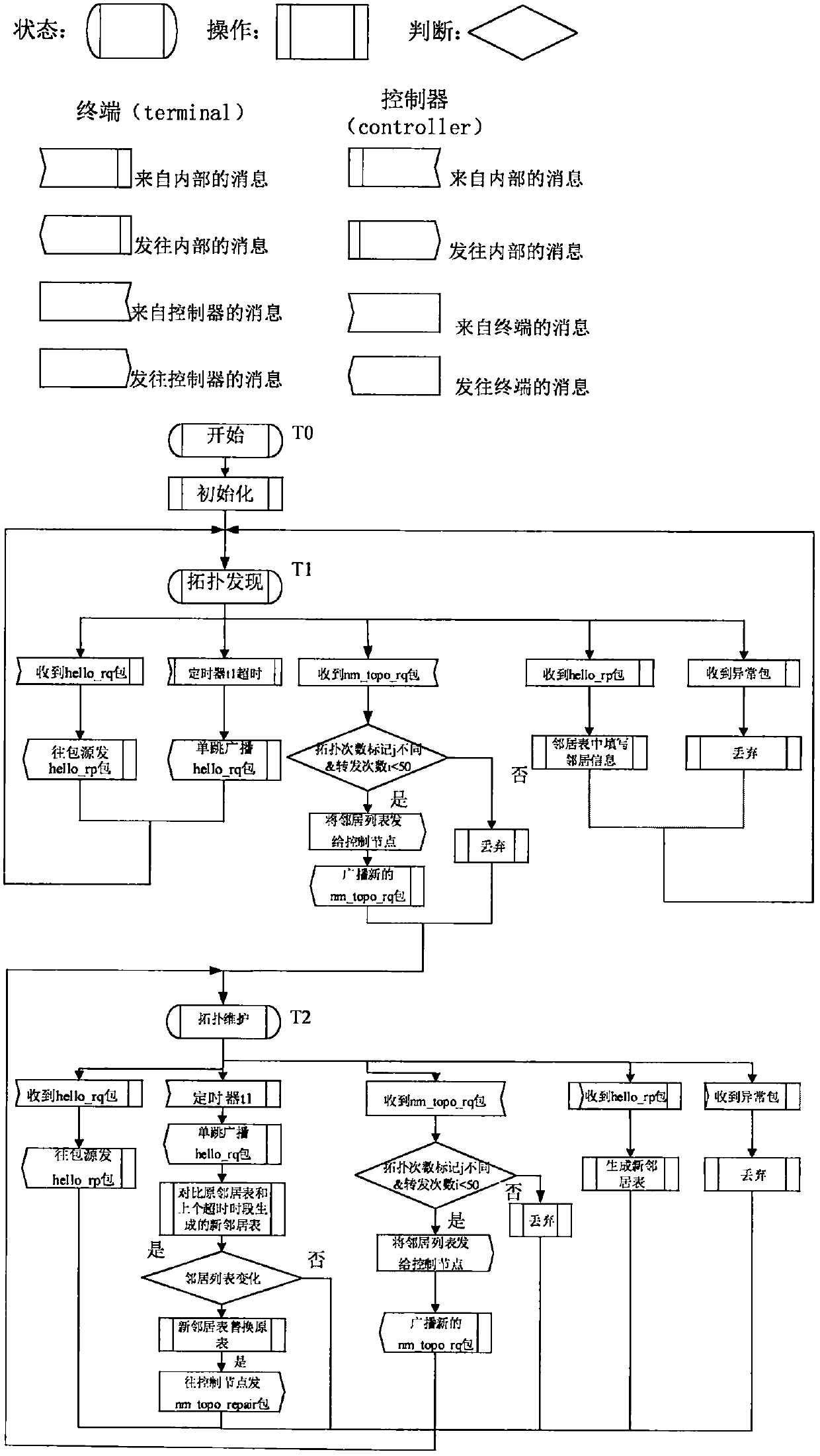
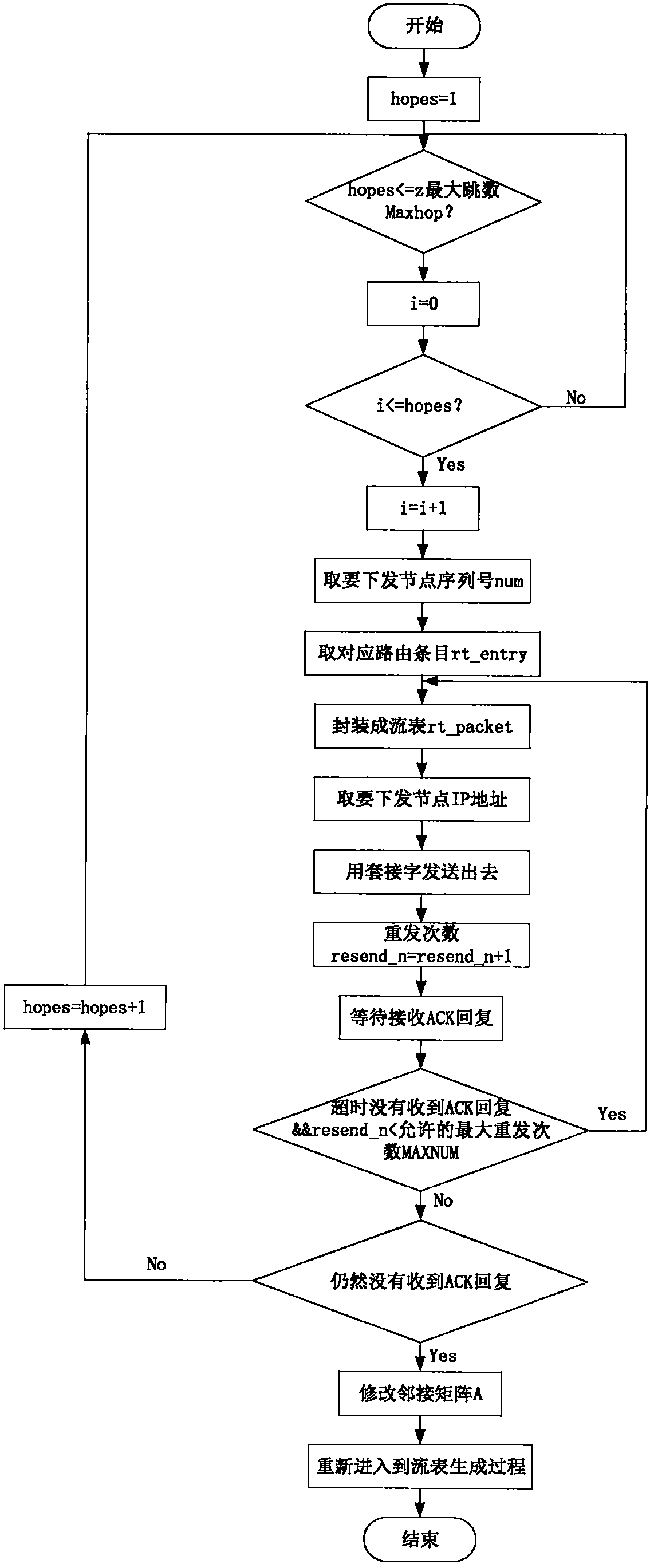
Low-power-consumption wide-area multi-hop networking method and system based on software definition
InactiveCN110650510AEasy to manageEasy to controlData switching networksHigh level techniquesNetwork managementControllability
The invention introduces a software defined network (SDN) technology into a low-power-consumption wide-area multi-hop network, and completes dynamic networking and flexible transmission of the networkthrough design and implementation of links such as topology discovery and maintenance, flow table generation and issuing and the like. Through control and data transmission decoupling of the network,software definition, flexibility and controllability of the network transmission process are realized, and meanwhile, the routing overhead of common sensing nodes is effectively reduced by adopting acentralized control algorithm, so that the routing success rate and the network stability are improved. The networking and transmission method provided by the invention is essentially different fromthe traditional routing-based networking method. According to the software defined network idea based on centralized control and numerical control separation, the advantages of a traditional softwaredefined network and the requirements of a wireless multi-hop network can be well met, and convenience is brought to the network management, centralized network configuration and the like of the wireless multi-hop network.
Owner:YUNNAN POWER GRID
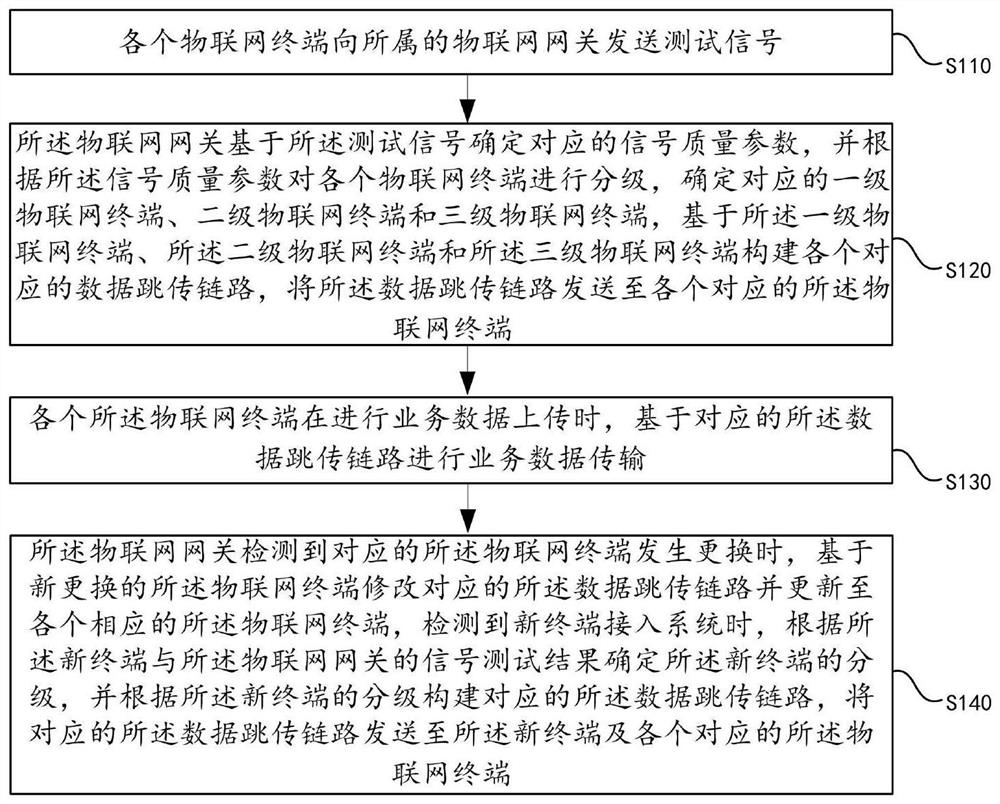
Method and device for data jump transmission link management based on system change
ActiveCN112533200BGuaranteed uptimeGuarantee the quality of signal transmissionSpatial transmit diversitySecurity arrangementLink managementEngineering
The embodiment of the present application discloses a method and device for managing data jump transmission links based on system changes. In the technical solution provided by the embodiment of this application, by sending the data jump link to each corresponding IoT terminal, each IoT terminal transmits business data based on the corresponding data jump link when uploading business data, and the IoT When the networking gateway detects that the corresponding IoT terminal is replaced or a new terminal is connected to the system, it modifies or newly constructs the corresponding data skip link, and sends the corresponding data skip link to the corresponding IoT terminal. Using the above-mentioned technical means, it is possible to build a data jump transmission link, ensure the quality of signal transmission in real time, and set the data jump transmission link according to the replacement or new access of the IoT terminal, so as to facilitate the setting of the signal transmission mode and further optimize the system data Transmission, optimize system business operation.
Owner:广州技象科技有限公司
A data forwarding method and device
The embodiment of the present application provides a data forwarding method and device, which relate to the communication field and can solve the problem that the relay node cannot forward the data to the correct next hop in the scenario of multi-hop wireless relay network or multi-hop and multi-connection network. node problem. The method is as follows: the first node receives the first data packet; wherein, the first data packet includes the first data and the identification of the second node of the first data; the first node queries the first routing mapping relationship according to the identification of the second node, The third node is determined; wherein, the first routing mapping relationship includes a corresponding relationship between the second node and the third node; the first node forwards the first data to the third node. This application is applied to multi-hop wireless relay networking or multi-hop and multi-connection networking scenarios.
Owner:HUAWEI TECH CO LTD
A design method of mac layer transmission protocol with limited control overhead
ActiveCN109348492BApplicable networking requirementsAvoid congestion or even paralysisNetwork topologiesWireless network protocolsTransmission protocolPathPing
Owner:HARBIN ENG UNIV
Local repair for underlay failure using prefix independent convergence
ActiveCN113765782AActive vector features are usefulNetworks interconnectionNetwork ConvergencePathPing
The embodiment of the invention relates to local repair for underlay failure using prefix independent convergence, and describes techniques for improving speed of network convergence after node failure. In one example, a method includes storing, by a virtual router agent of a compute node managed by a Software Defined Networking (SDN) controller, a forwarding information data structure with a shared liveness vector orthogonal to the forwarding path to indicate a liveness state of a plurality of overlay network tunnel endpoint next hops, wherein the shared liveness vector is shared by each of a plurality of members for a plurality of composite next hops that share a common list of the plurality of overlay network tunnel endpoint next hops; and in response to determining, by the virtual router agent, that the orthogonal liveness vector indicates that each of the plurality of overlay network tunnel endpoint next hops are reachable, distributing network traffic to one or more of the plurality of overlay network tunnel endpoint next hops.
Owner:JUMIPER NETWORKS INC
Mobile ad hoc network communication method, device and system and storage medium
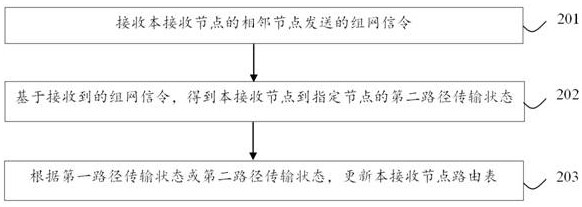
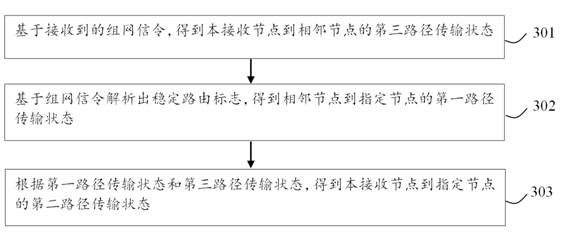
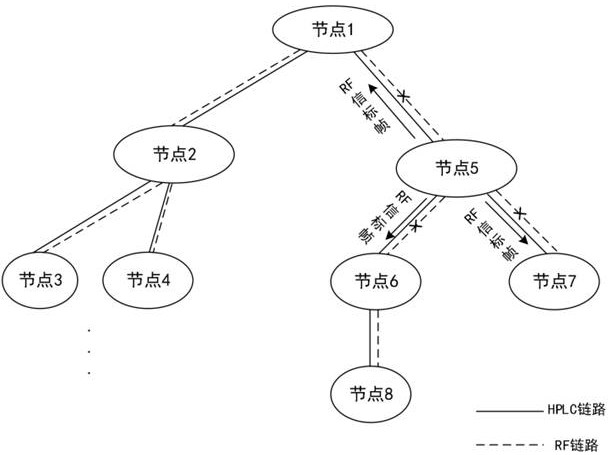
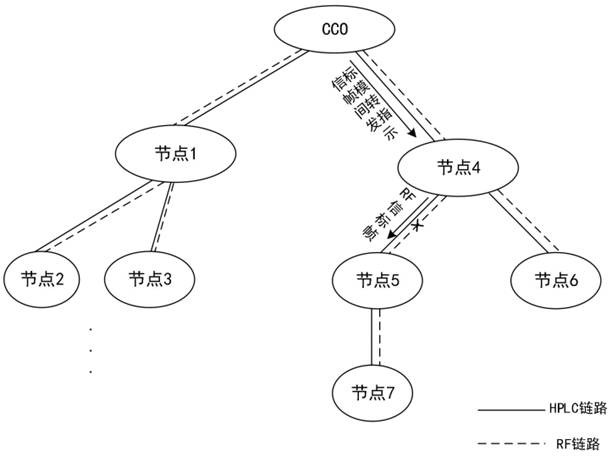
InactiveCN114786235AProcess stabilityImprove connectivityNetwork topologiesSignal allocationRouting tableEngineering
The invention discloses a mobile ad hoc network communication method, device and system and a storage medium. The method comprises the following steps: receiving a networking signaling sent by an adjacent node of a receiving node; the networking signaling comprises a stable routing mark and hop count information, the stable routing mark represents a first path transmission state that the adjacent node reaches a certain appointed node in the ad hoc network, and the hop count information represents the forwarding times that the adjacent node reaches the certain appointed node in the ad hoc network; obtaining a second path transmission state from the receiving node to the specified node based on the received networking signaling; and updating the routing table of the receiving node according to the first path transmission state or the second path transmission state. According to the embodiment of the invention, the stable routing mark is introduced, during networking, each node broadcasts and transmits the own stable routing mark and constructs / updates the routing table, and the routing table of each node can obtain the most stable next-hop node which arrives at the appointed node, so that the connectivity rate between two long-distance nodes is improved.
Owner:GUANGZHOU HUIRUI SITONG INFORMATION SCI & TECH CO LTD
Dual-mode inter-mode collaboration method and power Internet of Things network system
The invention provides a dual-mode inter-mode collaboration method and an electric power Internet of Things network system, which belong to the field of electric power Internet of Things wireless communication. The method includes: if the module A of the sending node is disconnected through the communication of the A link, the sending node performs inter-module coordination, and requests the module B of the sending node to construct a network frame and forward it through the B link, and the type of the network frame is module After the receiving node receives the inter-module forwarding frame through module B, it performs inter-module coordination and sends the inter-module forwarding frame to module A of the receiving node, so that module A of the receiving node obtains communication data. The method provides cooperative networking function, realizes inter-module beacon frame and networking command frame forwarding, improves network networking reliability; provides single-hop service transmission path backup and selection function, and realizes single-hop inter-mode data frame and command frame forwarding , Improve the reliability of network data transmission.
Owner:BEIJING SMARTCHIP MICROELECTRONICS TECH COMPANY +3
Programmatically determining next-hop mac address
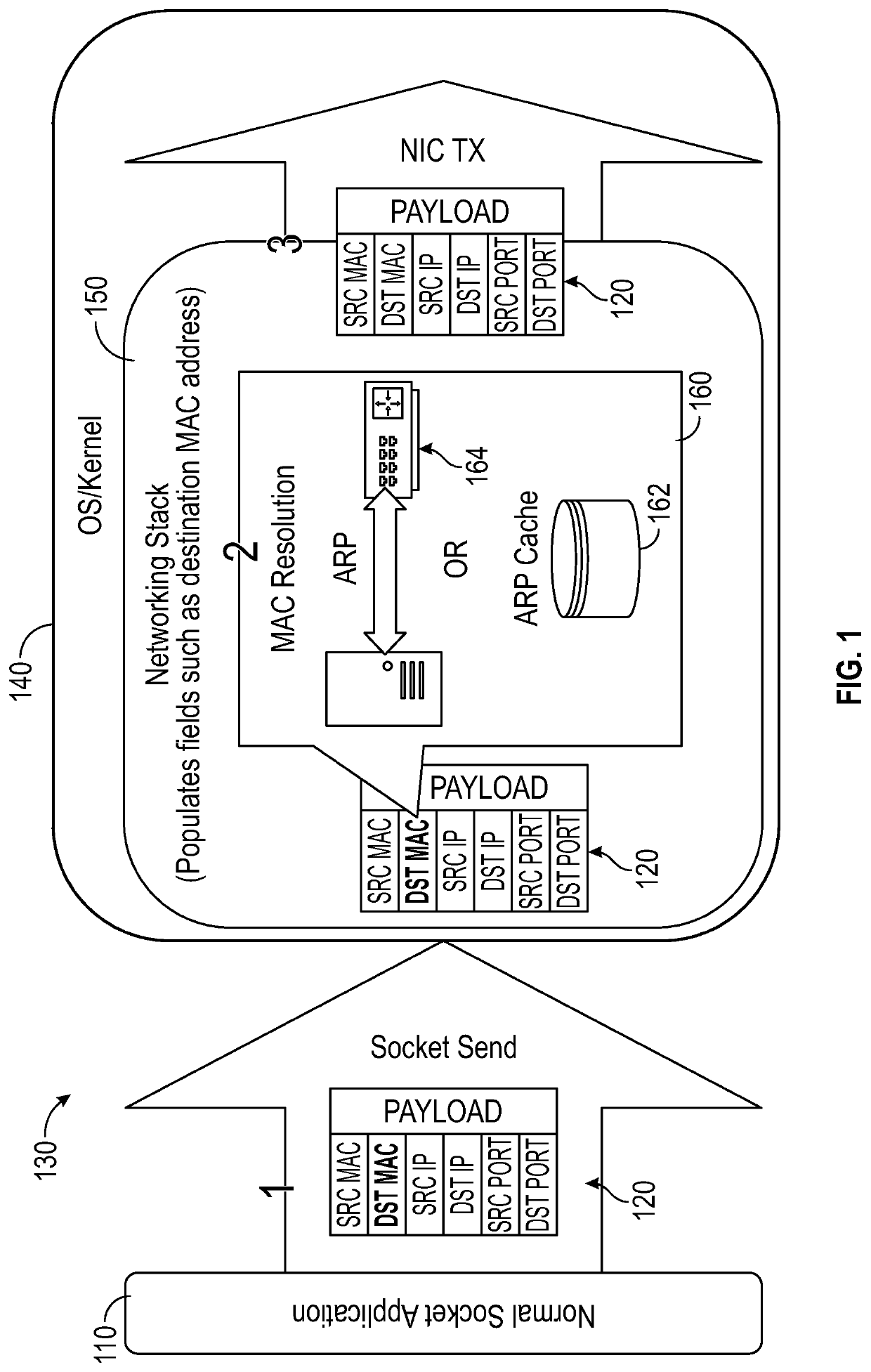
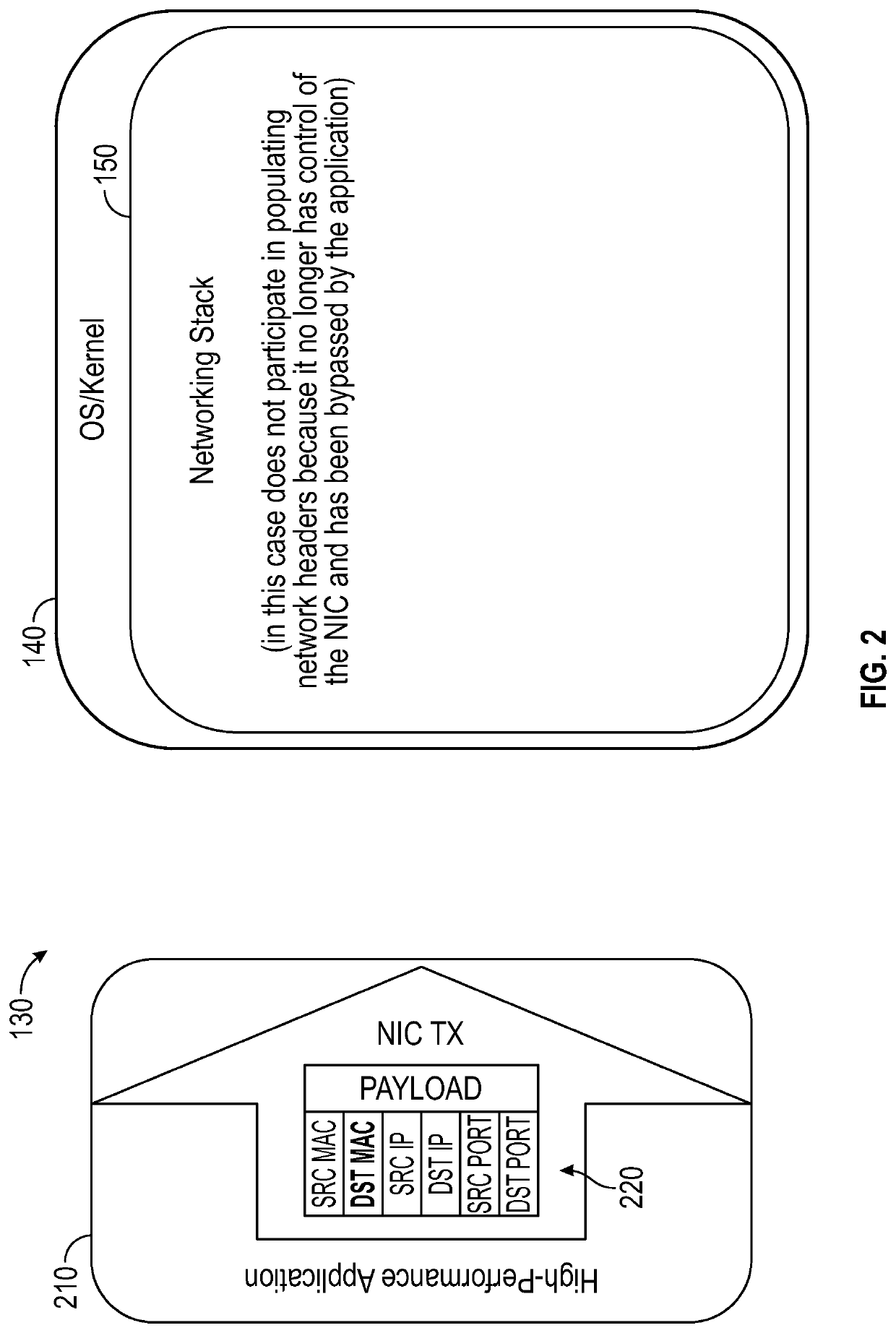
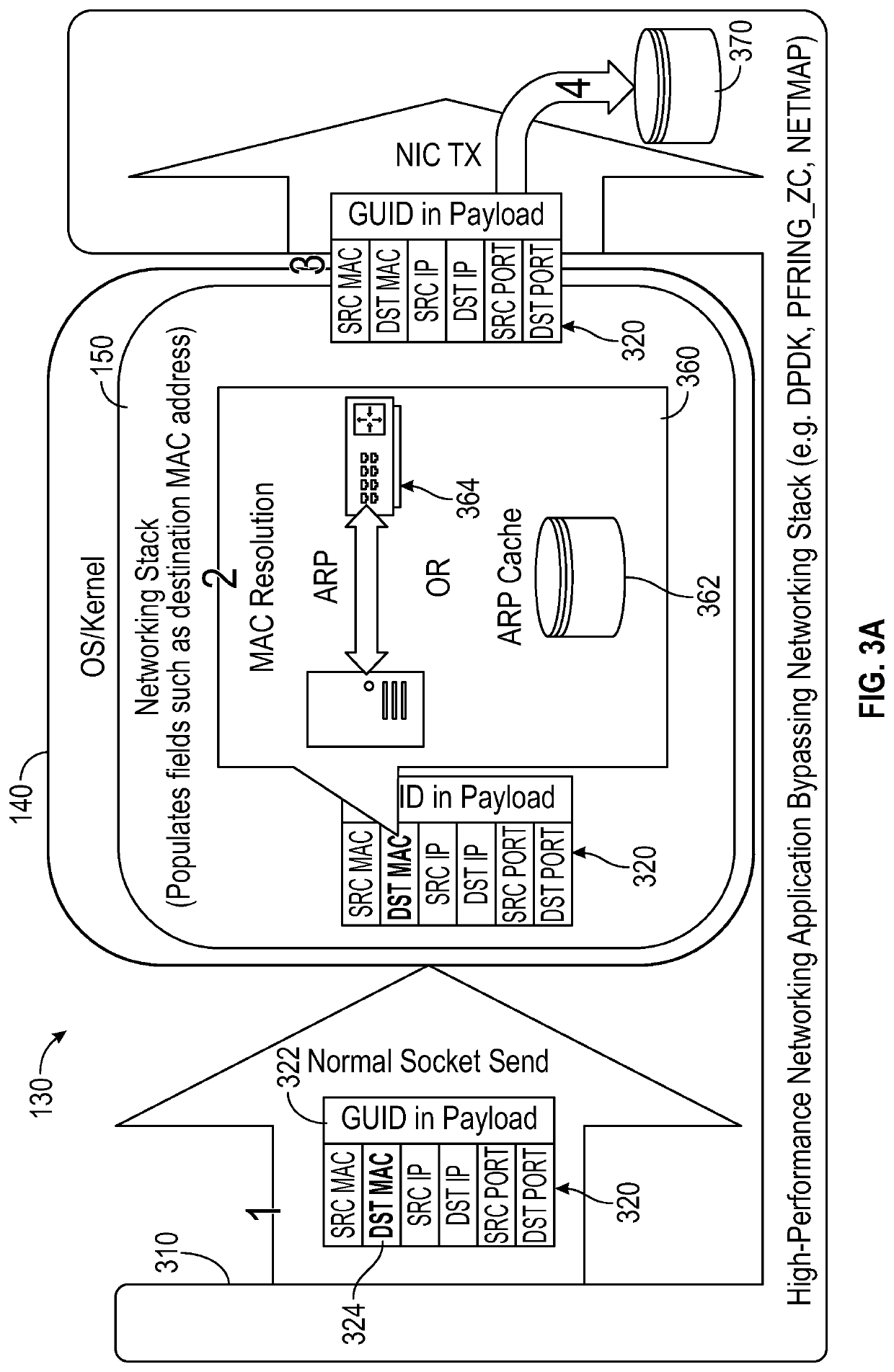
Systems, media, and methods are capable of determining a layer 2 destination address that can then be used by a network acceleration application to populate data packets to be transmitted using accelerated networking techniques. The systems and methods provide for a software application executed on a computing device that controls a NIC interface to provide for an accelerated network. The software application resides in the application layer of a networking stack and is interfaced via a virtual NIC or TUN / TAP device with the kernel and the networking stack and operating system (OS) facilities to determine a layer 2 destination address for use in accelerated network applications. Embodiments herein, through the combination above, are able to account for firewall rules, static ARP entries, or any other system-administrator rules put in place for network operations.
Owner:KRATOS INTEGRAL HLDG LLC
A message forwarding method and device
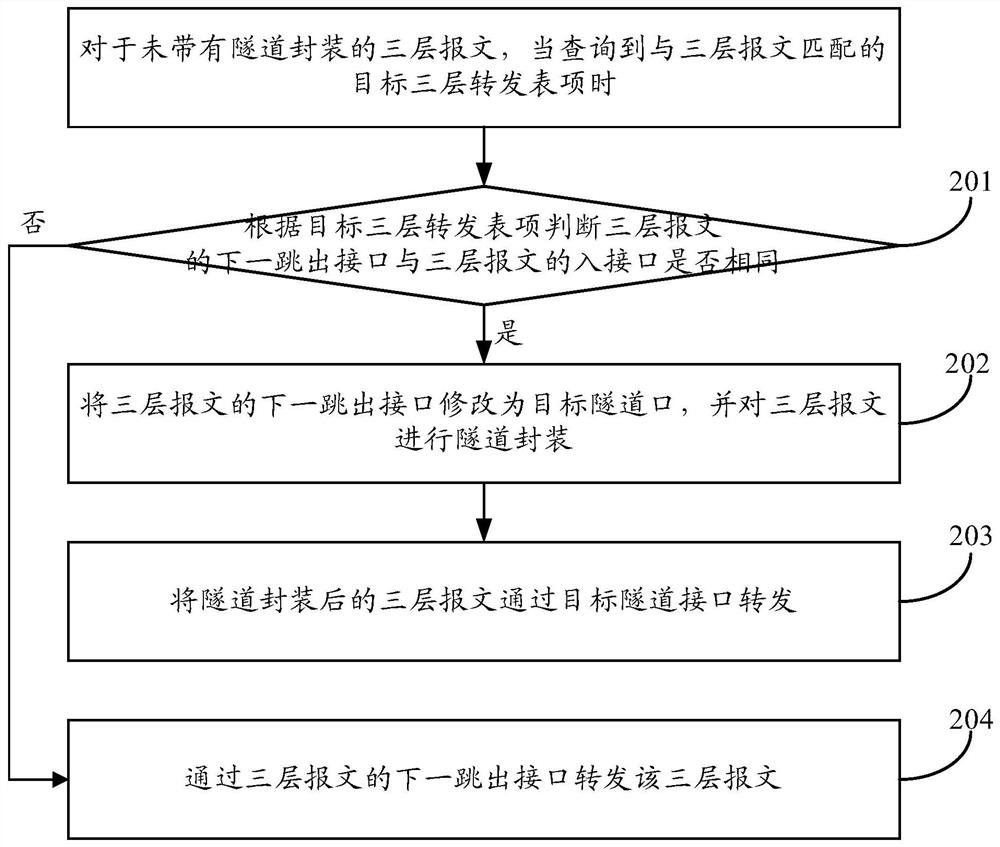
ActiveCN108965126BAvoid it happening againImprove reliabilityData switching networksEngineeringPacket forwarding
The present invention provides a message forwarding method and device. The method includes: for a Layer 3 message without tunnel encapsulation, when a target Layer 3 forwarding entry matching the Layer 3 message is found, the The target three-layer forwarding entry judges whether the next-hop outgoing interface of the three-layer message is the same as the incoming interface of the three-layer message; if they are the same, the next-hop outgoing interface of the three-layer message is modified to target tunnel interface, and perform tunnel encapsulation on the layer-3 message; forward the layer-3 message after tunnel encapsulation through the target tunnel interface; if different, exit through the next hop of the layer-3 message The interface forwards the Layer 3 packet. The application of the embodiments of the present invention can reduce the probability of loops in the data center networking and improve the reliability of the array center networking.
Owner:NEW H3C TECH CO LTD
A method and device for publishing network routes
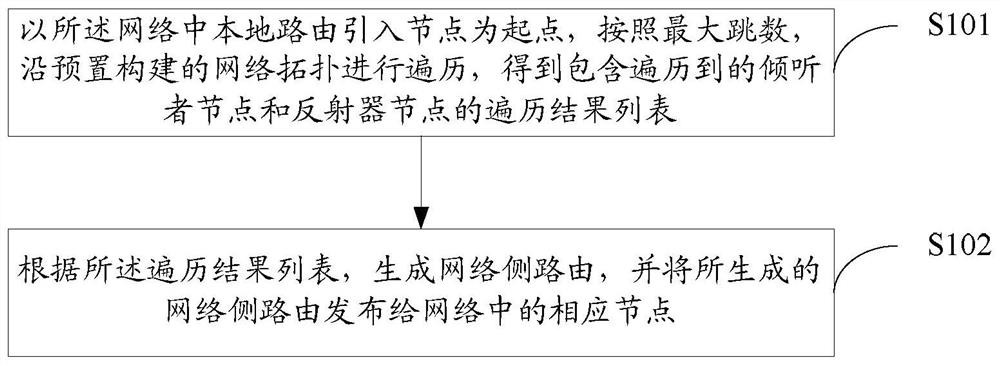
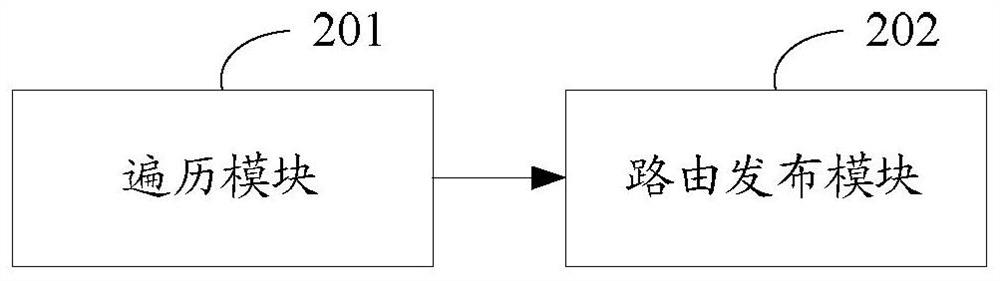
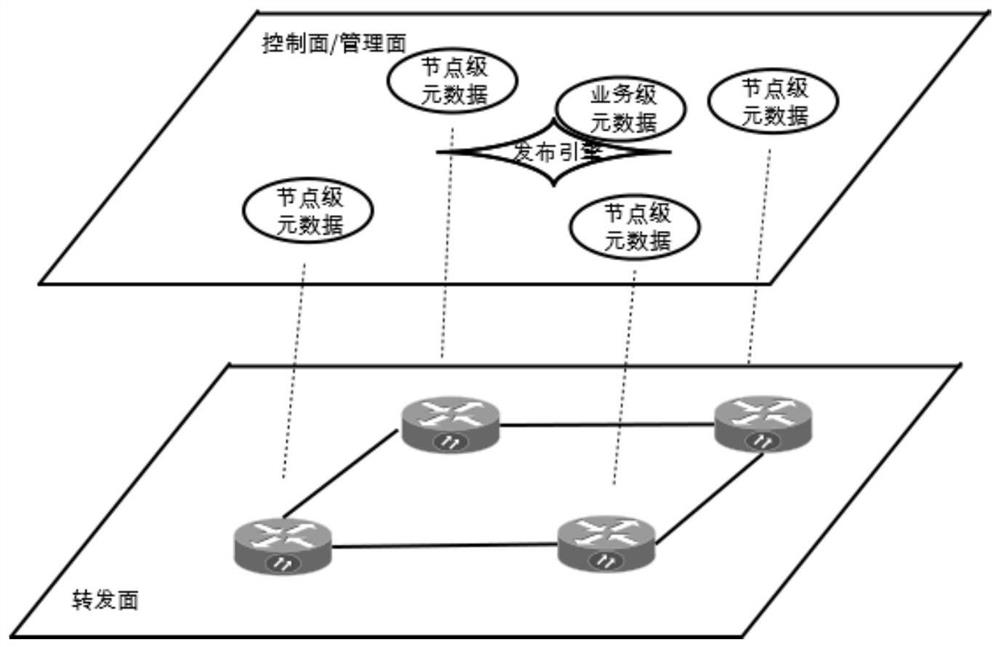
The invention discloses a method and device for publishing a network static route, which relates to the technical field of data communication. The method comprises: starting from a local route introduction node in the network, and proceeding along a preset network topology according to the maximum number of hops Traversing to obtain a traversal result list including the traversed listener nodes and reflector nodes; generating a network-side route according to the traversal result list, and publishing the generated network-side route to corresponding nodes in the network. The present invention customizes the publishing rules through metadata configuration to more flexibly and quickly adapt to the L3VPN route publishing algorithm of various networking scenarios.
Owner:ZTE CORP
Energy-equalized workflow
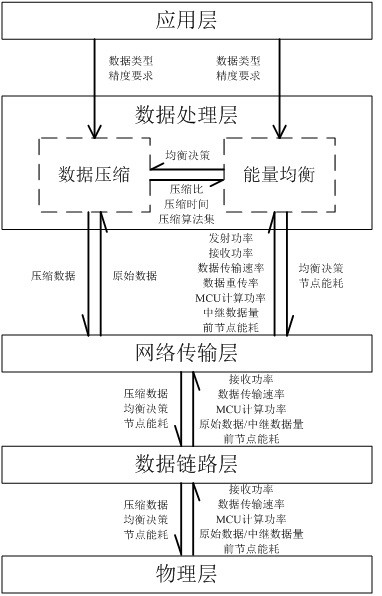
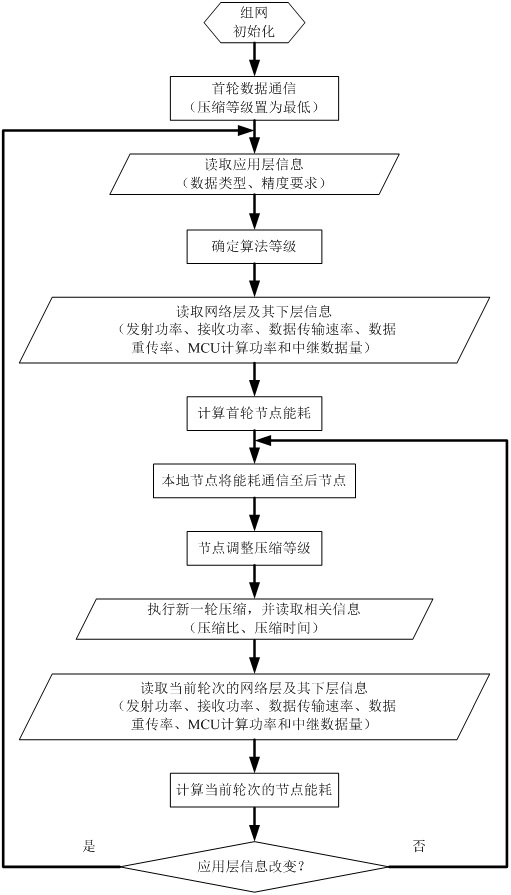
InactiveCN112423359AExtend your lifeEnergy savings and equalizationPower managementNetwork topologiesEnergy balancingOriginal data
The invention provides a workflow of an energy balancing method, which comprises the following steps that: 01, after a node finishes deployment and networking initialization, the node starts to collect original data and transmits the processed data to a Sink hop by hop, which is uplink communication and finishes the first round of data communication; 02, acquiring related information from an application layer by an energy balancing module; step 03, according to the related information provided by the application layer, the energy balance module acquiring an algorithm level in a preset compression algorithm set; 04, acquiring related information from the network transmission layer and the lower layer of the network transmission layer by the energy balancing module; step 05, the energy balance module calculates the energy consumption of the local node in the first round of data communication according to the known parameters; step 06, the energy balance module transmits the calculated total node energy consumption of the current round to a physical layer in a downlink manner, and communicates to a back node in a downlink manner through a message frame; the method has the advantages that saving and balancing of energy consumption are considered simultaneously, so that the network service life is prolonged.
Owner:ZHEJIANG BUSINESS TECH INST
A testing method for wired mesh network
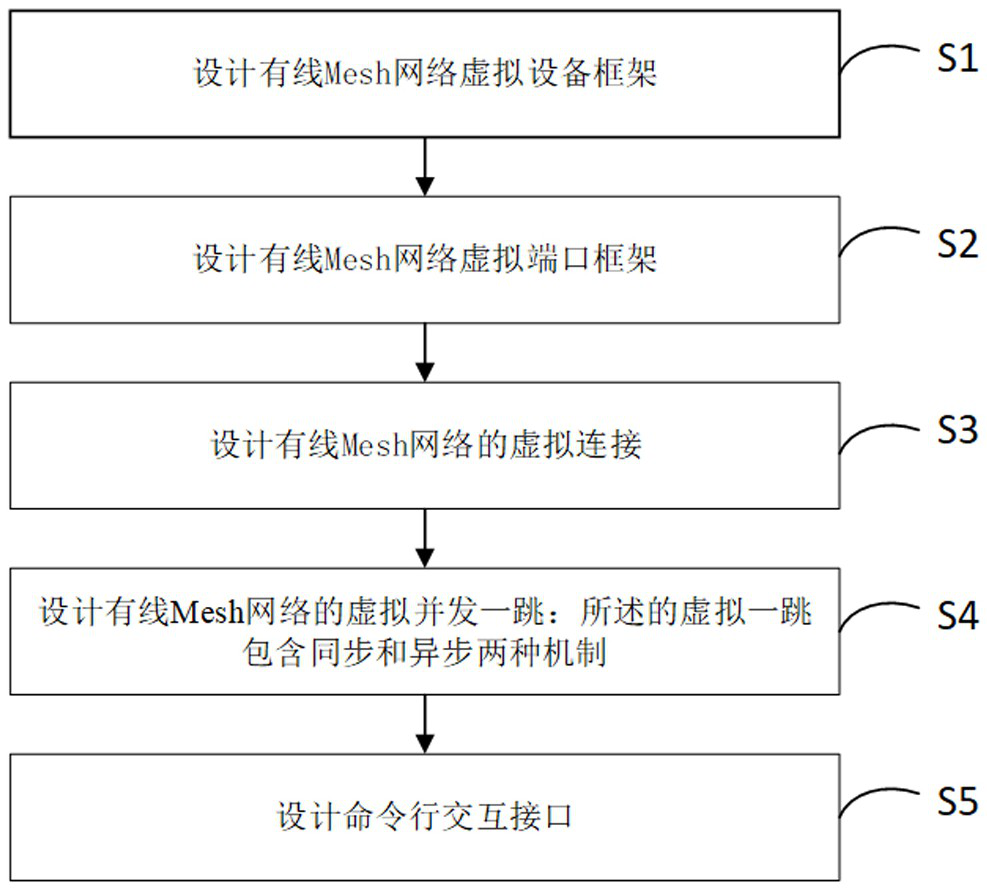
ActiveCN113572652BEfficient feedbackEfficient feedback on the running effect of code modificationData switching networksComputer architectureVirtual appliance
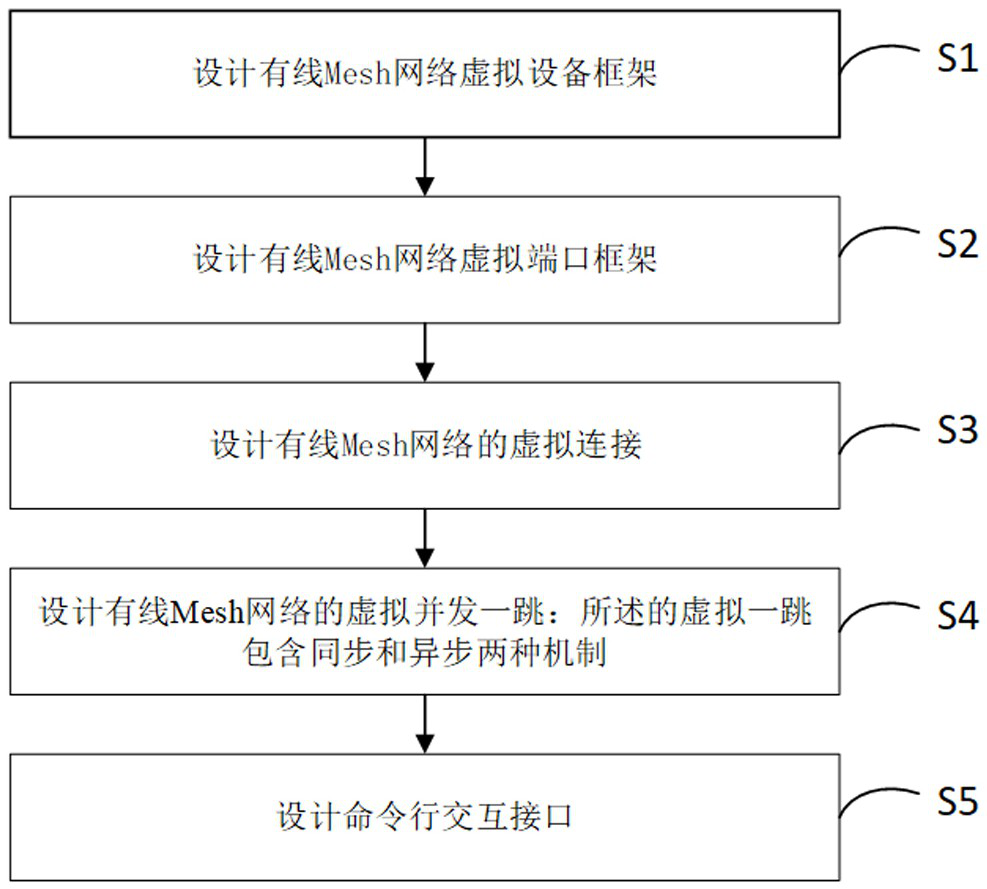
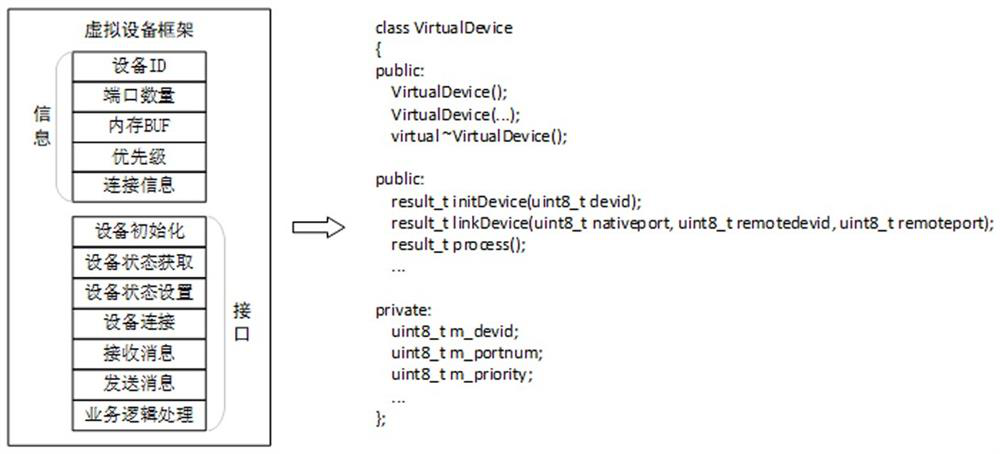
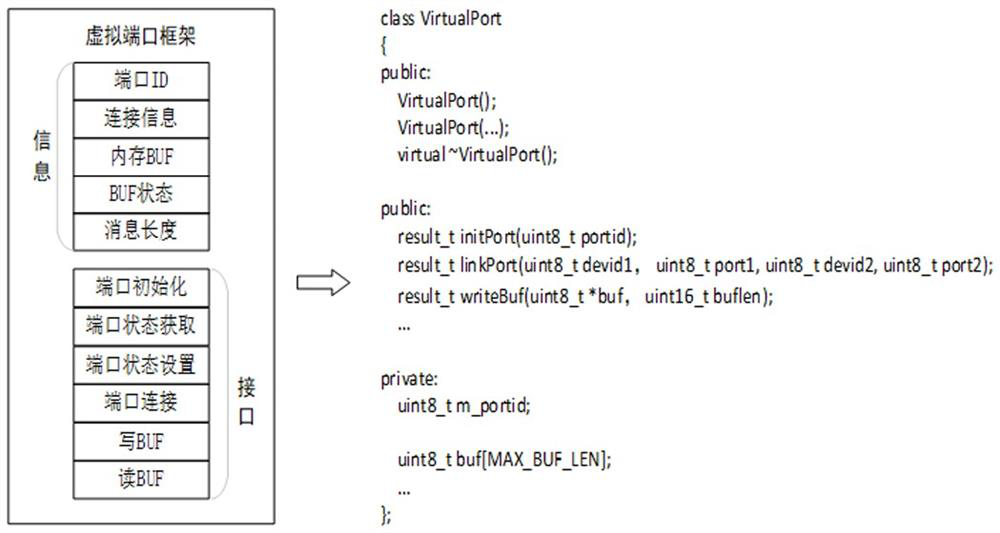
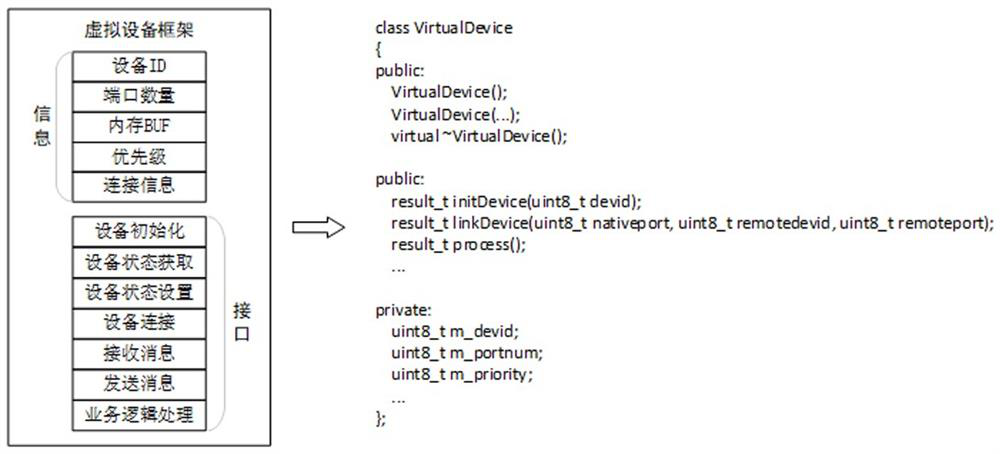
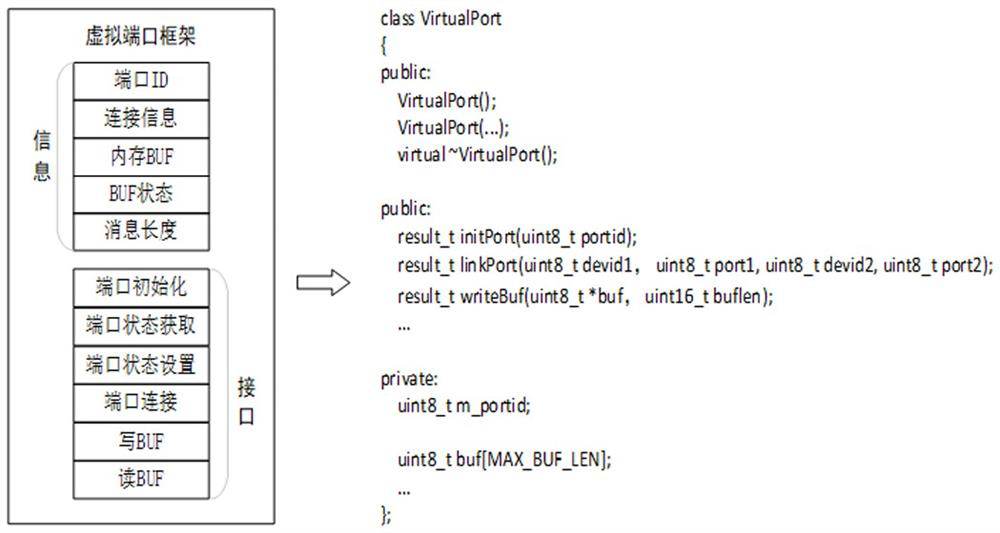
The invention discloses a wired Mesh network testing method, comprising: designing a virtual device frame of the wired Mesh network; designing a virtual port frame of the wired Mesh network; designing a virtual connection of the wired Mesh network; designing a virtual concurrent hop of the wired Mesh network; and designing commands line interaction interface. The invention separates the concepts of equipment and ports, breaks the binding relationship between the two in traditional physical concepts, and thus can realize very complex networking scenarios with very simple codes. At the same time, the invention avoids the complexity of concurrent programming through the design concept of virtual one-hop. The synchronous one-hop mode can simulate the wired Mesh networking with synchronous function, and the asynchronous one-hop mode can also cover most of the function verification scenarios. The entire test framework is very simple, easy to develop, maintain and expand, and can effectively assist developers and testers to carry out related work, shorten the project cycle, and improve product quality.
Owner:ZHEJIANG LAB
A state-aware software-defined networking method
ActiveCN106230737BRealize automatic networkingReduce energy consumptionSubstation remote connection/disconnectionHigh energyData level
Owner:ANSHAN POWER SUPPLY COMPANY OF STATE GRID LIAONING ELECTRIC POWER COMPANY +3
Networking method and wireless communication device of a hybrid access mode multi-hop network
ActiveCN106131923BReduce access conflict probabilityAchieve accessPower managementAssess restrictionAccess networkTrunking
The invention discloses a networking method of a multi-hop network with hybrid access modes. The network comprises three kinds of logic nodes consisting of gateway nodes, relay nodes and terminal nodes, wherein the terminal node and the gateway node perform communication by establishing direct connections or indirect connections, the access mode of accessing the gateway node by the direct connection is different from the access mode of accessing the gateway node by the indirect connection; and furthermore, the different access modes can be used when the relay node in the network accesses the gateway node, the relay node accesses the upper-level relay node, the terminal node accesses the relay node, or the terminal node directly accesses the gateway. According to the method, the hops of the multi-hop network are allowed to use different access modes instead of the traditional single access or connection mode adopted by a traditional mesh network, wide area network coverage and access of lots of connections based on the multi-hop network are achieved, and unnecessary spectrum resource and battery energy consumption overheads are avoided.
Owner:XIAMEN ZIFI INFORMATION TECH CO LTD
A method for constructing virtual-real decoupling simulation network
An embodiment of the present invention provides a method for constructing a virtual-real decoupling simulation network, including: S1, obtaining a user-defined configuration simulation network planning script, which includes the simulation network topology and the function information of each node therein; S2, According to the simulation network planning script, each node of the simulation network is distributed and deployed on multiple physical hosts connected through the physical network; S3, build a data plane device connecting all nodes on each physical host, and configure it in a software-defined manner Based on the Overlay tunnel technology, each data plane device constructs a logical topology by networking scattered nodes to form a simulated network that is decoupled from the physical network and allows data frames to be transmitted hop by hop. The construction process of the present invention is completely transparent to the physical network cluster, and without depending on and without changing the networking and configuration of the physical network cluster, an arbitrary simulation network topology structure decoupling between virtual and real can be constructed.
Owner:INST OF COMPUTING TECH CHINESE ACAD OF SCI
A network topology control method in cognitive vehicle networking
ActiveCN112468996BEliminate distractionsSolve congestionParticular environment based servicesVehicle wireless communication serviceInformation transmissionLink weight
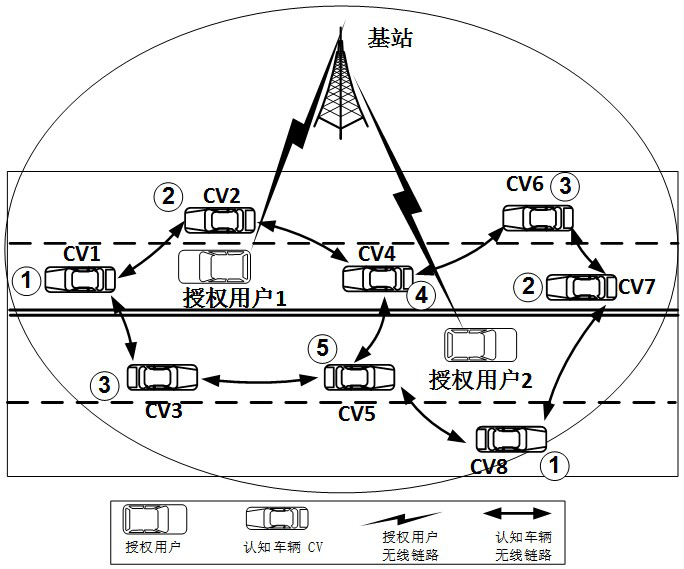
The invention discloses a network topology control method in a cognitive vehicle networking, which mainly solves the problems of network topology splitting and mutual interference of cognitive vehicles caused by any channel being occupied in the prior art. The implementation process of the method is as follows: 1. Each vehicle node in the network first uses the directional information transmission mechanism in the present invention to obtain one-hop neighbor information; 2. Based on the one-hop neighbor information, each vehicle node uses the two-hop neighbor information in the present invention. The hop neighbor discrimination mechanism obtains a local two-hop topology map; 3. Each vehicle node constructs a local generated subgraph that can ensure the connectivity of the topology structure according to the link weight proposed in the present invention; 4. All vehicle nodes in the network are based on the optimized The locally generated subgraph of the channel is requested and used to avoid interference in the network. The method of the invention can ensure the network connectivity after any channel in the network in the cognitive vehicle networking is occupied, and improve the fault tolerance and robustness of the network topology structure.
Owner:EAST CHINA JIAOTONG UNIVERSITY +1
Wired Mesh network test method
ActiveCN113572652AEfficient feedbackEfficient feedback on the running effect of code modificationData switching networksInteraction interfaceNetwork testing
The invention discloses a wired Mesh network test method. The method comprises the following steps: designing a wired Mesh network virtual equipment framework; designing a wired Mesh network virtual port framework; designing virtual connection of the wired Mesh network; designing a virtual concurrent hop of the wired Mesh network; and designing a command line interaction interface. According to the invention, the concepts of the equipment and the port are separated, and the binding relationship between the equipment and the port in the traditional physical concept is broken, so that a very complex networking scene can be realized by using very simple codes. Meanwhile, the complexity of concurrent programming is avoided through a virtual one-hop design concept, a synchronous one-hop mode can simulate wired Mesh networking with a synchronization function, and an asynchronous one-hop mode can also cover most of function verification scenes. The whole test framework is very simple, easy to develop, maintain and expand, and capable of effectively assisting development and testing personnel to carry out related work, shortening the project period and improving the product quality.
Owner:ZHEJIANG LAB
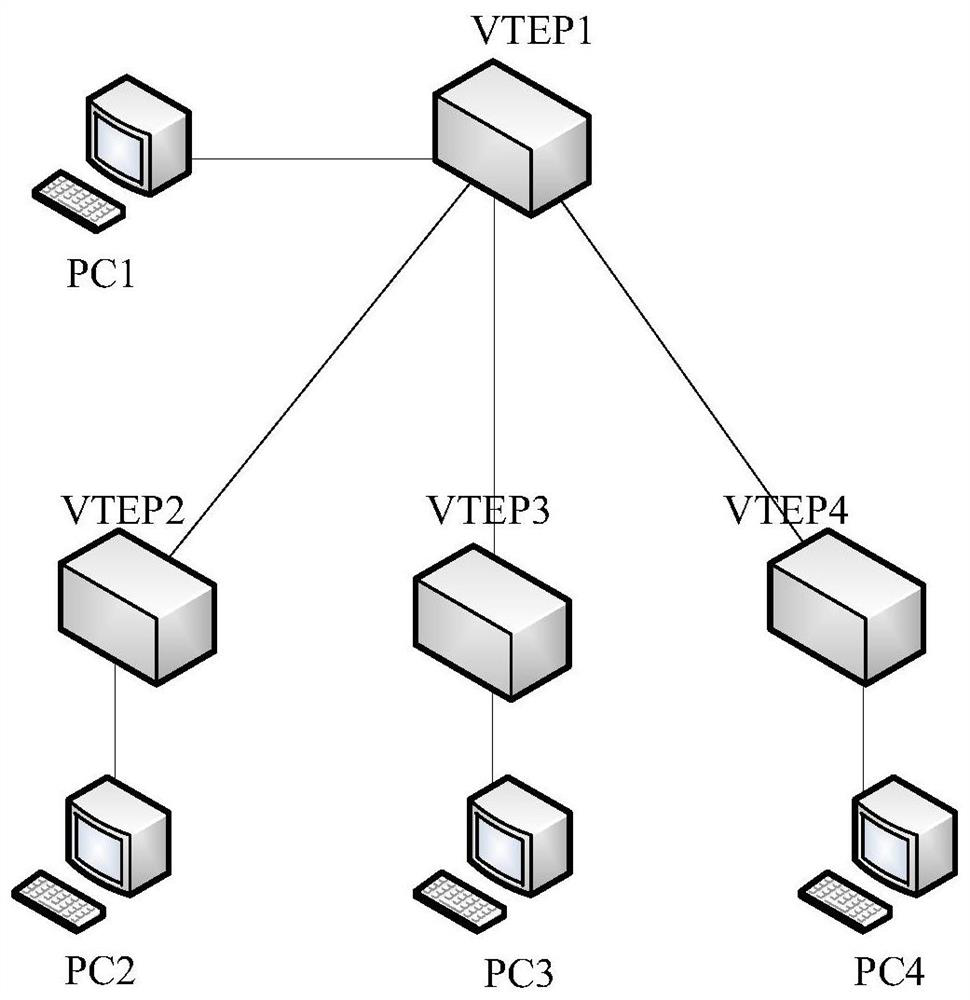
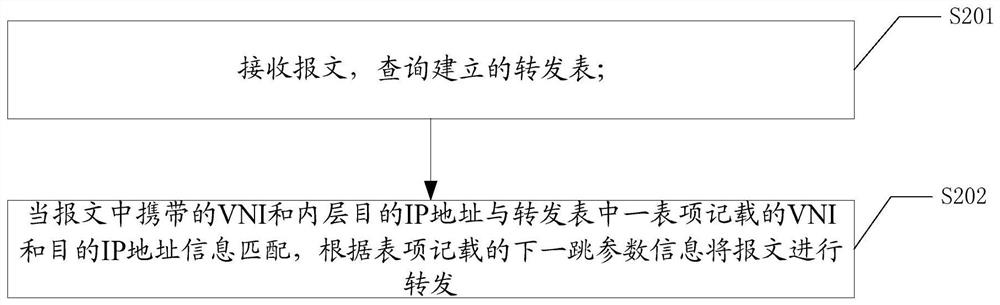
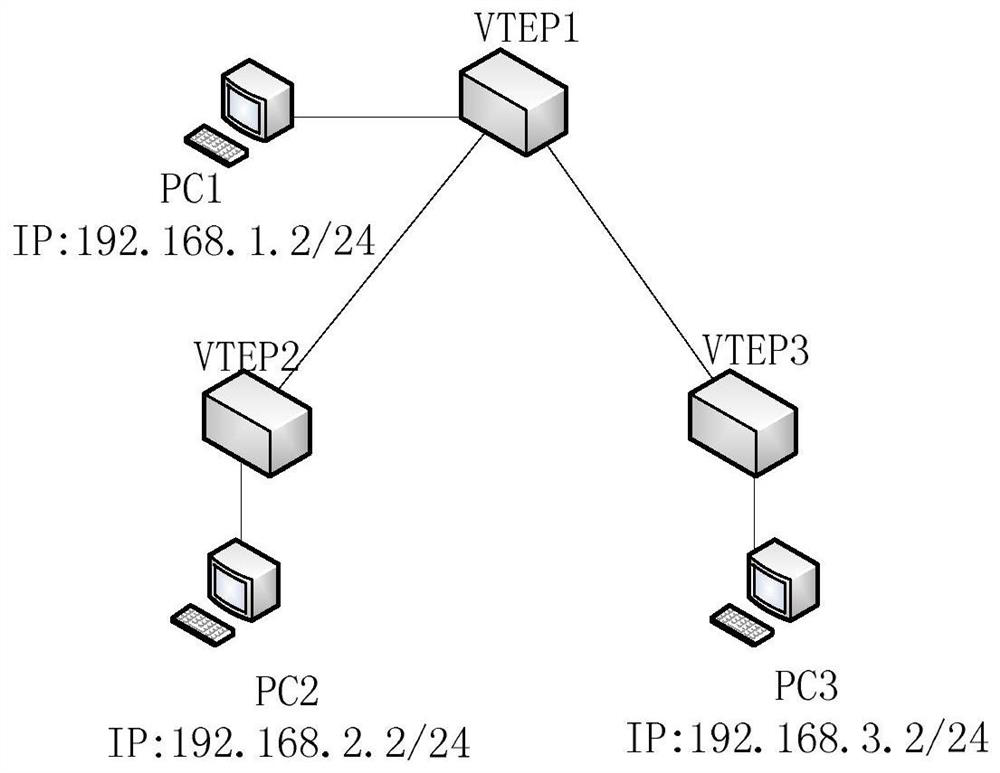
A message sending method and device in vxlan axis networking mode
A message sending method, device, storage medium and terminal in a VXLAN axis networking mode, the method includes: receiving a message, querying an established forwarding table; the forwarding table includes one or more entries, and the The table item content includes virtual network identification VNI, destination IP address information, and next-hop parameter information, and the next-hop parameter information includes: next-hop message outer layer source IP address and User Datagram Protocol UDP port number; When the VNI carried in the message and the inner layer destination IP address match the VNI and the destination IP address information recorded in an entry in the forwarding table, the message will be forwarded according to the next hop parameter information recorded in the table entry to retweet. This application can realize the transmission of messages between terminals located in different network segments in the hub-spoke networking scenario.
Owner:RAISECOM TECH
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com