Phishing webpage detection method
A technology for phishing web pages and detection methods, applied in special data processing applications, instruments, platform integrity maintenance, etc., can solve problems such as low efficiency, difficult application, and complex computing.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
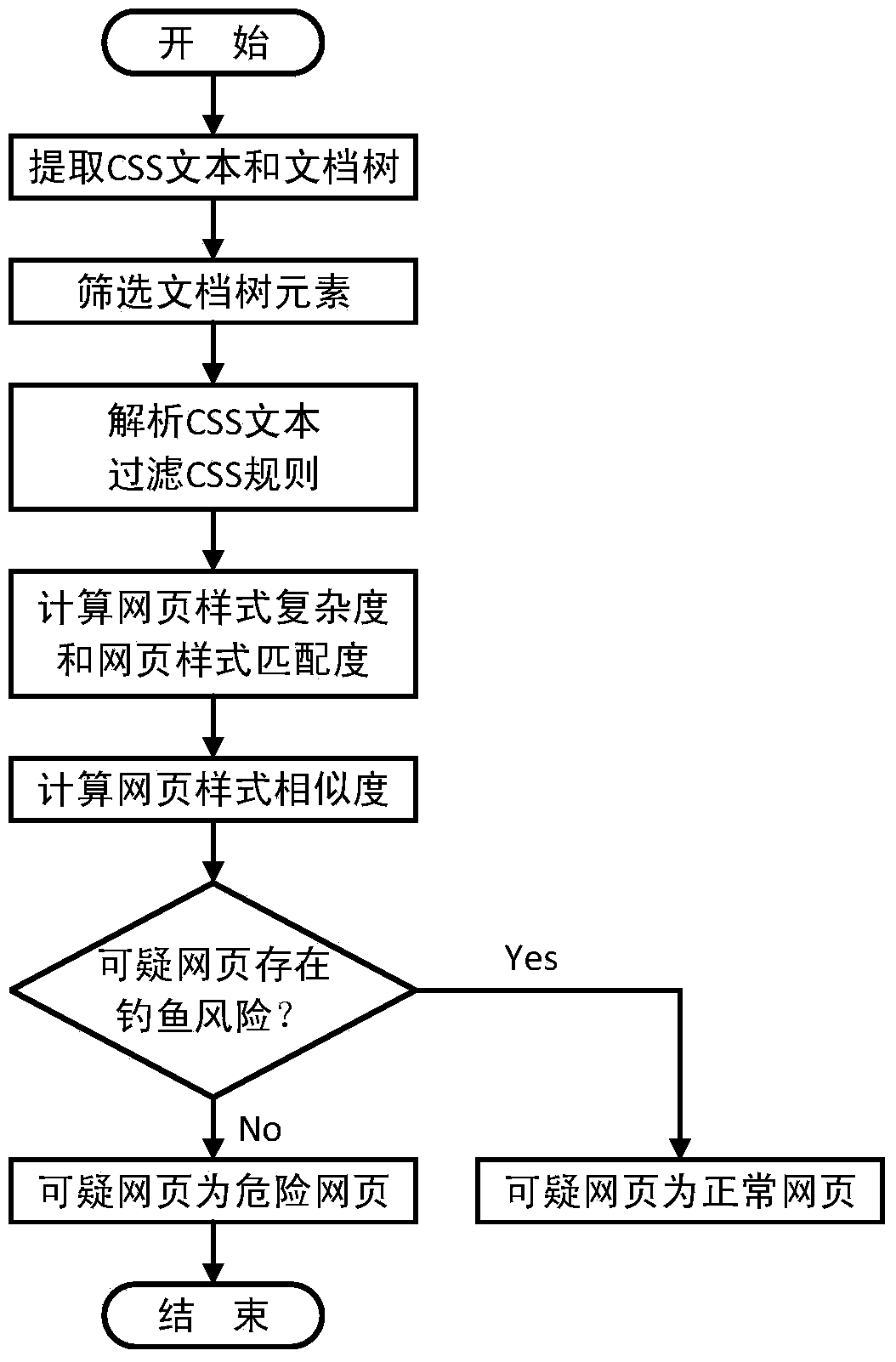
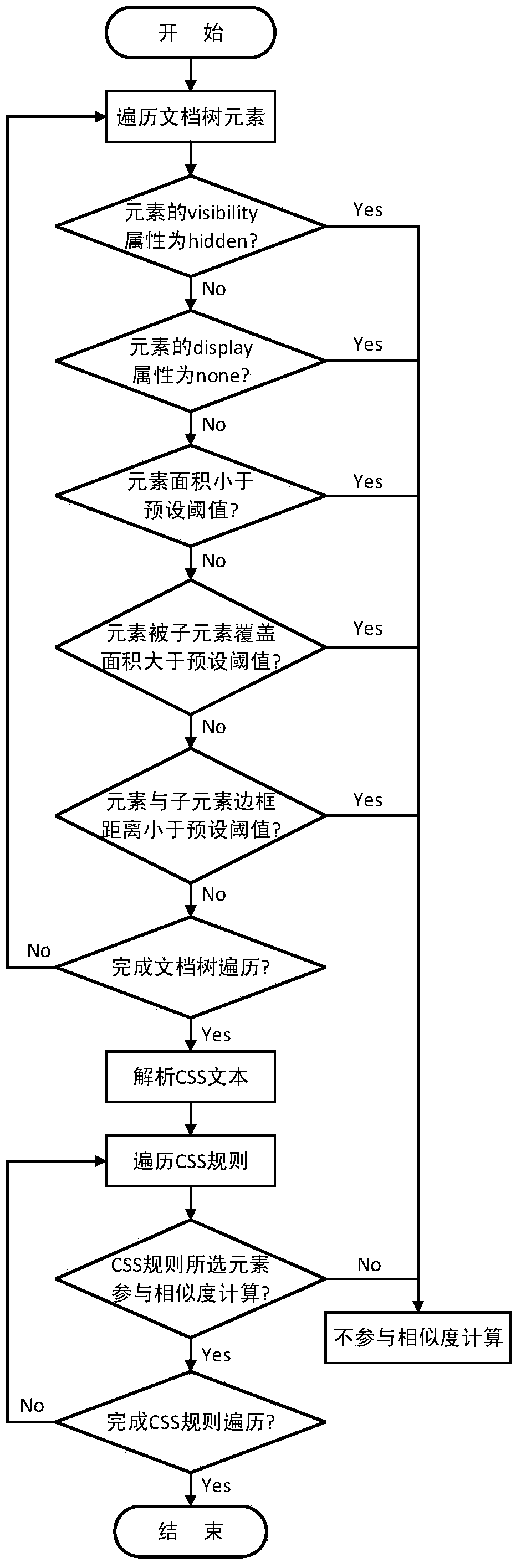
[0066] See figure 1 — Figure 4, the present invention proposes a method for detecting phishing webpages, which detects phishing webpages by comparing the similarity of webpage styles of two webpages. The method is divided into four steps: web page style feature extraction, web page style feature screening, web page style similarity calculation and result judgment. The method will be described in detail below.
[0067] Step 1: Web page style feature extraction
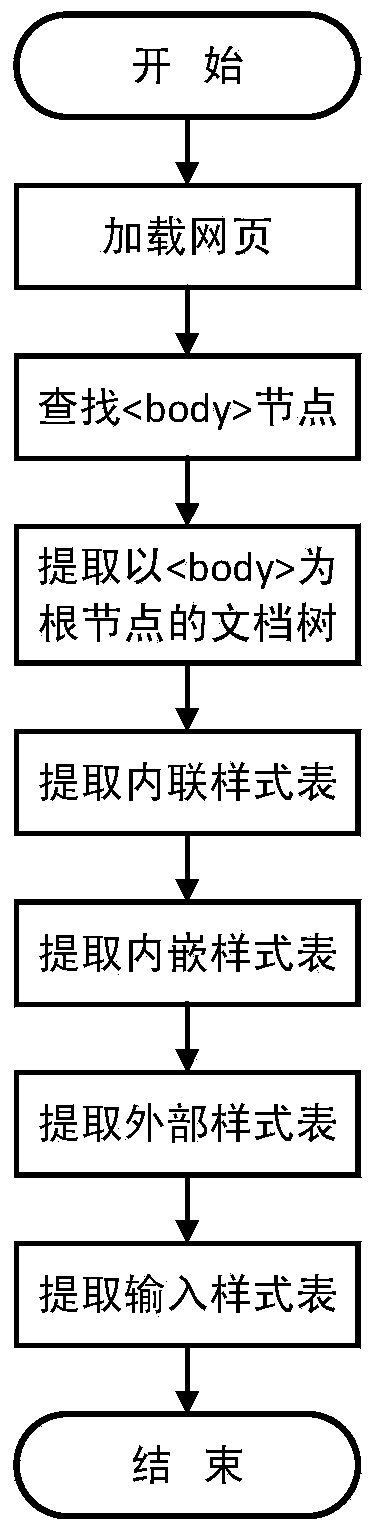
[0068] ● Document tree extraction. To extract the document tree with the body element as the root node in the DOM of the page, it is necessary to ensure that each element in the document tree is an object of type Element. Because the .children() method extracts all Element objects, use the .children() method to extract the child elements of each element in the document tree. Each node in the document tree needs to store the name (tagName), class name (class) and ID (id) of the element.
[0069] ● CSS text extract...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com