Safe transfer method and system of wide area network trusted virtual machine
A technology for migrating systems and virtual machines, applied in the field of virtual machine migration, which can solve problems such as virtual machine security concerns, business failures, and complicated migration processes
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
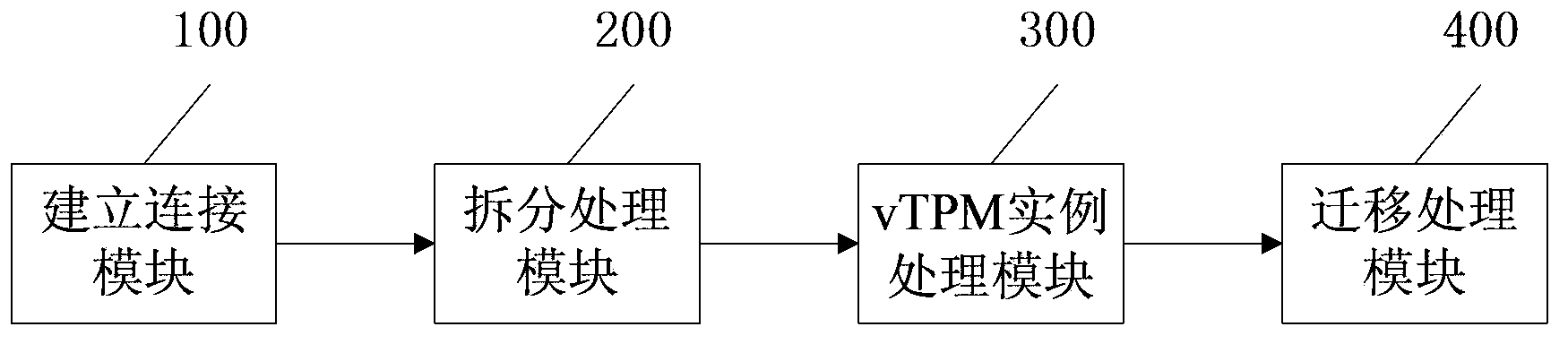
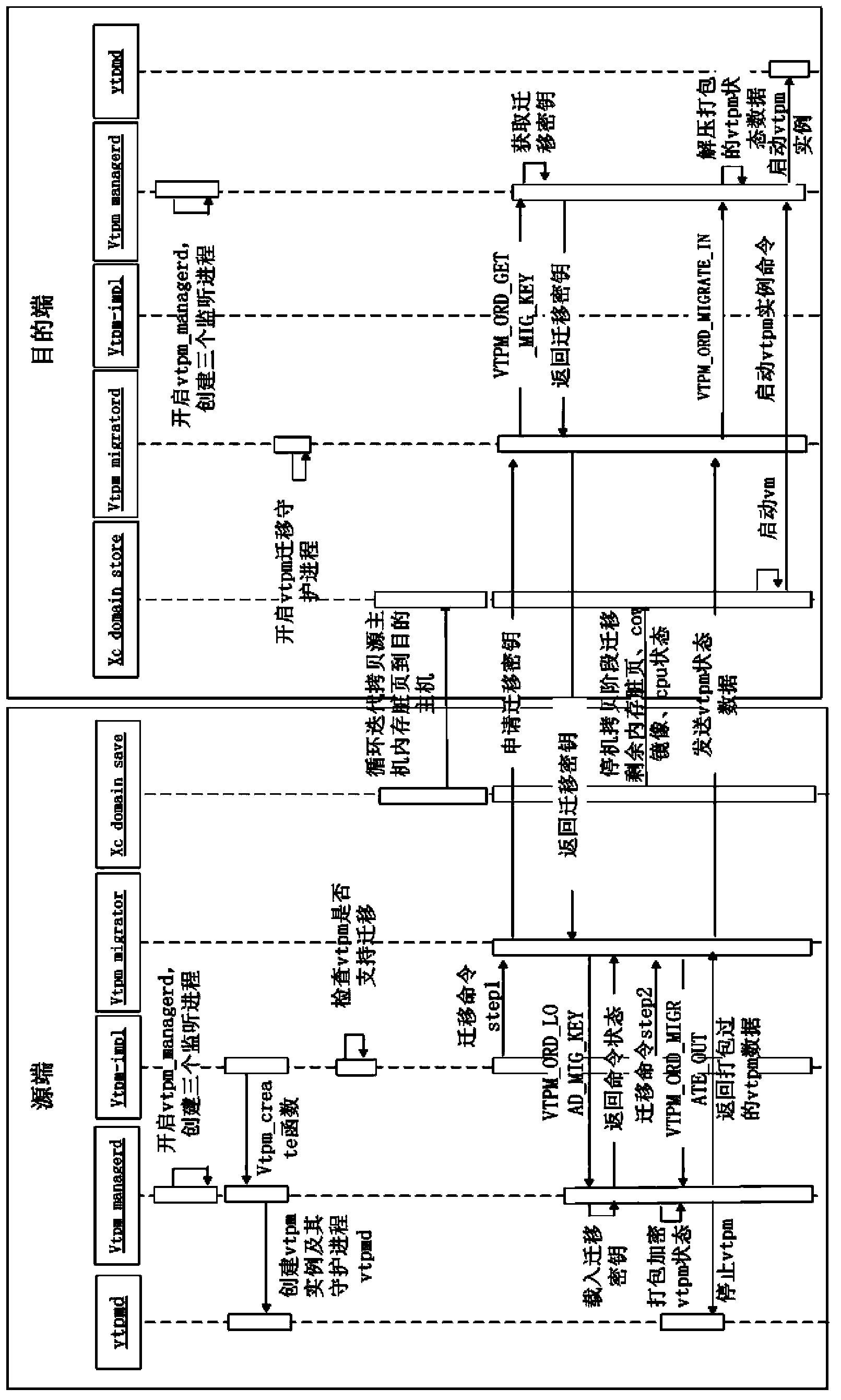
[0079] The invention combines the VPN technology with the TPM&vTPM technology, and realizes the security and credibility of the virtual machine migration terminal, access terminal, network transmission, and the entire migration chain. Compared with the security migration protocol in the prior art, this patent does not need to rebuild the security migration protocol, and directly adopts the SSL mechanism in the existing VPN (OpenVPN), which greatly reduces the difficulty of implementation and the compatibility of products. The virtualization environment is a Xen virtualization environment, and the trusted virtual machine is a virtual machine that supports the TPM trusted computing function. The safe migration refers to carrying out credible verification on the transmission end, and using the VPN security protocol to monitor the transmission process. Perform encryption processing.
[0080] figure 1 It is a flow chart of the safe migration method of the trusted virtual machine i...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com