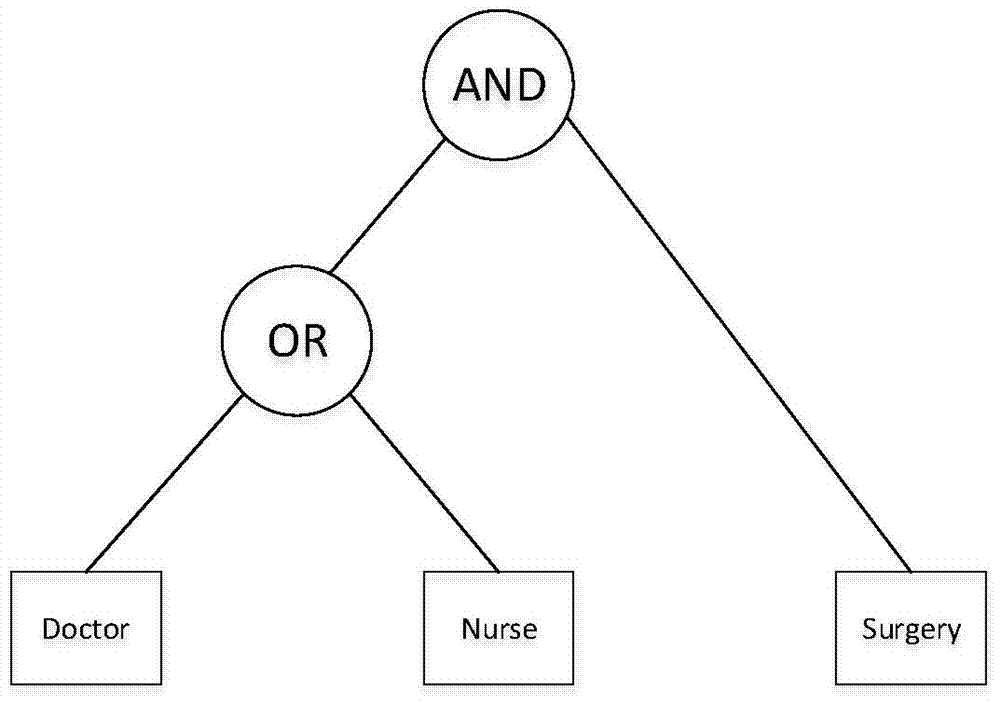
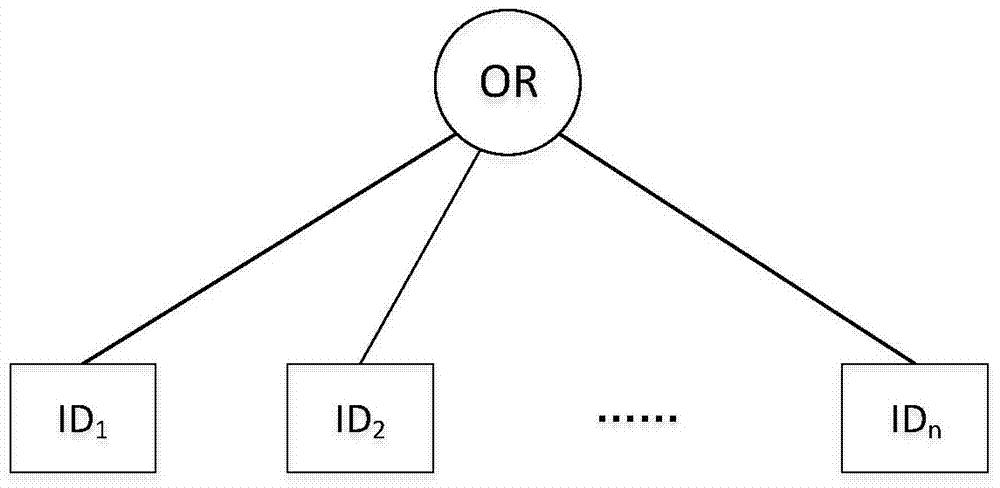
A Method for Realizing Identity-Based Broadcast Encryption by Attribute-Based Encryption of Ciphertext Policy
A technology of attribute-based encryption and broadcast encryption, which is applied in the field of cryptography in information security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
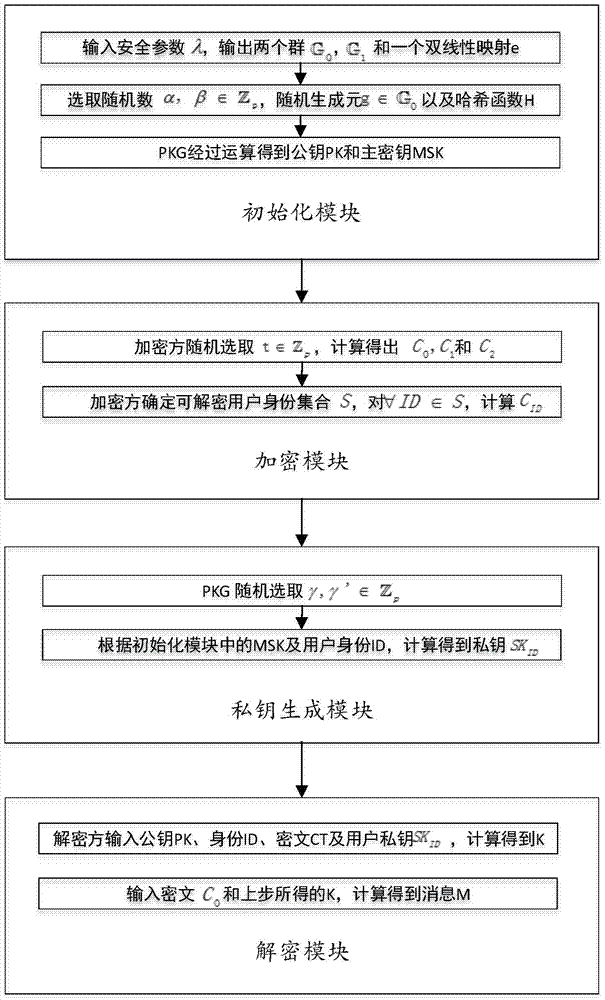
[0080] See Figure 1-3 As shown, this scheme includes four modules, which are initialization module, encryption module, private key generation module and decryption module. Such as image 3 As shown, each module is executed in the order of "initialization module" → "encryption module" → "private key generation module" → "decryption module".
[0081] A kind of method of the present invention realizes broadcast encryption by the attribute base encryption of ciphertext policy, promptly realizes the method for IBBE by CP-ABE, and its implementation steps are as follows:
[0082] Module 1: Initialize the module
[0083] In this module, PKG takes system security parameter λ as input, and outputs public key PK and master key MSK. The public key PK is public, and the master key MSK is kept by PKG. The specific implementation of the module function is divided into three steps:
[0084] Step 1: PKG first inputs the system security parameter λ, and then runs the algorithm g(1 λ ), ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com