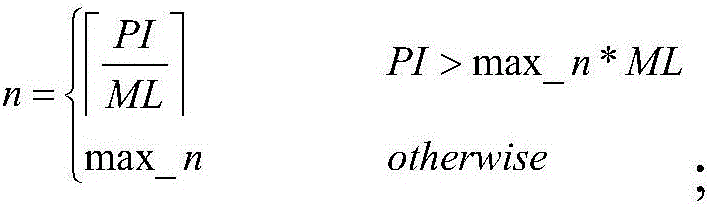Secure Code Distribution Method in Wireless Sensor Networks
A wireless sensor and security code technology, applied in network topology, wireless communication, digital data protection, etc., can solve the problems of large energy consumption, high complexity, low security, etc., and achieve the effect of reducing unnecessary transmission load and reducing load
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0047] The present invention will now be explained in detail in conjunction with the accompanying drawings and embodiments.
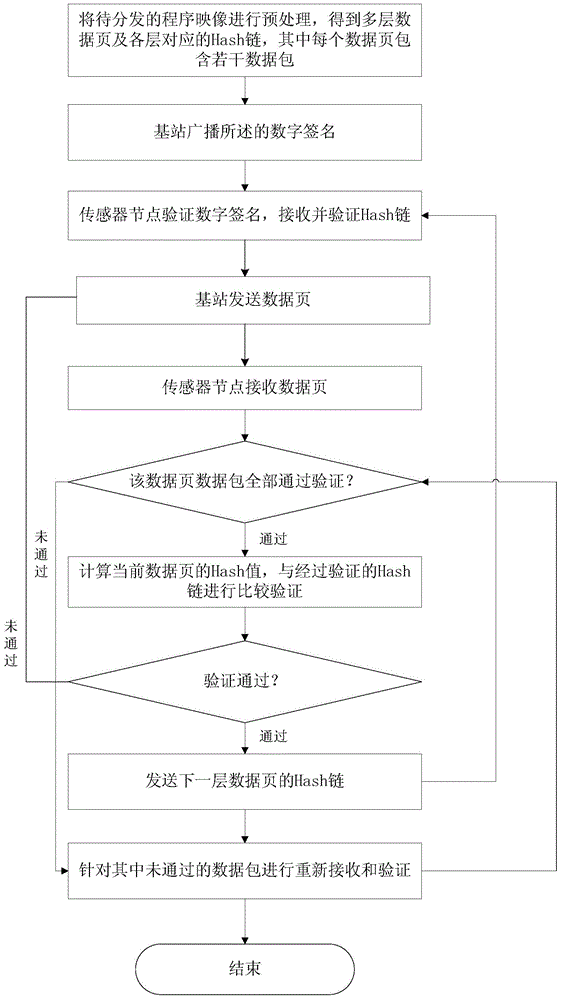
[0048] Such as figure 2 Shown, the concrete steps of the inventive method are as follows:
[0049] Step 1. The base station preprocesses the program image to be distributed to obtain multi-layer data pages and the Hash chains corresponding to each layer. Each data page contains several data packets. The first H node of the first layer Hash chain Hash value is digitally signed.
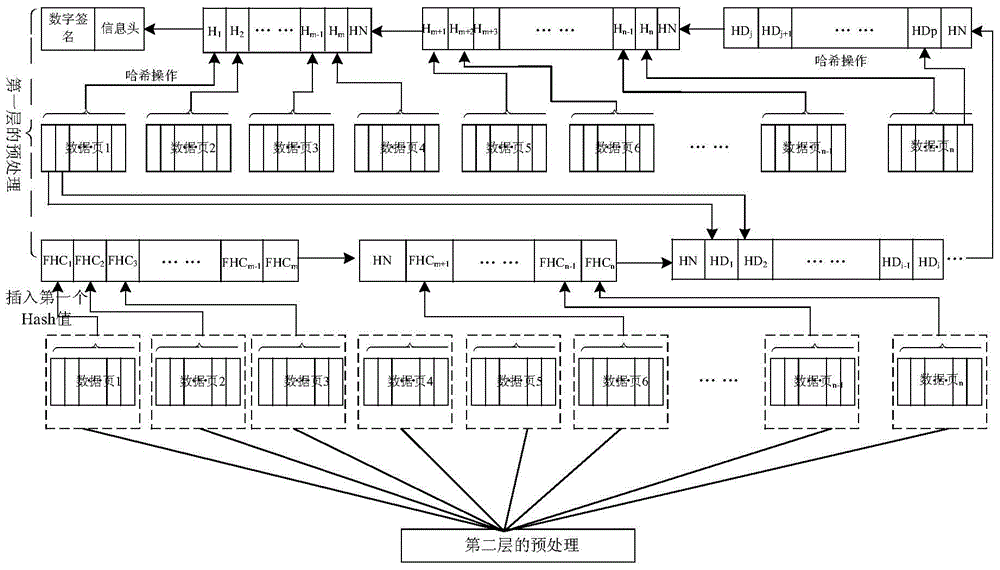
[0050] Among them, such as figure 1 As shown, the preprocessing in step 1 specifically includes the following steps:
[0051] Step 1-1, set the number of pages in the first layer and the maximum load, divide the program image into equal lengths according to the number of pages in the first layer, obtain the data pages in the first layer, calculate the Hash value of each data page, and save it Insert it into the position corresponding to the H node in the first layer Hash ch...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com