Database safety access control method based on independent authorization
A security access control and access control technology, applied in the field of database security, can solve problems such as database attacks, database vulnerabilities, and inability to control user behavior
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
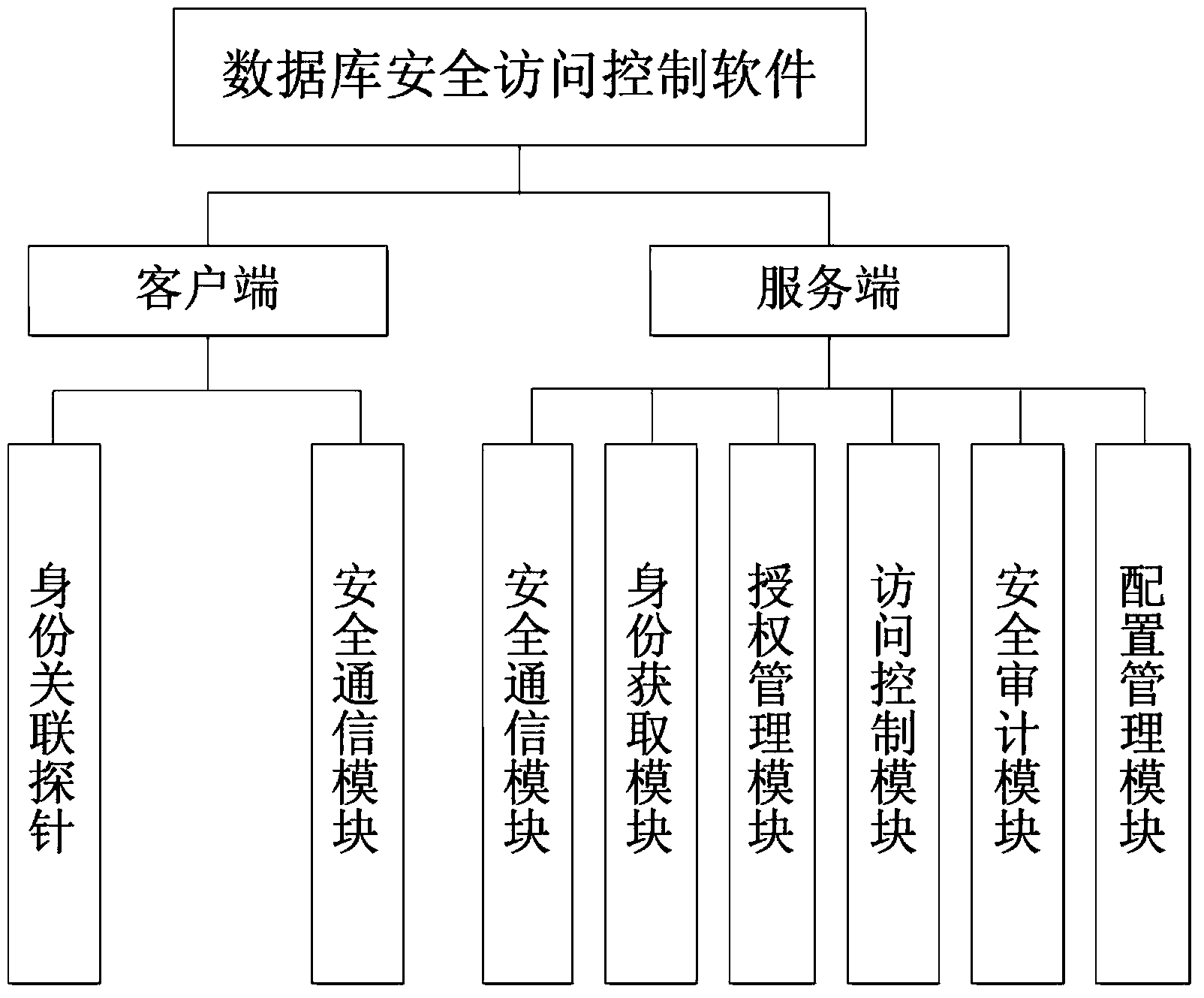
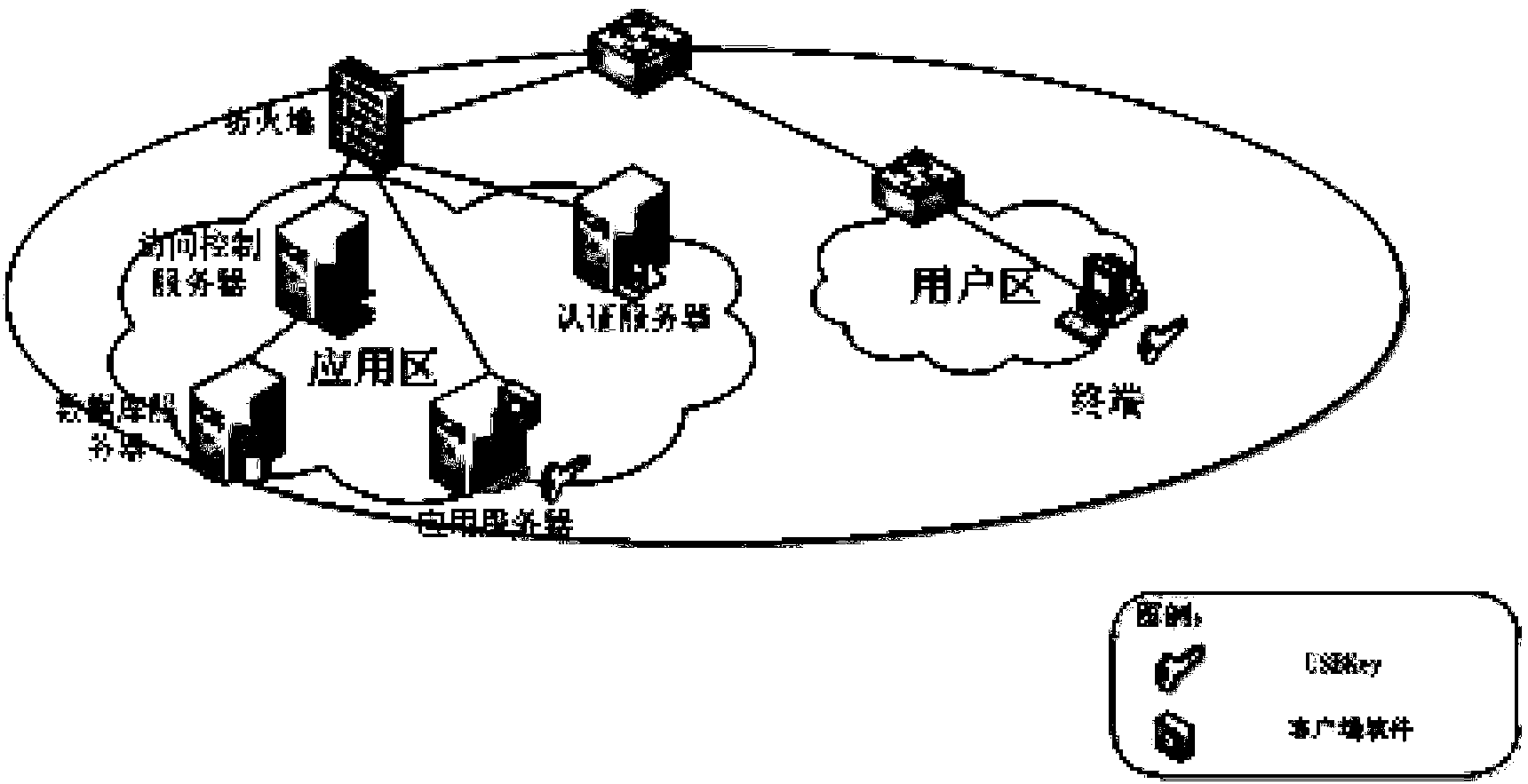
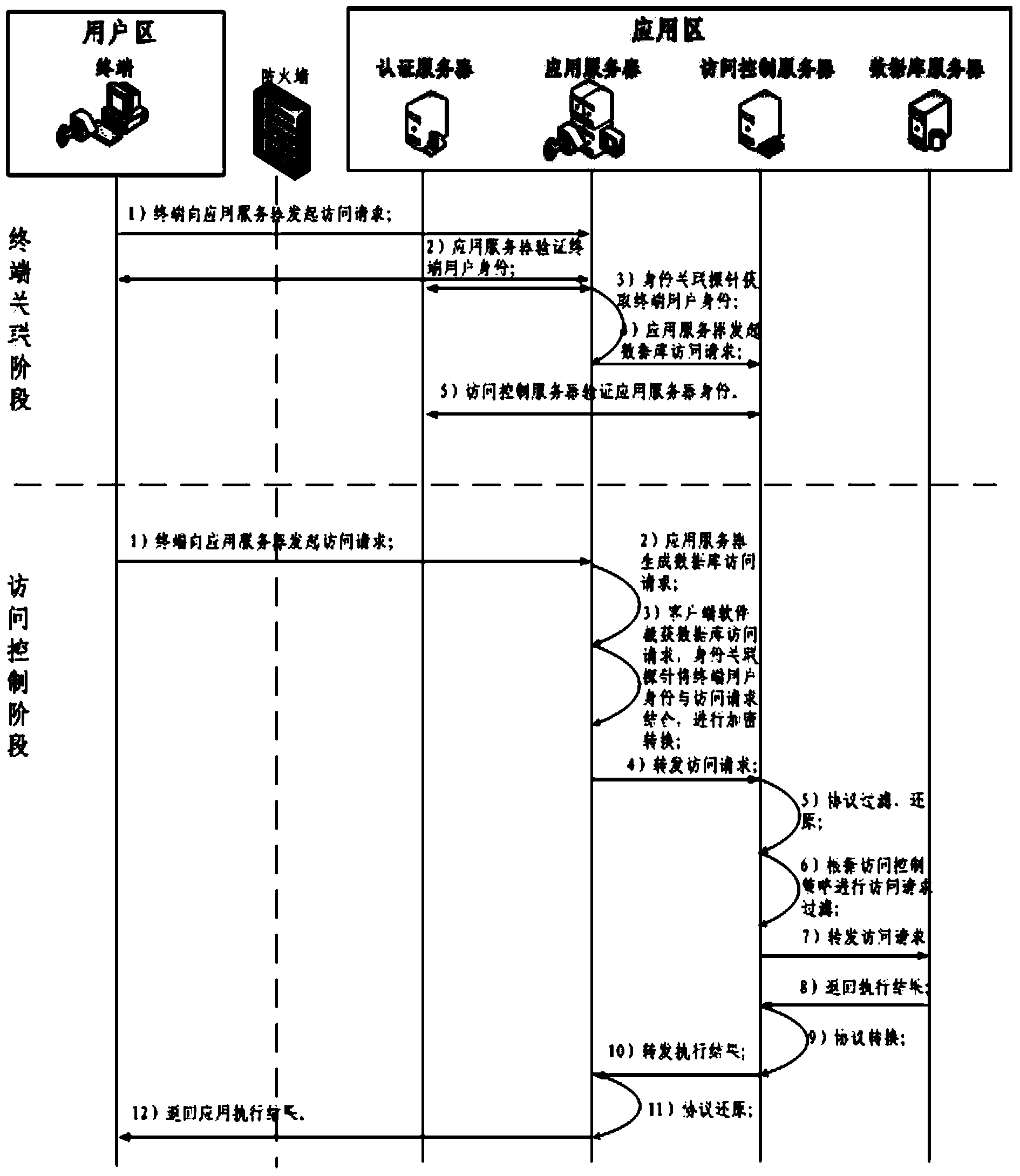
[0043] The core of the present invention is database security access control control software, such as figure 1 As shown, the software includes two parts, the client and the server, consisting of 7 modules in total.
[0044] The main functions of the seven functional modules of the database security access control software are:
[0045] Identity association probe: The identity association probe is deployed on the application server, responsible for obtaining the identity information of the front-end user, and sending the corresponding relationship between the user identity information and the access control request to the database security access control software;
[0046] Secure communication module: The secure communication module is deployed on the application server and the access control server, and is responsible for realizing secure data exchange between the application server and the database server;
[0047] Identity acquisition module: the identity acquisition...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com