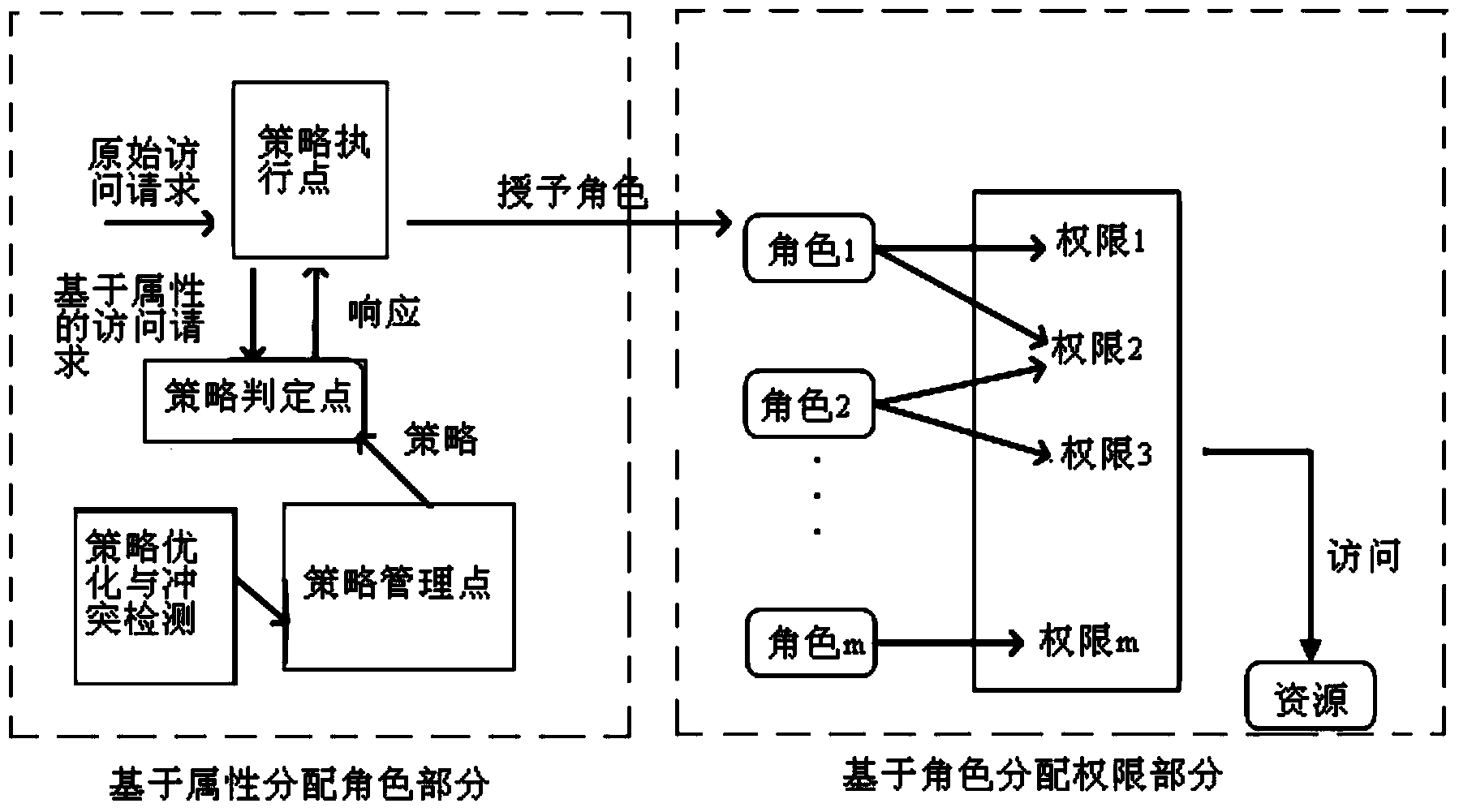
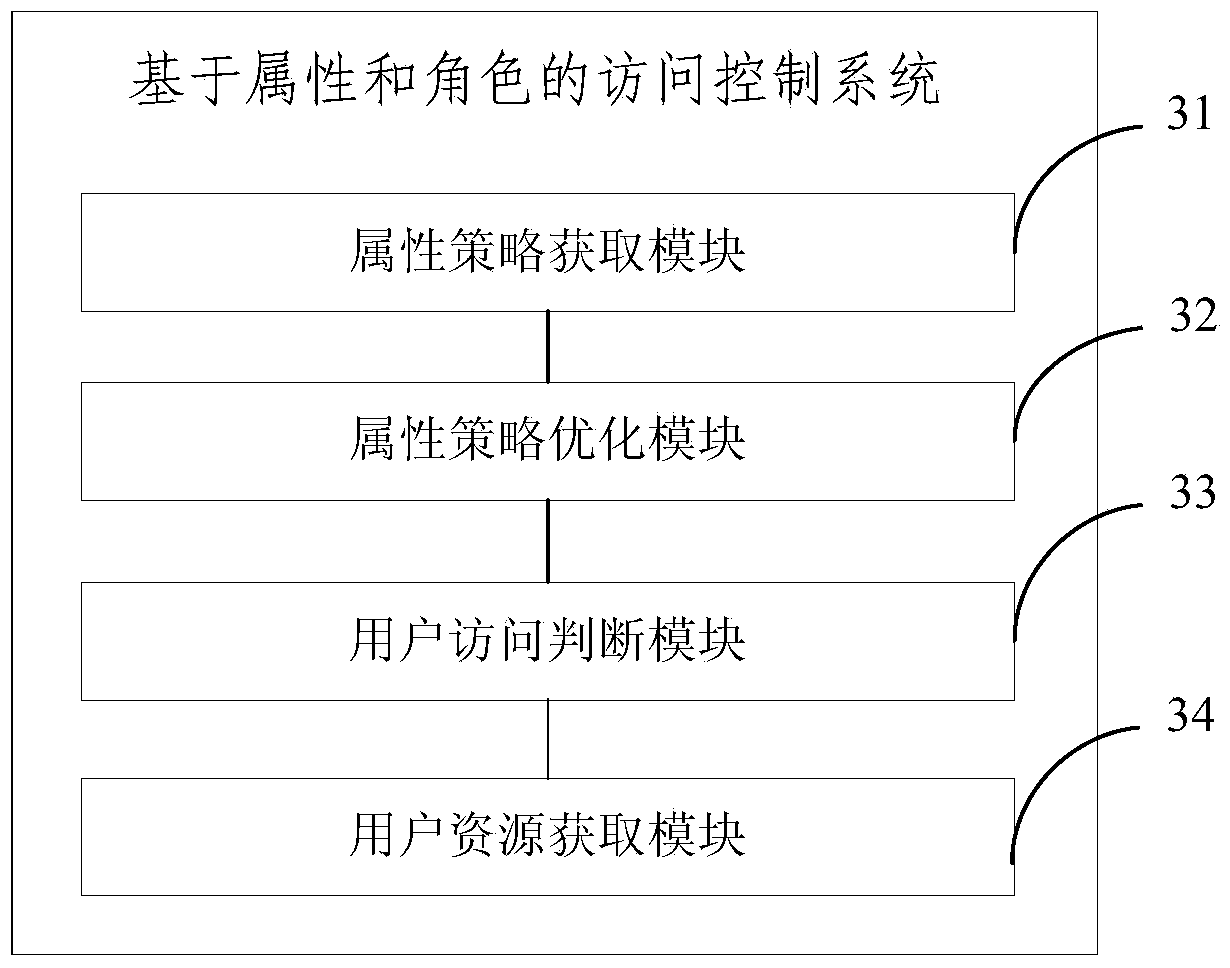
Access control method and system based on attribute and role
An access control and attribute technology, applied in the field of access control of information resources, can solve problems such as RBAC insufficiency, large-scale user dynamic change access ABAC insufficiency, etc., and achieves the effect of resolving redundancy and conflict.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0099] Application of this method in WeChat
[0100] Divide all the visitors in the "nearby people" in WeChat into five categories: contacts in the mobile phone (saved phone numbers), WeChat friends, QQ friends, the same school or work unit in WeChat as the interviewee, unfamiliar people. This results in four roles: friends, known, colleague, unknown. The order of priority is as follows Table 2 shows the priority and authority assignment of roles in WeChat:
[0101]
[0102]
[0103] (Note: Read means viewing photo logs, etc., TimeSeen means that the time of publication is visible, PlaceSeen means that the place of publication is visible, Forwarding means forwarding comments)
[0104] Table 2
[0105] According to the policy language above, the policy is constructed as follows:
[0106] Rule1: phone-number in Phone-Contacts->friends;
[0107] Rule2: WeChat-number in WeChat-friends->known;
[0108]Rule3: QQ-number in QQ-friends->known;
[0109] Rule4: place=my plac...
Embodiment 2
[0117] Application of this method in the taxi system
[0118] At present, the taxi-hailing system is widely used, but the system is simple, and generally you can only contact the customer service to call the driver of the empty car, which is very inconvenient and inflexible. But if the taxi information can be checked online, it will bring security problems. The current design is as follows: the driver's relatives can view all driver information; the driver's friends can view the current location to contact you; the operating company can view the driver's historical itinerary for unified scheduling; Check their mobile phone number for easy contact. The following table 3 shows the priority and authority assignment of roles in the taxi-hailing system.
[0119]
[0120] (Note: Real-time-location indicates the driver's real-time location, History-track indicates the historical trace, License-plate indicates the license plate, car-owner indicates the driver's personal informati...
Embodiment 3
[0133] Application of this method in online cinema
[0134] An online movie theater is currently open to the EU, US, Japan and China (other countries are not considered because of religious issues). Since China does not allow teenagers and children to surf the Internet alone, the movie theater stipulates that the role distribution of the online movie theater is as follows: Table 4
[0135]
[0136] Table 4
[0137] According to the policy language above, the policy is constructed as follows:
[0138] Rule1: age≥3 and country in{EU, America, Japan}->Child;
[0139] Rule2: age≥11 and country in{EU, America, Japan}->Juvenile;
[0140] Rule3: age≥16 and country in{EU, America, Japan, China}->Adolescent;
[0141] Rule4: age≥18 and country in{EU, America, Japan, China}->Adult;
[0142] According to the definition in the invention scheme:
[0143] (1) Rule1 and Rule2, Rule3 and Rule4 constitute exceptional conflicts;
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com