Access control system based on intelligent terminal and control method of access control system
A technology of intelligent terminal and access control system, applied in the direction of instruments, time registers, single input port/output port registers, etc., can solve the problems of lack of versatility, message cracking, and lack of control intelligence, etc., to improve security , avoid instability or damage, high reliability effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
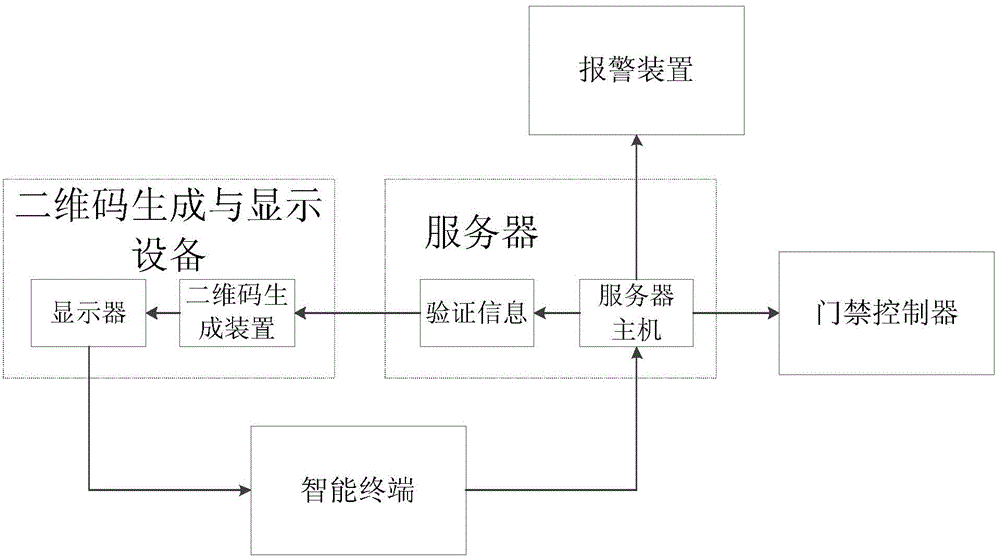
[0042] Step 1: The server host generates verification information. The verification information includes the server address domain name (or IP address), the timestamp for verifying the validity period of the verification, and the interference code. The number of characters is within 200 characters, and the server host will verify the information. Send to the QR code generating device;
[0043] Step 2: After receiving the verification information, the two-dimensional code generating device generates two-dimensional code graphics using the matrix two-dimensional code standard, and displays the two-dimensional code graphics on the display;
[0044] Step 3: The user scans the QR code on the display with the camera of the smart phone, and the smart phone prompts to scan the fingerprint, and the user collects the fingerprint through the smart phone for verification. After the user verification, the verified information is transmitted to the server host through the wireless communicat...
Embodiment 2
[0048] Step 1: The server host generates verification information. The verification information includes the server address domain name (or IP address), the timestamp for verifying the validity period of the verification, and the interference code. The number of characters is within 200 characters, and the server host will verify the information. Send to the QR code generating device;
[0049] Step 2: After receiving the verification information, the two-dimensional code generating device generates two-dimensional code graphics using the matrix two-dimensional code standard, and displays the two-dimensional code graphics on the display;
[0050] Step 3: The user uses the camera of the smartphone to scan the QR code on the display, the smartphone prompts to enter a password, and the user enters the password for verification. After the user verifies, the verified information is transmitted to the server host through the wireless communication network;
[0051] Step 4: The server...
Embodiment 3
[0054]Step 1: The server host generates verification information. The verification information includes the server address domain name (or IP address), the timestamp for verifying the validity period of the verification, and the interference code. The number of characters is within 200 characters, and the server host will verify the information. Send to the QR code generating device;
[0055] Step 2: After receiving the verification information, the two-dimensional code generating device generates two-dimensional code graphics using the matrix two-dimensional code standard, and displays the two-dimensional code graphics on the display;
[0056] Step 3: The user scans the QR code on the display with the camera of the smart phone, and the smart phone prompts to scan the fingerprint. After the user collects the fingerprint through the smart phone, the smart phone prompts to enter the password. The password is transmitted to the server host through the wireless communication netwo...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com