Secure use method of privacy data in cloud computation
A private data and cloud computing technology, which is applied in computer security devices, computing, electronic digital data processing, etc., can solve the problems of loss of user privacy data, failure to provide settings and management, loss of data consistency between end users and servers, etc. To achieve the effect of preventing illegal use and dissemination
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0051] The specific implementation manners of the present invention will be further described in detail below in conjunction with the drawings and examples.
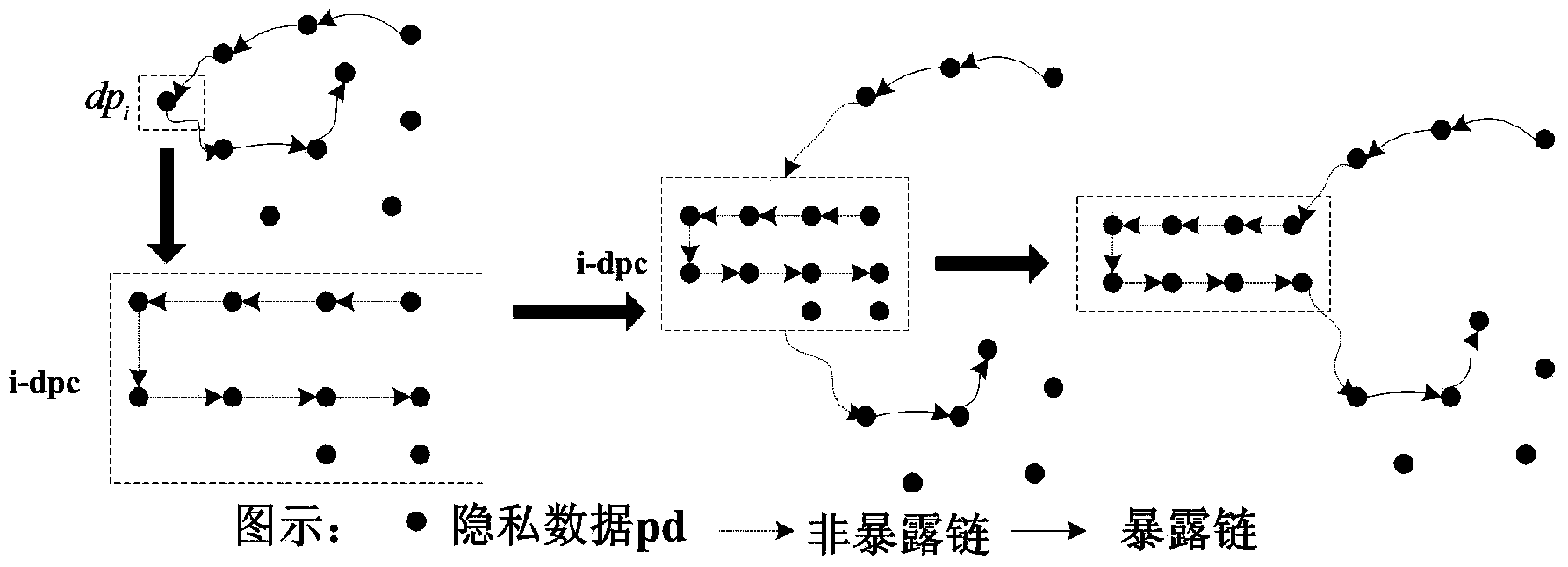
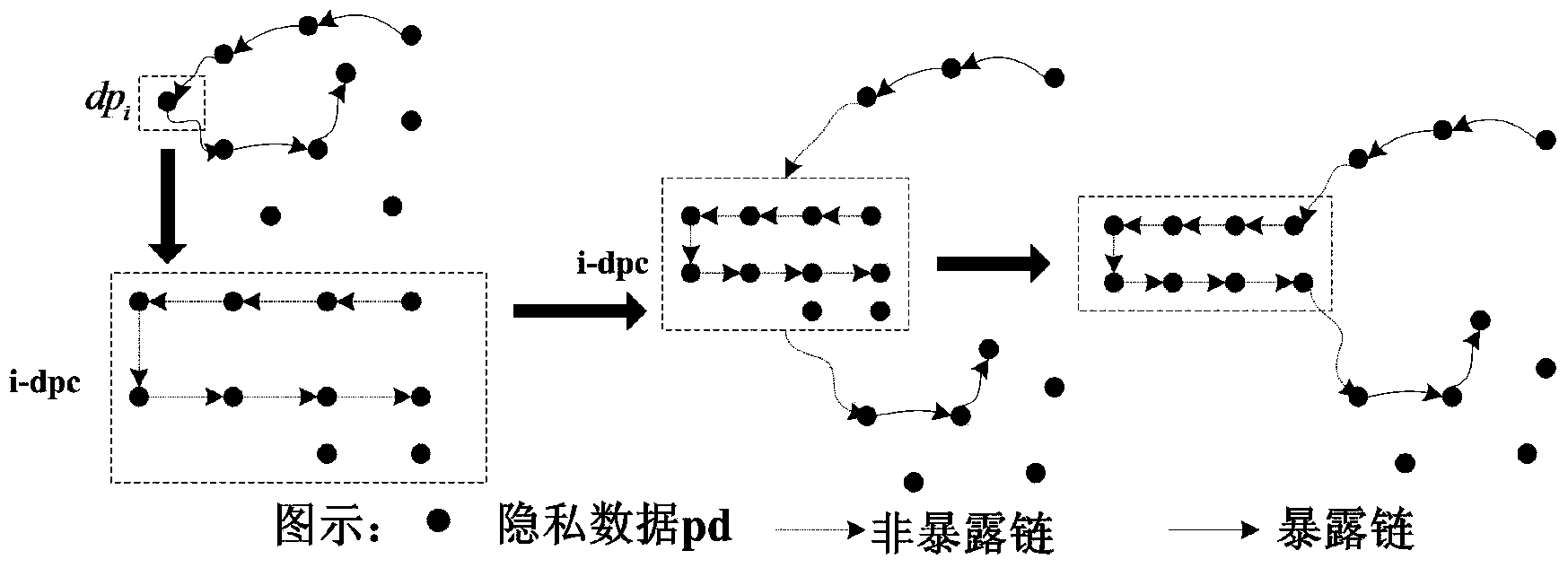
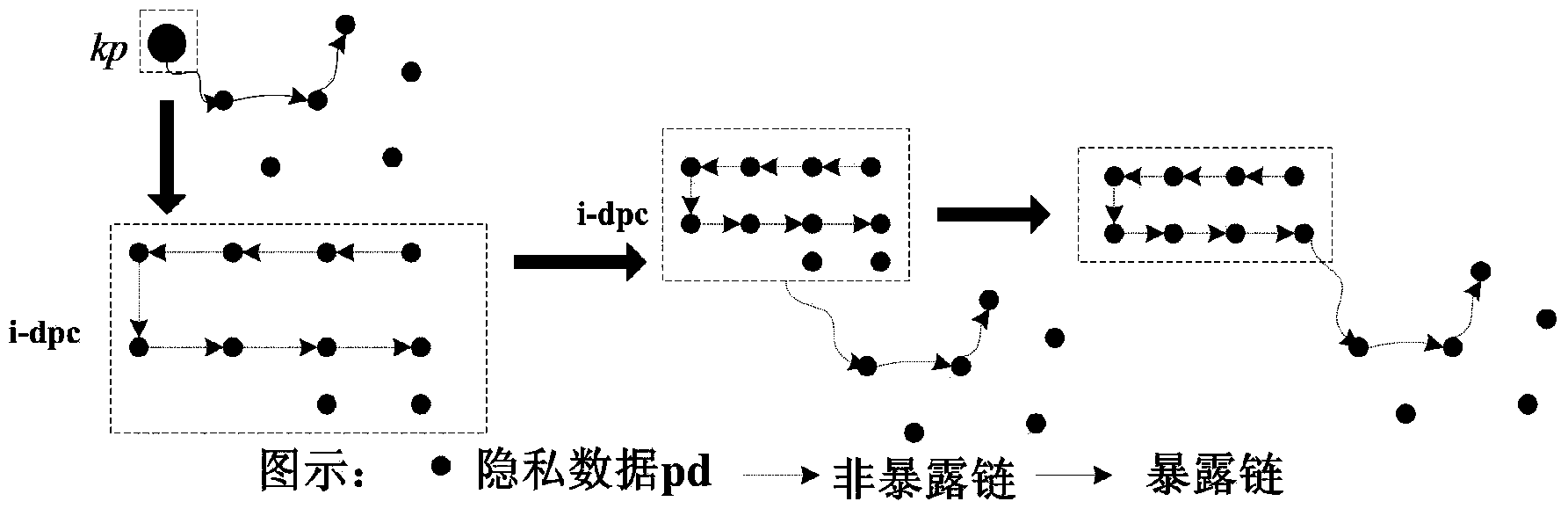
[0052] A method for safely using private data in cloud computing proposed by the present invention, its specific implementation steps include: classification of user private data, detection of exposure chains and key private data, protection of discrete private data and protection of continuous private data, After the detection of the exposure chain and key privacy data in the first stage and the reorganization of the exposure chain and key privacy data as the root node in the second stage, the continuous privacy data is converted into discrete privacy data to achieve the result of protecting the user's personal privacy information .
[0053] A method for safely using private data in cloud computing proposed by the present invention, the key links and application diagrams in its specific implementation steps are sh...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com