Implementation method of high security application system based on trusted execution environment
An execution environment and security application technology, applied in security devices, wireless communications, electrical components, etc., can solve problems such as insufficient security level, application system Trojan threat, and difficulty in ensuring complete isolation, achieving a short development cycle and high security. The effect of high and low build complexity
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0035] In order to make the objectives, advantages and technical solutions of the present invention more clear, the present invention will be further described in detail below through specific implementation and in conjunction with the accompanying drawings.
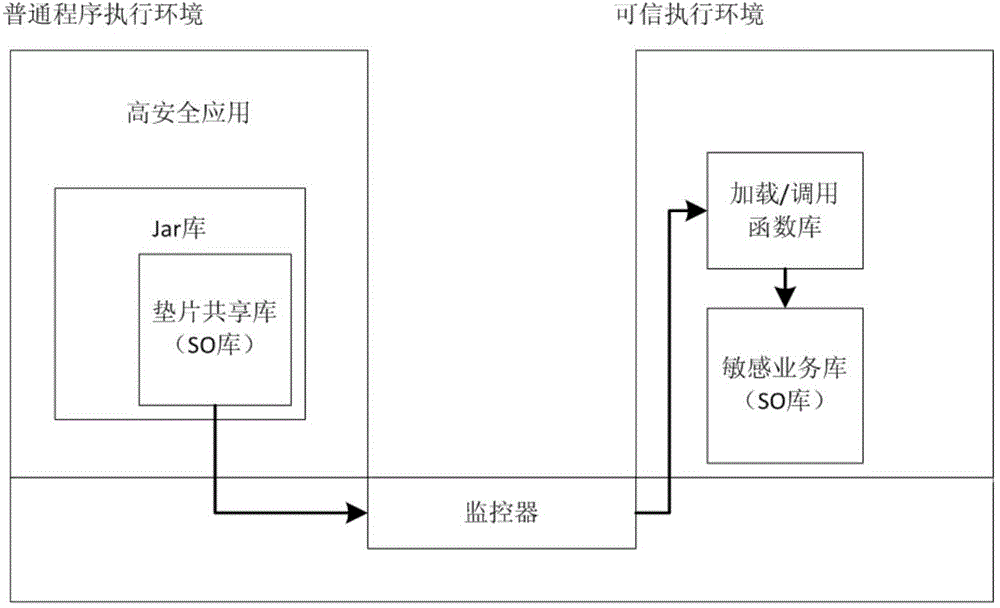
[0036] for figure 1 Describes the overall structure of the implementation of the program as a whole, mainly including the following three parts.
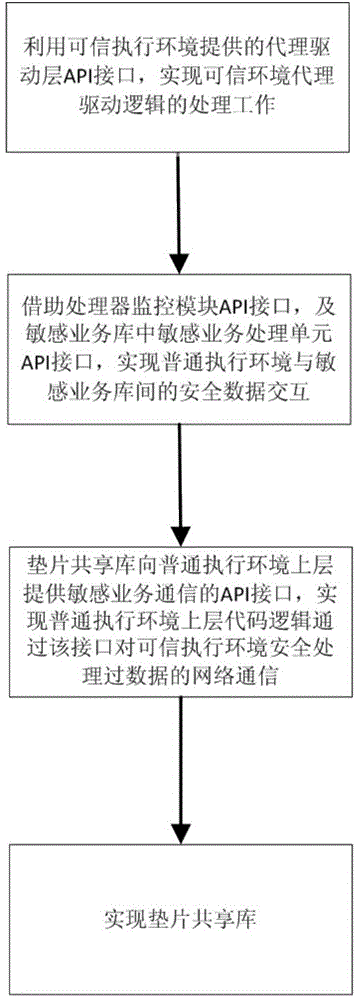
[0037] 1. Implementation method of sensitive business library based on trusted execution environment security application system
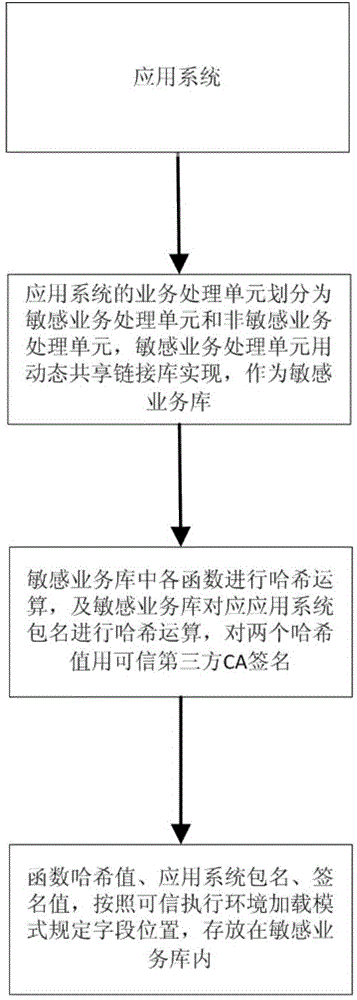
[0038] The developer of the high-security application will apply the sensitive business processing unit and the non-sensitive business processing unit of the application system. The non-sensitive business processing unit refers to the code logic for processing non-core data, and the sensitive business processing unit is the code logic for processing core data. The sensitive business library is signed by a trusted third-party CA, so as to realize t...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com