System reloading based mimicry safety implementation system and method
A technology for implementing systems and methods, applied in computer security devices, instruments, calculations, etc., can solve problems such as hacker breakthroughs and severe problems, and achieve the effects of improving security and reliability, increasing the difficulty and cost of hacking attacks
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0027] In order to make the object, technical solution and advantages of the present invention clearer, the present invention will be further described in detail below in conjunction with the accompanying drawings.
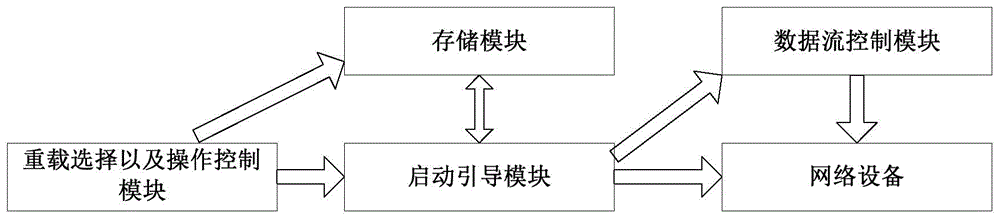
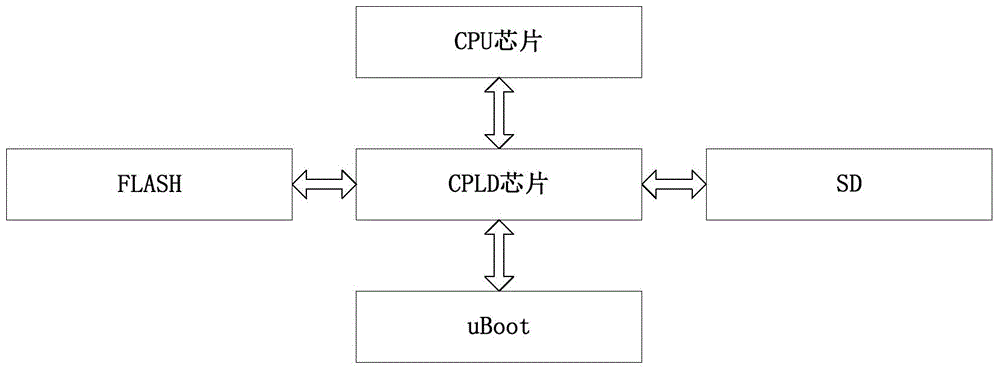
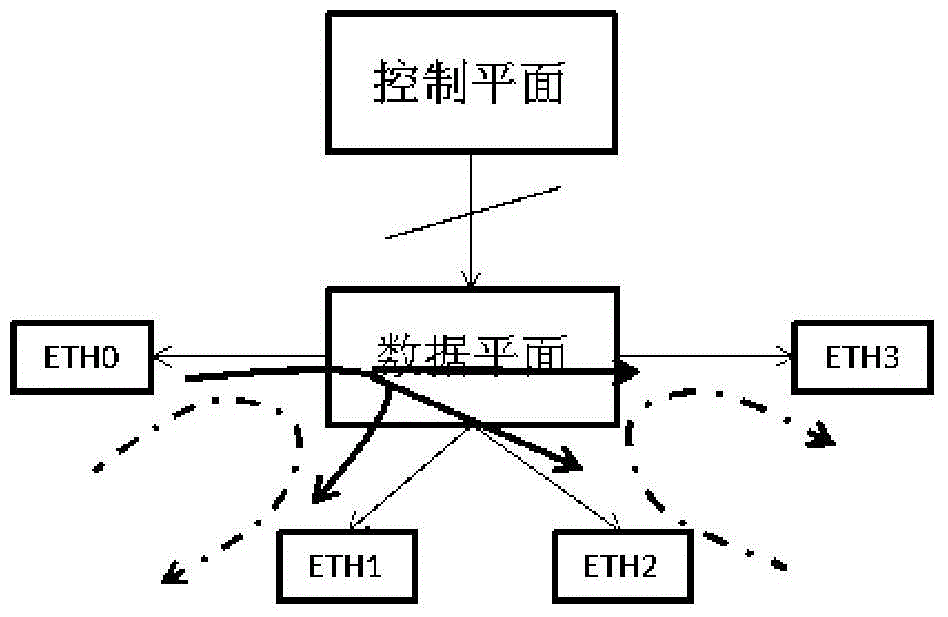
[0028] In view of the fact that most of the existing network devices or systems are a single fixed operating system, the methods or technologies used to defend against external attacks are all defenses or vulnerability patches for known backdoors or vulnerabilities, and there is a certain degree of lag, inactivity or It is called passive defense. In order to effectively solve the problems in the above-mentioned passive defense form, the present invention proposes a system and method for implementing system overloading based on the principle of irregular and non-deterministic replacement of various operating systems.
[0029] The present invention actively defends against unknown backdoors and loopholes through mimic security. Mimicry is the phenomenon in which one...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com