A user-based method for controlling the access authority of operating system peripherals
An operating system and peripheral access technology, applied in the field of computer security, can solve the problems of indistinguishable control, single control method, coarse control granularity, etc., and achieve the effect of strong peripheral recognition ability, strong scalability and good stability
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
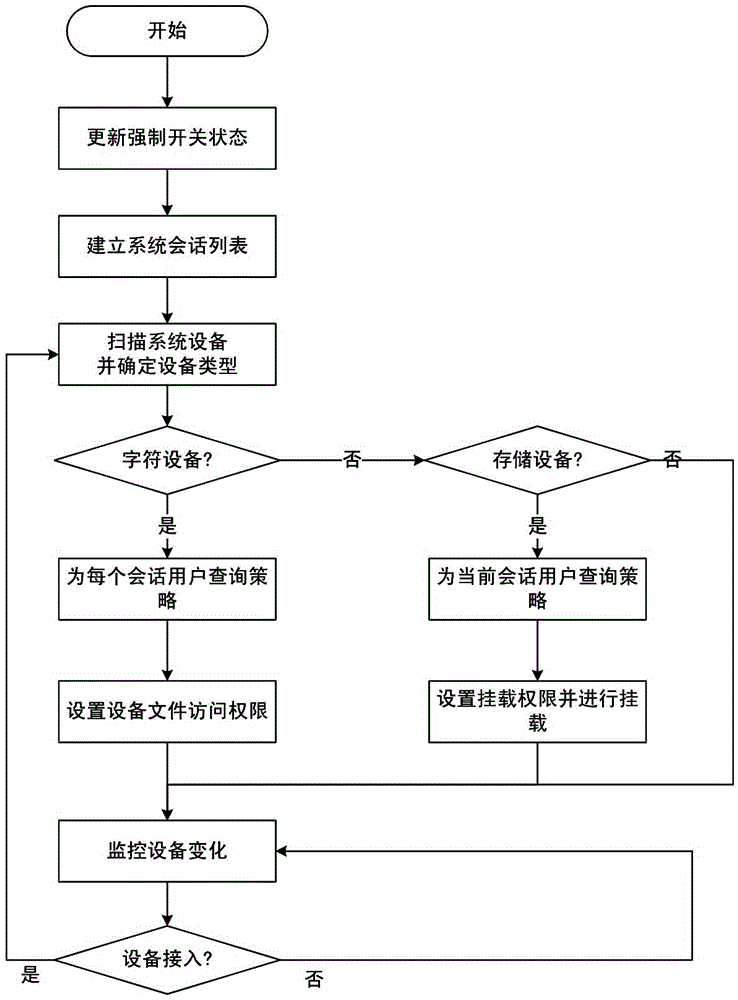
[0043] Such as figure 1 As shown, the implementation steps of the user-based operating system peripheral access authority control method in this embodiment are as follows:
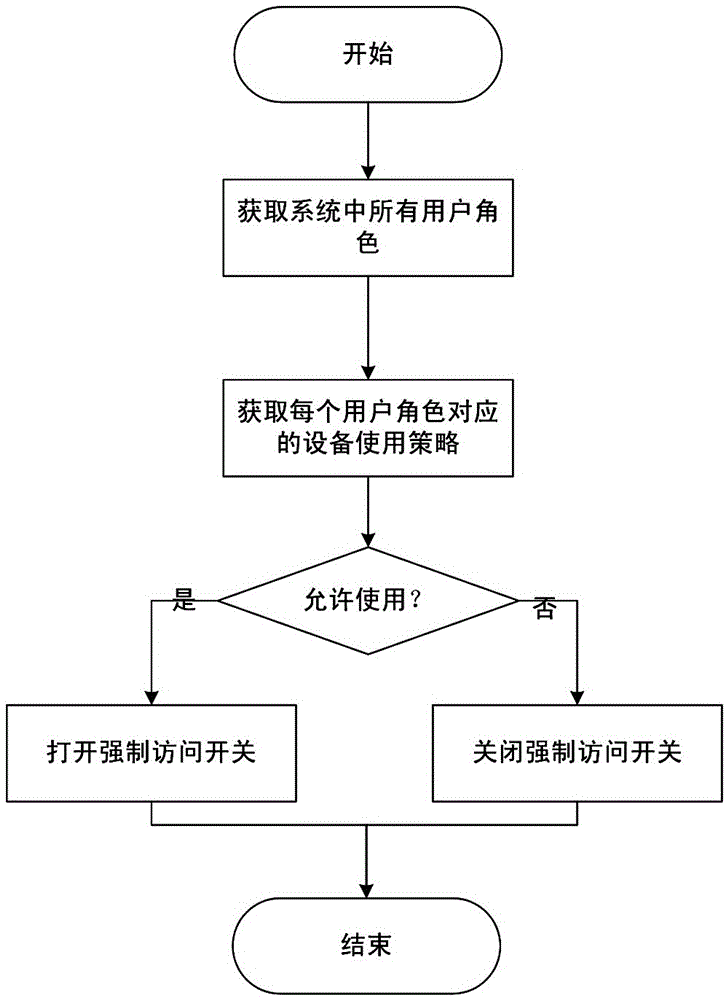
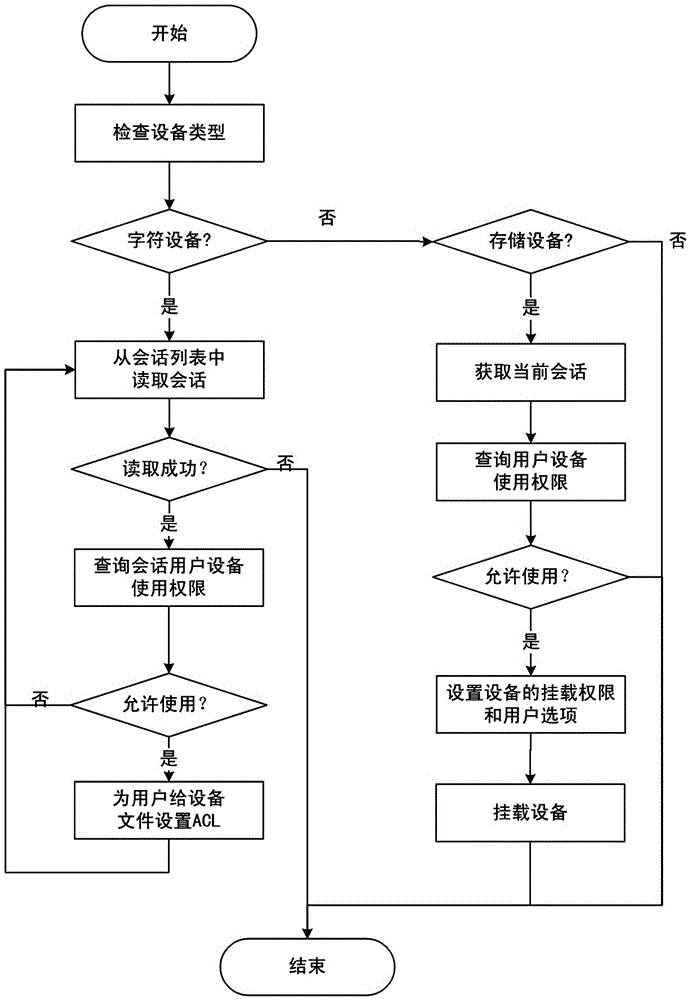
[0044] 1) Establish a device feature database for classifying peripherals; classify users in the operating system into different user roles, establish a device usage policy for configuring whether each user role is allowed to use a specified device type, and control whether Each user role is allowed to use the mandatory access control switch of the specified device type, respectively establishes a user access control list including whether to enable user control and the user's access rights to the specified device type, including whether to enable user group control and the user group's access to the specified device type The user group access control list of access rights information, the user role access control list including whether user role control is enabled and the access rights information of the ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com