Random encryption and double-blind confidential matching method for images
A random encryption and matching method technology, which is applied in image enhancement, image analysis, image data processing, etc., can solve the problems of strong random noise, difficult to identify images, etc., and achieve the effect of high accuracy and good confidentiality
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0040] An image random encryption double-blind confidential matching method, the method includes the following steps:
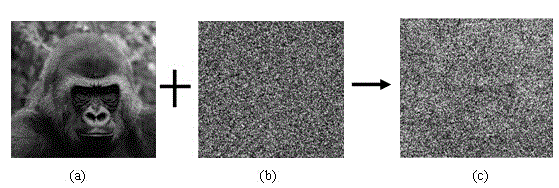
[0041] (1) In the terminal A, the target image matrix Y to be matched is added to the random noise matrix N for encryption to obtain the encrypted target image matrix Y*=Y+N to be matched; the encryption effect is as follows figure 1 Shown: figure 1 (a) is the original image, figure 1 (b) is the image corresponding to the noise, figure 1 (c) for figure 1 (a) plus figure 1 (b) the resulting encrypted image;
[0042] (2) set up a database with M floating image matrices in terminal B, for the ith floating image matrix X i , adding random noise matrix N i , perform random encryption to get the encrypted floating image matrix X 0 i =X i +N i , i=1, 2, ..., M, forming an encrypted floating image matrix database;
[0043] (3) The encrypted target image matrix Y to be matched in terminal A * send to terminal B;
[0044] (4) In terminal B, the encrypted t...
Embodiment 2
[0049] An image random encryption double-blind confidential matching method, the method includes the following steps:
[0050] (1) Establish a database with 20 floating image matrices in terminal B, for the ith floating image matrix X i , adding Gauss noise N with mean value 0 and variance σ2=3002 i , perform random encryption to get the encrypted floating image matrix X 0 i =X i +N i , i=1, 2, ..., 20, after all 20 floating image matrices are encrypted, an encrypted floating image matrix database can be obtained;
[0051] (2) In terminal A, add the target image matrix Y to be matched with a mean value of 0 and a variance of σ 2=300 2 The Gauss noise N of N is randomly encrypted to obtain the encrypted target image matrix Y to be matched;
[0052] (3) Send the encrypted target image matrix Y in the terminal A to the terminal B;
[0053] (4) In terminal B, the encrypted target image matrix Y to be matched and the encrypted floating image matrix X in the image database ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com