Crowd-sourced content delivery network system, method and device
A content distribution network and most of the technologies, which are applied in the field of crowdsourcing content distribution network, can solve the problems that CDN and P2P systems cannot be seamlessly integrated and flexible scheduling, high CDN operation and use costs, bandwidth and processing capacity bottlenecks, etc., to achieve Low power consumption, reduced energy consumption, and optimized flow effects
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
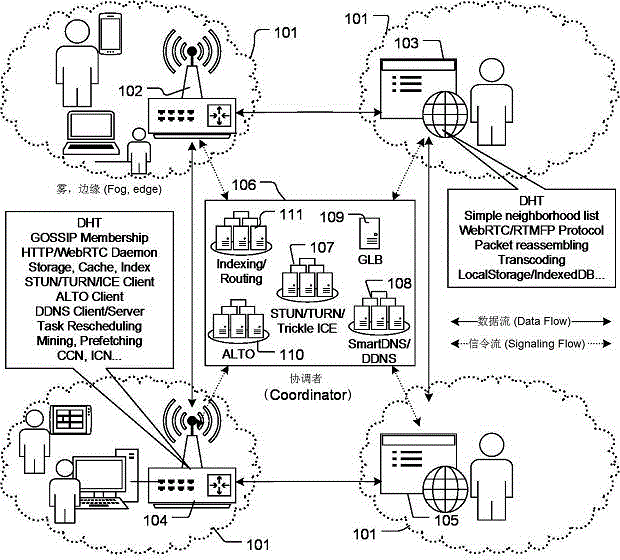
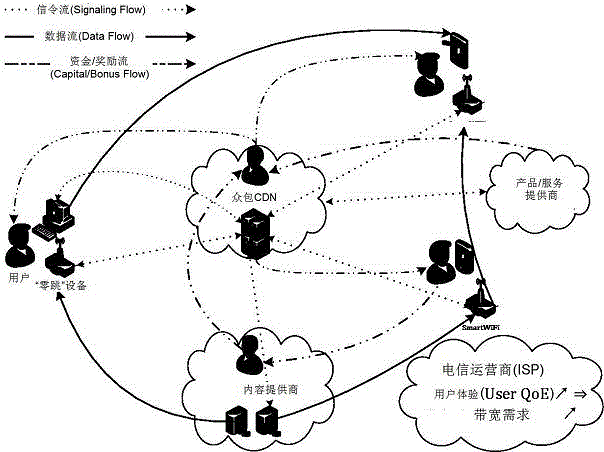
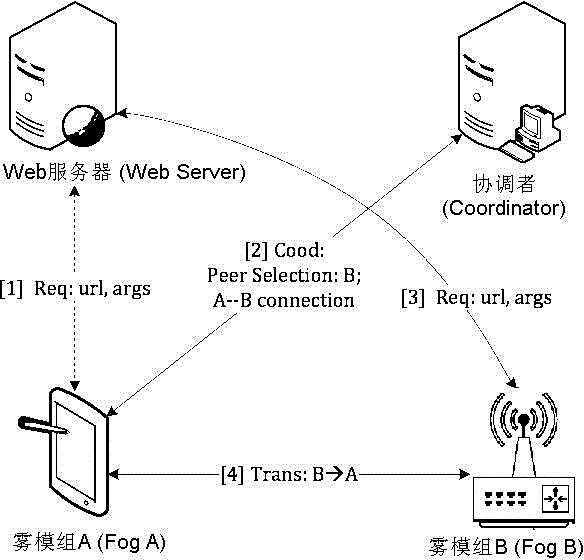
[0039] In order to further set forth the technical means and effects that the present invention takes to reach the intended purpose of the invention, the following combination Attached picture And the preferred embodiment, the specific implementation, method, steps and effects of the crowdsourcing content distribution network proposed according to the present invention are described in detail below.
[0040] Regarding the aforementioned and other technical contents, characteristics and effects of the present invention, they are referred to below picture The detailed description of the preferred embodiment of the formula will appear clearly. Through the description of specific implementation methods, when the technical means and effects adopted by the present invention to achieve the intended purpose can be understood more deeply and specifically, however, Attached picture The formulas are provided for reference and illustration only, and are not intended to limit the pre...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com