Security data reporting method and security data reporting system on basis of Hash trees and anonymity technologies
A technology for secure data and security parameters, applied in transmission systems, digital data protection, data processing applications, etc., can solve problems such as not supporting flexibility, autonomy, theoretical methods not suitable for practical application environments, complex computing and communication overhead, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
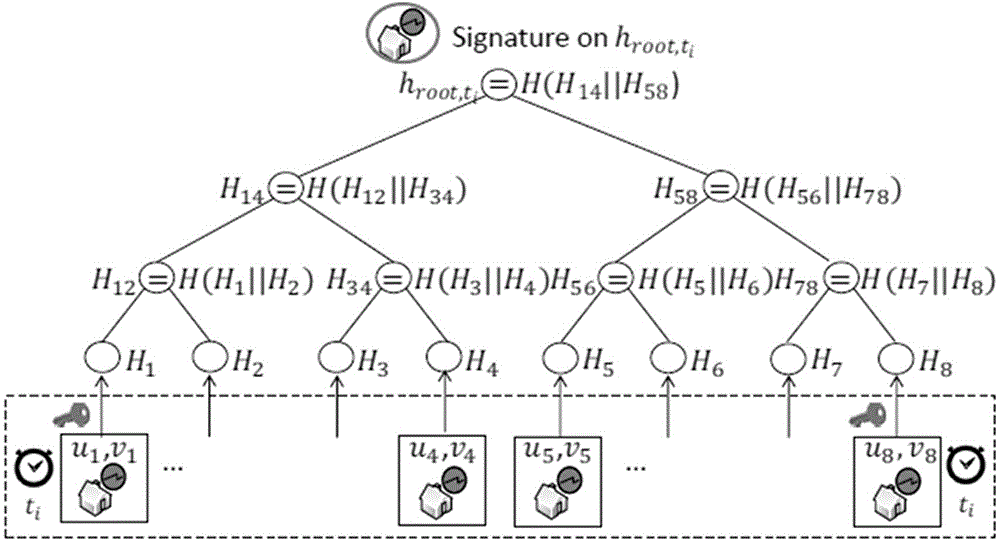
[0093] The present invention will be further described below in conjunction with accompanying drawing.
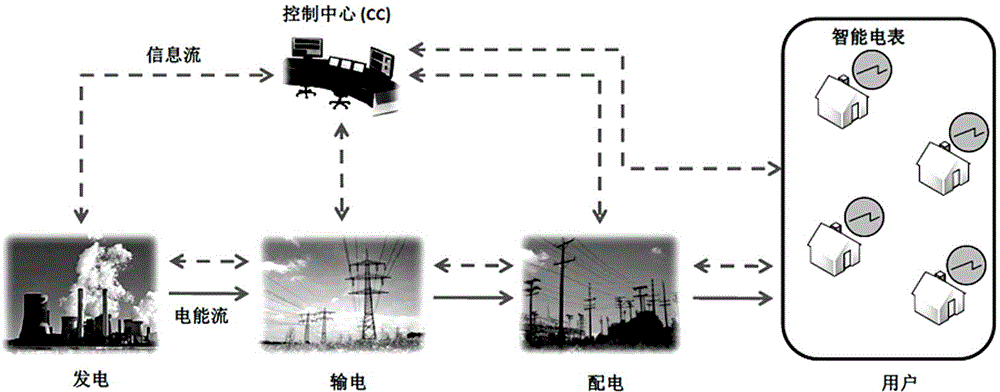
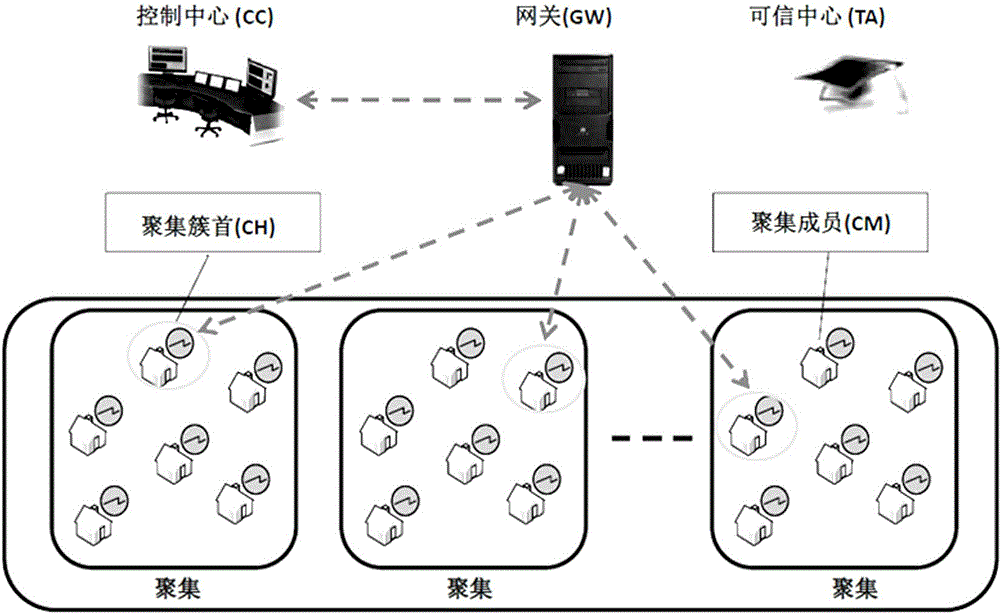
[0094] Such as figure 2 As shown, the security data reporting method and the overall system architecture based on hash tree and anonymous technology of the present invention include the following four participants:
[0095] (1) Trusted Authority (TA for short):
[0096] TA is a credible authority center with strong computing power and is responsible for managing the entire system.
[0097] (2) Control Center (Control Center, referred to as CC):
[0098] CC has high reliability and is responsible for collecting, processing and analyzing real-time power consumption data of each user, and providing reliable services for the smart grid.
[0099] (3) Gateway (Gateway, referred to as GW):
[0100] The GW has a strong computing capability and is used to connect the TA and the RA. The main functions of GW include two aspects:
[0101] First, the data collection function is r...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com