Method for establishing safety management view of full life cycle of unstructured data
An unstructured data, full life cycle technology, applied in the field of data security, can solve the problems of lack of data security management view, wide distribution of unstructured data, difficult data leakage and other security emergencies tracking and traceability, to improve accuracy Sexuality and real-time effects
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
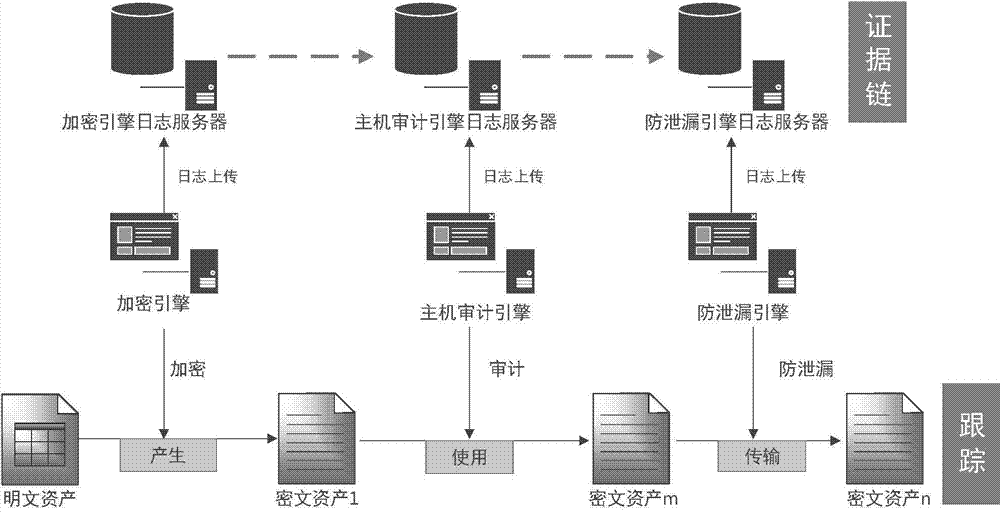
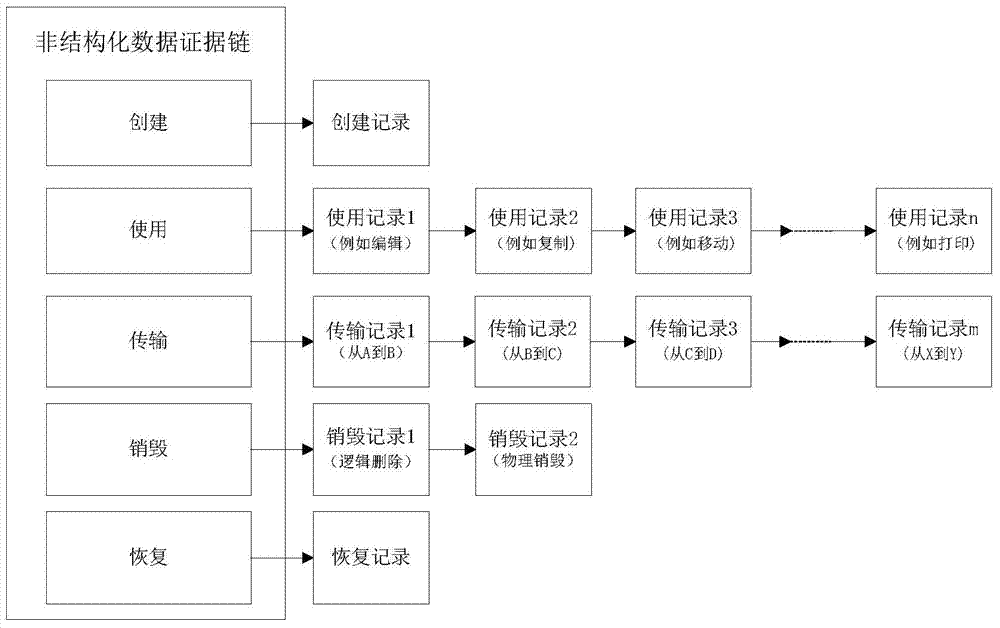
[0033] Embodiment of the present invention: a method for establishing a security management view of the whole life cycle of unstructured data, such as figure 1 As shown, the design is mainly carried out from two aspects of data tracking and evidence collection: First, record the data operation behavior of unstructured data files in the stages of creation, storage, use, transmission, destruction and recovery, and store them as log audit records. Track the data; then, read the log audit records of the unstructured data files in the stages of creation, storage, use, transmission, destruction and recovery, analyze the data operation behavior that violates the security policy, generate an analysis report, and complete the analysis Data forensics; finally, establish a full life cycle security management view of unstructured data (such as Figure 6 As shown), it shows the information of each stage of data creation, circulation, operation, and destruction, and provides analysis basis ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com