Method for dynamically detecting malicious behavior in Android App (Application)
A technology of dynamic detection and behavior, applied in the field of mobile Internet, can solve the problems of consuming system resources and unable to guarantee the coverage of sensitive behaviors, and achieve the effect of improving accuracy, overcoming the low coverage rate of dynamic detection, and facilitating testing
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
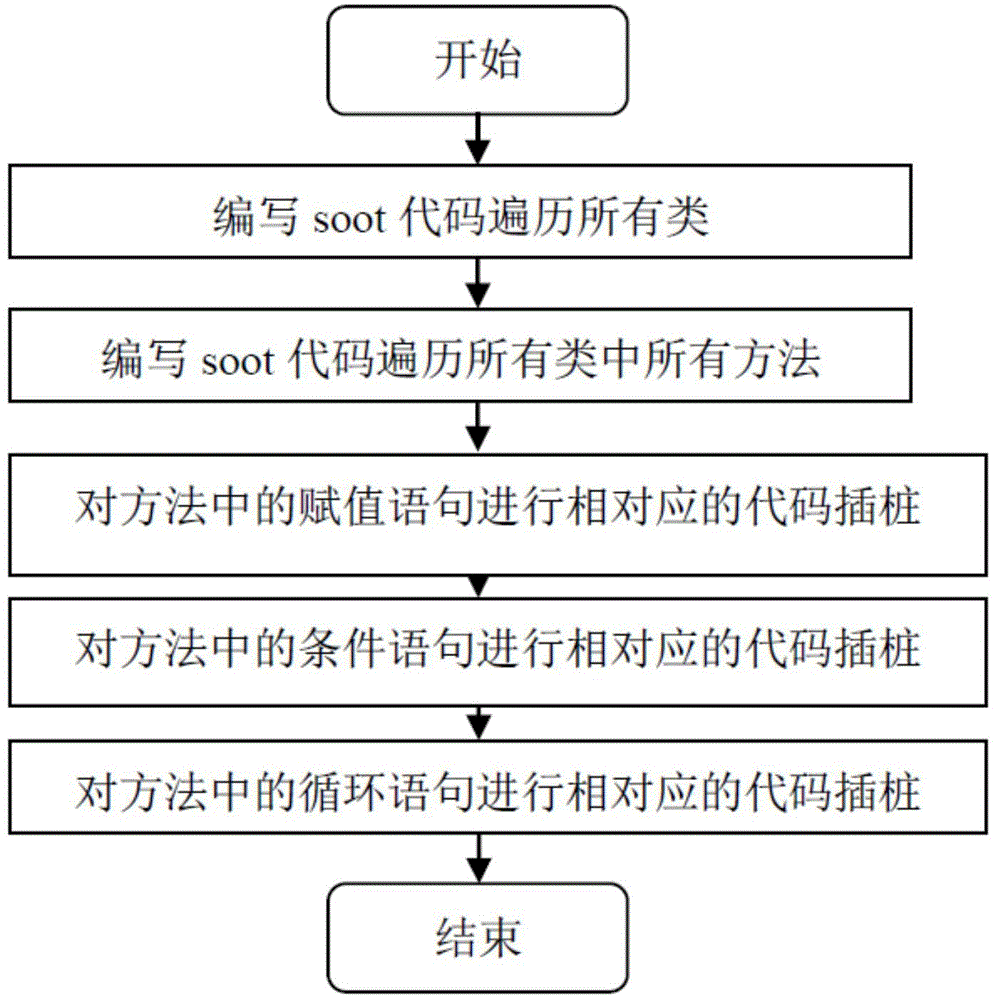
[0046] The present invention will be described in further detail below in conjunction with the accompanying drawings and embodiments.
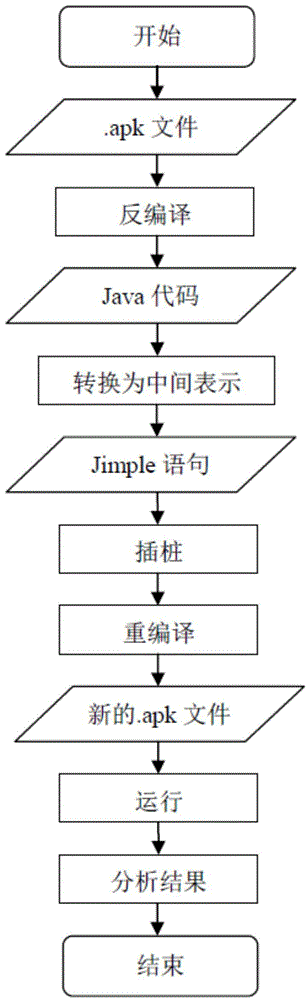
[0047] The general process of the preferred embodiment of the inventive method is as figure 1 As shown, the implementation steps are:
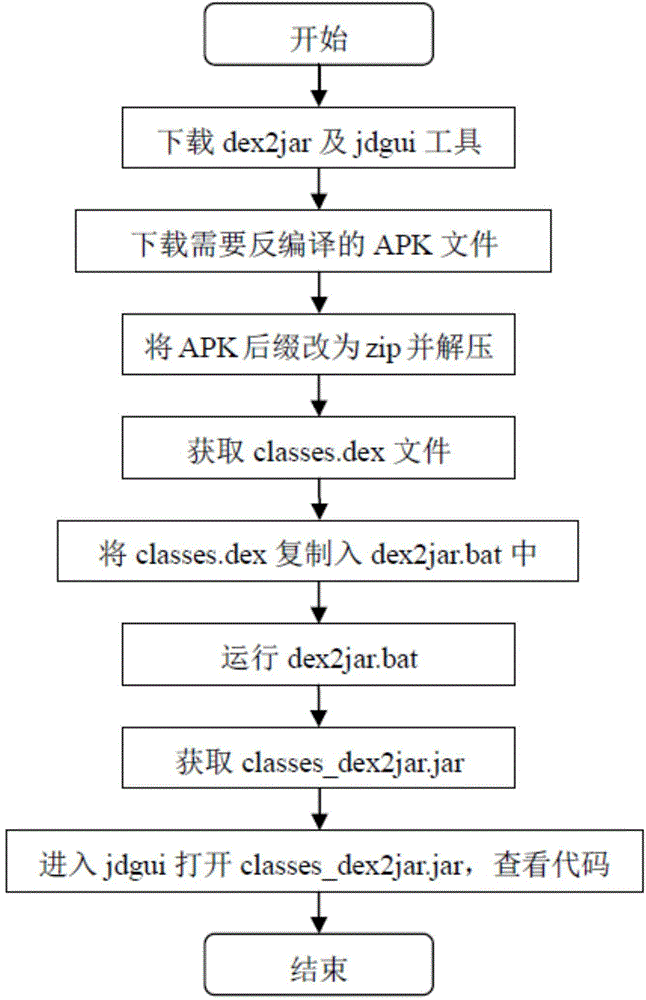
[0048] 1. Convert the APK package of the Android application program into the corresponding Java code (the specific flow chart is as follows figure 2 shown):
[0049] Step 1.1) download the APK file that needs to analyze the Android application;
[0050] Step 1.2) Change the suffix of the APK file to zip and decompress it to get the classes.dex;
[0051] Step 1.3) Copy classes.dex to the directory where dex2jar.bat is located;
[0052] Step 1.4) Locate the directory where dex2jar.bat is located under the command line, run dex2jar.batclasses.dex, and generate classes_dex2jar.jar;
[0053] Step 1.5) Enter the jdgui folder and double-click jd-gui.exe, open the jar package classes_dex2jar.jar generated above, ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com