Intrusive type grey box assembly validation method based on model
A verification method and intrusive technology, applied in program control devices, software testing/debugging, etc., can solve the problems of limited number of components, difficult application, and difficulty in formally describing the requirements of push point components, so as to increase the matching degree. , the effect of improving development efficiency, automatic verification of correctness and security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0068] The present invention will be described in detail below in conjunction with the accompanying drawings and specific embodiments. This embodiment is carried out on the premise of the technical solution of the present invention, and detailed implementation and specific operation process are given, but the protection scope of the present invention is not limited to the following embodiments.
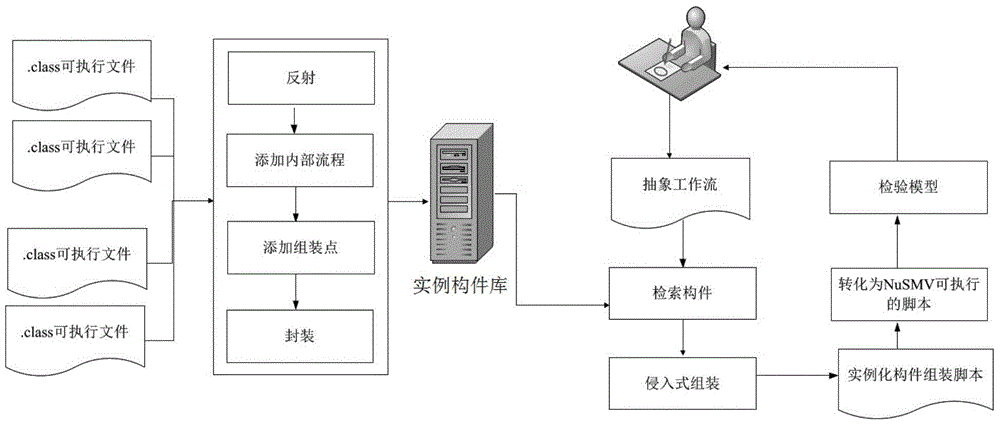
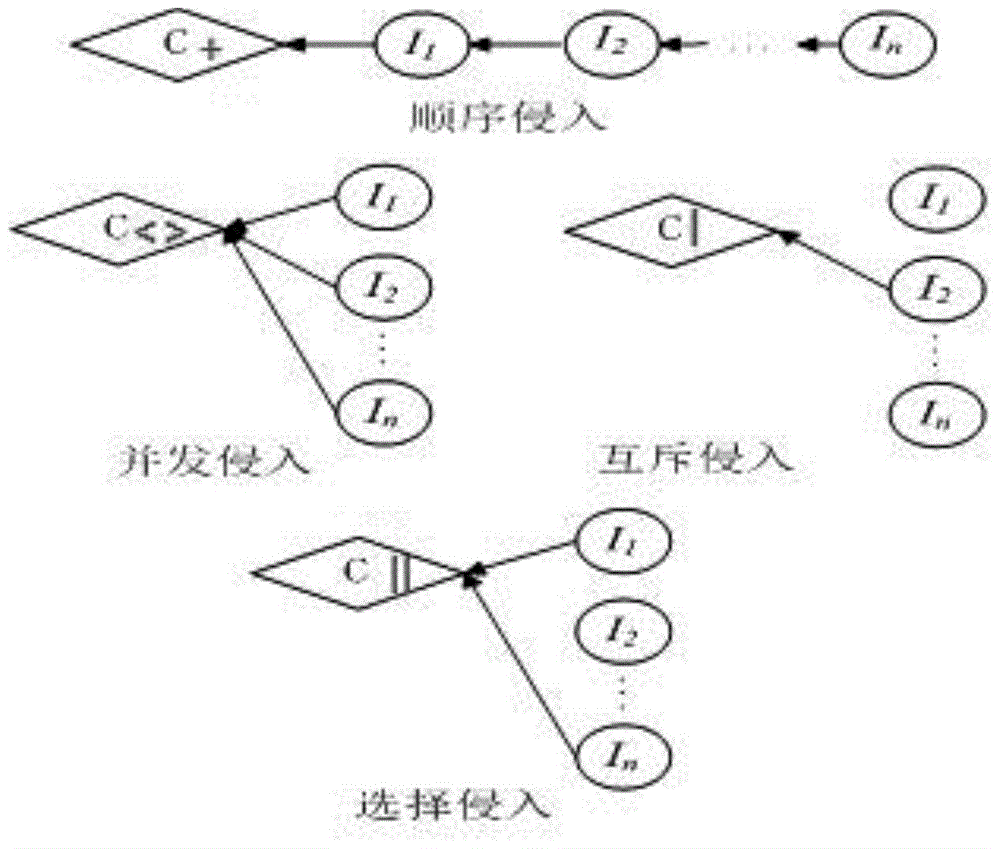
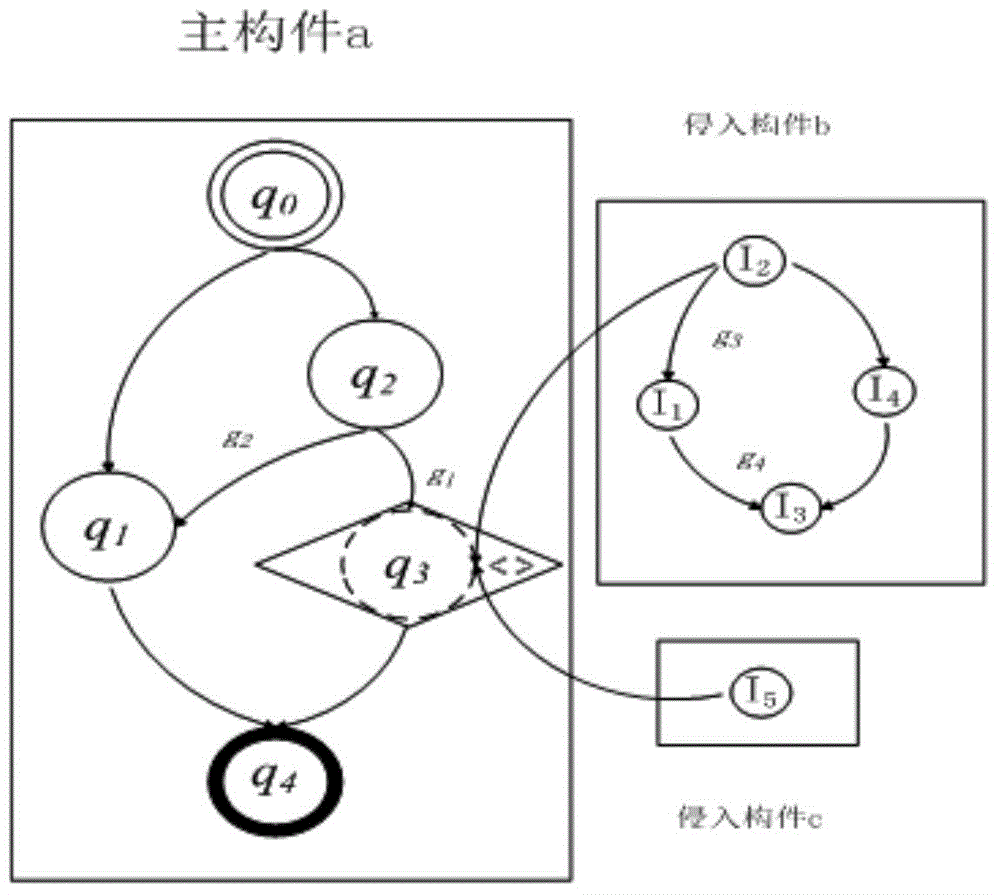
[0069] A Model-Based Approach to Intrusive Gray-Box Assembly Verification as figure 1 As shown, firstly, the Java executable program is parsed using reflection technology, and the internal process logic and assembly points are added, and the assembly points are added, and encapsulated into the component library. Secondly, users design abstract workflows on the visual interface according to their needs. Next, for the workflow, the satisfiable singleton artifacts are retrieved from the service repository. If there is no satisfying instance component, an algorithm is used to intrude mu...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com