Symmetric cipher table and symmetric key algorithm
A symmetric password and symmetric encryption technology, applied in electrical components, user identity/authority verification, transmission systems, etc., can solve the problems of easy password peeping, bank card theft, magnetic stripe bank card cloning, and theft.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
example 1
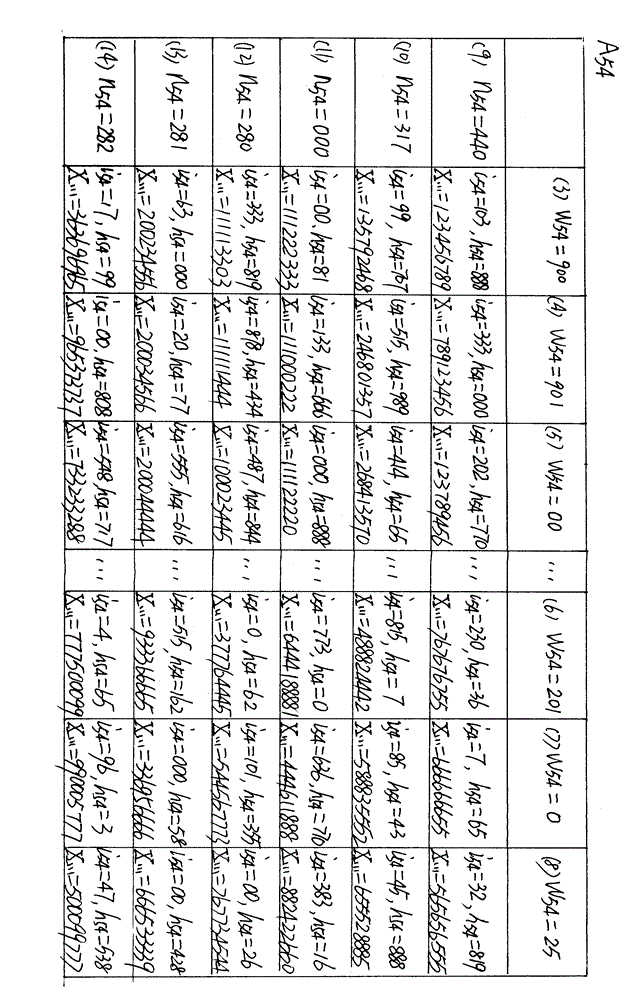
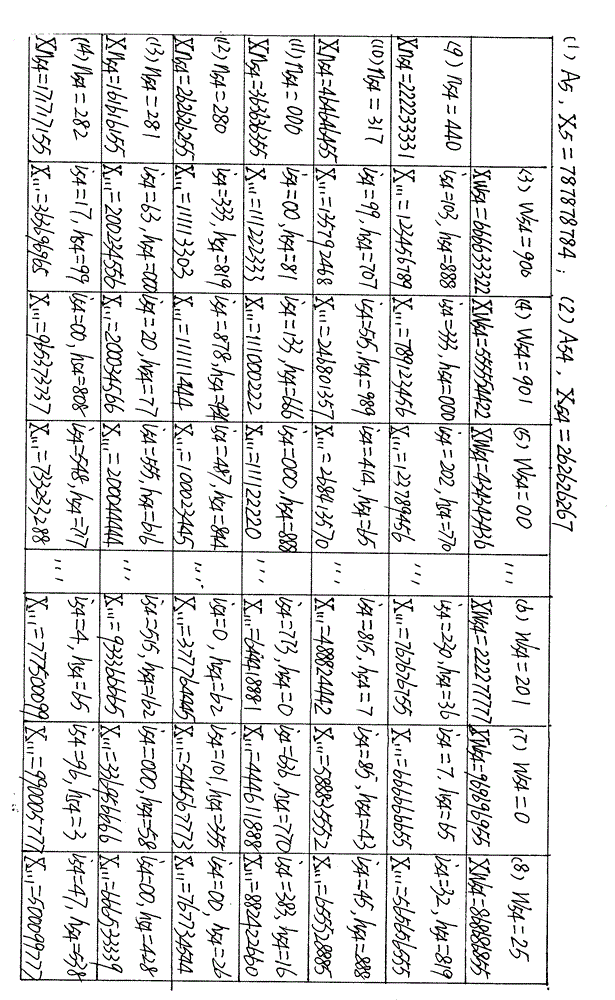
[0088] Example 1, such as figure 1 , A5 is the fifth symmetric password table (c=5) in A; A54 is the fourth password area (c=5, y=4) in the symmetric password table A5.
[0089] In Acy, there are altogether Icy common rows and Hcy common column password characters; the common row number is ncy, the common column number is wcy, and each password character corresponds to ncy and wcy. In this example, in A54, there are altogether the password characters of 999 public rows (I54=999), 999 public columns (H54=999); Vertical is row, and horizontal is column; Each public row has a public row number n54 , for example, n54 = ..., 440, 317, 000, 280, 281, 282, ...; each common column has a common column number w54, eg, w54 = ..., 900, 901, 00, ..., 201, 0, 25, ...; For example, in A54, the password character 123456789 corresponds to the public row 440 and the public column 900, and the password character 246801357 corresponds to the public row 317 and the public column 901, ....
[00...
example 2
[0105] Example 2, assuming that the plaintext L to be encrypted is 00555.
[0106] (1) if figure 2 , have the symmetric cipher table as claimed in claim 1, claim 2, claim 3, claim 4 (included in symmetric cipher system A, AI and AII are identical); A5 is the No. 5 symmetric cipher table in A , A54 is the No. 4 password area in A5.
[0107] (2) According to the preset program in AI, plaintext L (00555) is divided into 1 segment (L1), f=F=1; L1 is the plaintext character segment in L, further, L1 is divided into 2 groups ( L11, L12), L1g1 is the plaintext character group (1≤g1≤G1) in L1, Gf=G1=2; so, 00555 (=L=L1) is divided into L11, L12; When gf=g1=1 , Lfgf=Lfg1=L11=00; when gf=g1=2, LfGf=L1G1=Lfgf=Lfg1=L12=555.
[0108] (3) According to the preset program in AI:
[0109] ③: When Gf≥2, Lfgf corresponds to Jfgf. In this example, when f=1, gf=g1=1, "Lfgf and Jfgf in AI correspond to each other" in the above ① refers to "L11 corresponds to (mapping) J11 in A54" (Lfgf is L1...
example 3
[0123] Example 3, when Gf≥2, ..., the forward series has one or more of the following 10 forms. In this example, in the 5th form, the row element (fgf) is connected forward to the column element [f(gf+1)]; further, as described in the third situation in claim 8, icy(fgf ) is forward concatenated to the column element [f(gf+1)] involving icy(fgf).
[0124] Assuming that the plaintext L to be encrypted is 99888 (L=L1, L11=99, L12=888); L11 corresponds to (mapping) J11; suppose, J11=icy(11), then L11 corresponds to (mapping) icy(11), then icy(11)=99.
[0125] like figure 2(A54); Suppose, icy (11) is located on the public column 900 in A54 (w54=900), and after searching, it is found that i54=99 at the public column 900 and public row 317, so, i54 at this place Temporarily become i54(11), i54(11)=99, L11 corresponds (maps) this i54(11); because, the i54 at this place becomes i54(11) temporarily, so, at this place, n54(=317) involves The same i54 (11) at this place temporarily ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com