Mobile terminal secrecy system and method based on quantum true random number
A quantum random number and true random number technology, applied in digital transmission systems, transmission systems, and key distribution, can solve the problem that there is no similar technology application in the field of relay service security, it is difficult to meet the high-speed requirements of mobile communications, and it is impossible to quickly generate true random numbers And other issues
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
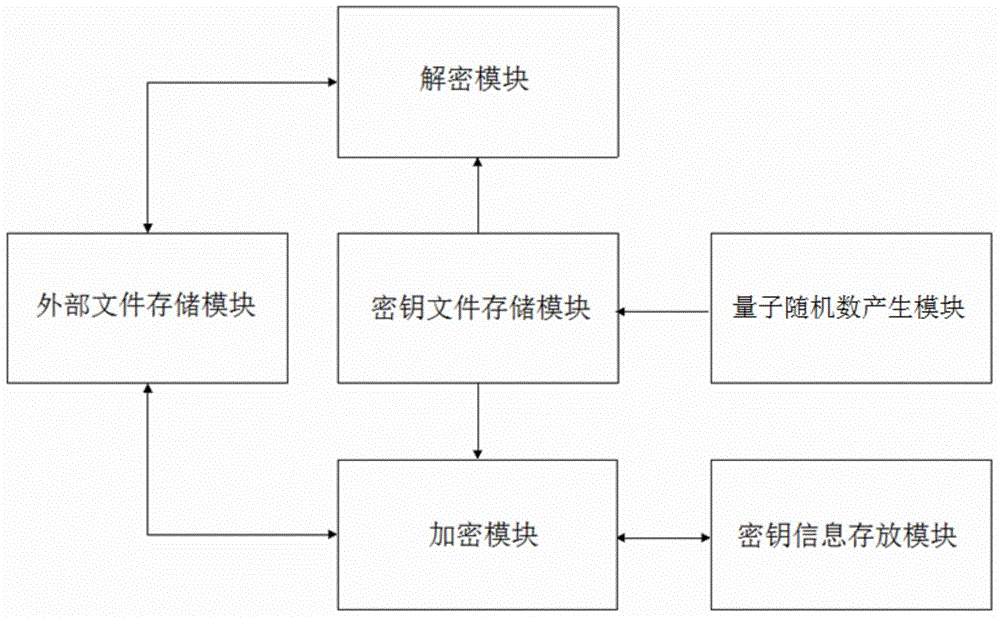
[0022] Such as figure 2 As shown, in this embodiment, the system of the present invention is pre-installed on the mobile terminal, and its security method specifically includes the following steps:
[0023] Step 1, detect whether the random number key information is reserved in the mobile terminal, when not, generate the random number key information by the quantum random number generation module and store it in the mobile terminal key file storage module, when there are enough keys in the mobile terminal For the key file, skip step 1 and go directly to step 2;
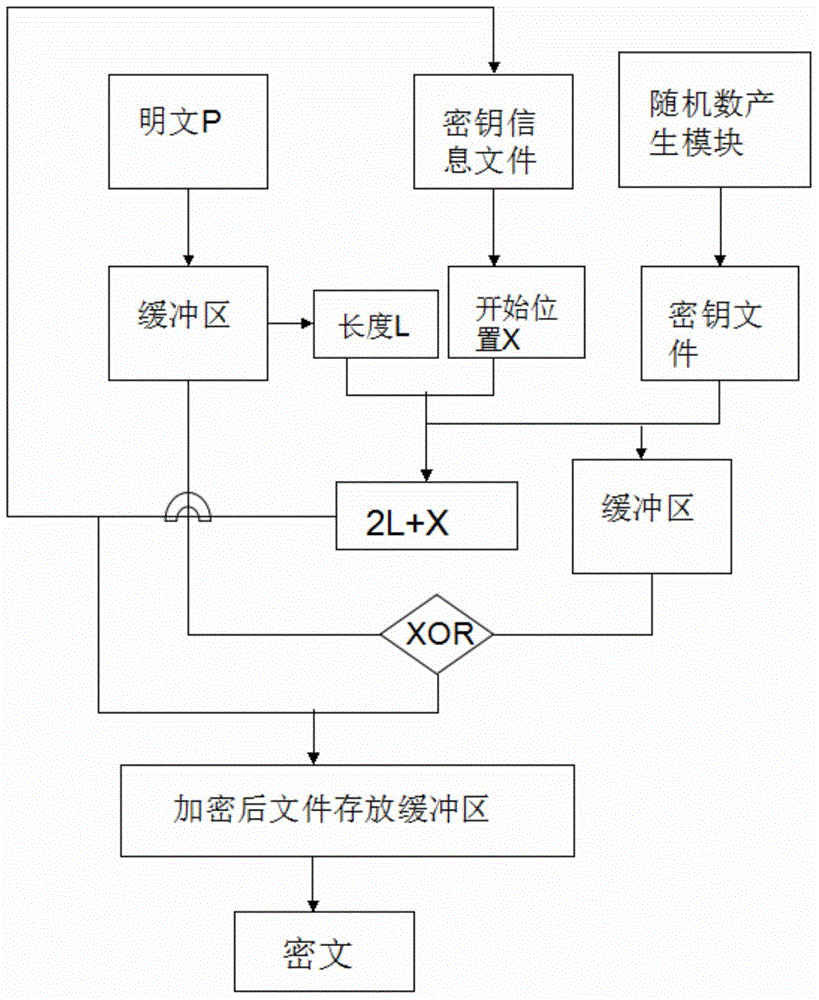
[0024] The random number key information consumes the key according to the number of times of encryption and the amount of use each time after the random number is generated, specifically: the number of times of encryption and the number of times of each The usage amount of is stored as key usage information, which determines where the next encryption starts, so that the used key will not be used next time.
[0025...
Embodiment 2
[0038] This embodiment decrypts the above-mentioned encrypted file, which specifically includes the following steps:
[0039] Step a, the user generates a certain capacity of random number key information through the quantum random number generation module and stores it in the key file storage module, if there are enough key files in the mobile terminal, skip step a and directly proceed to step b.
[0040] Step b. The user selects the file to be decrypted from the external file storage module. If the selected file is not of the "*.quantum" type, it prompts that the selected file does not need to be decrypted, and ends the operation. Otherwise, proceed to step b.
[0041] Step c, read the file to be decrypted from the external file storage module in the form of a byte stream and save it in a byte array buffer, and obtain the key file to start reading according to the first N bytes of the byte array position x d (that is, the updated key usage information content), the content ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com