Data exchange method and device thereof based on HTTP protocol
An HTTP protocol, data interaction technology, applied in the field of data interaction, can solve problems such as data leakage, and achieve the effect of ensuring security, ensuring information security, and ensuring information security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
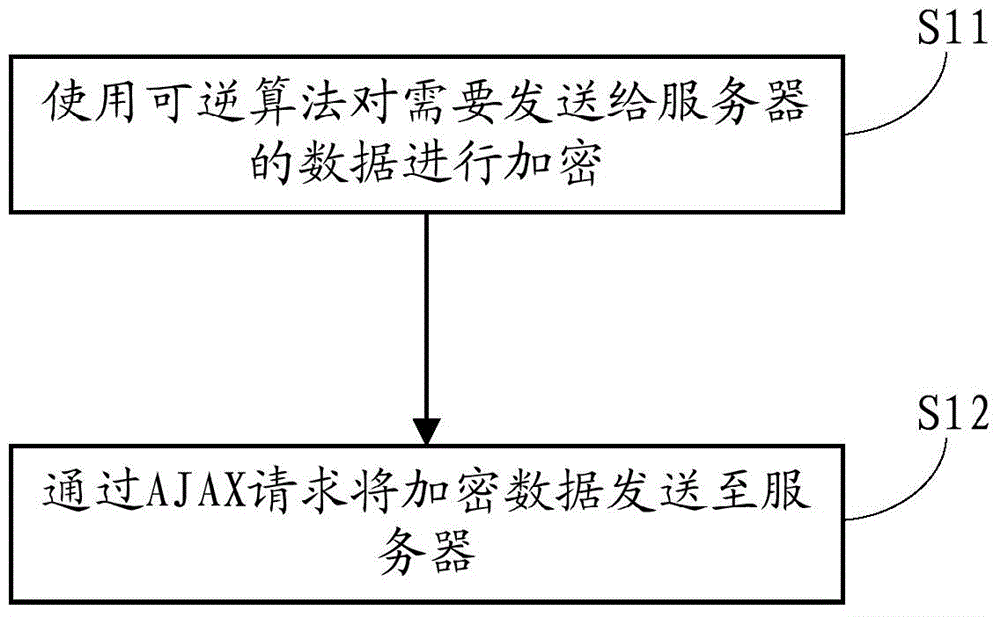
[0056] figure 1 It is a flow chart of a data interaction method based on the HTTP protocol shown according to an exemplary embodiment, such as figure 1 As shown, the data interaction method based on the HTTP protocol is used in a client of a web browser or other WEB applications, including the following steps S11-S12:
[0057] In step S11, a reversible algorithm is used to encrypt the data to be sent to the server.
[0058] When the user performs an operation on the web browser or other WEB application client, so that the client needs to send data to the server, the client will use a reversible algorithm to check the data to be sent or a specific data in the data Fields are encrypted, and the encryption process can be done by client-side scripts.
[0059] In one embodiment, the reversible algorithm may be a simple algorithm: y=f(x,m), where x is the data to be sent to the server, y is the encrypted data, and m is the encryption key.
[0060] In step S12, the encrypted data ...
Embodiment 2
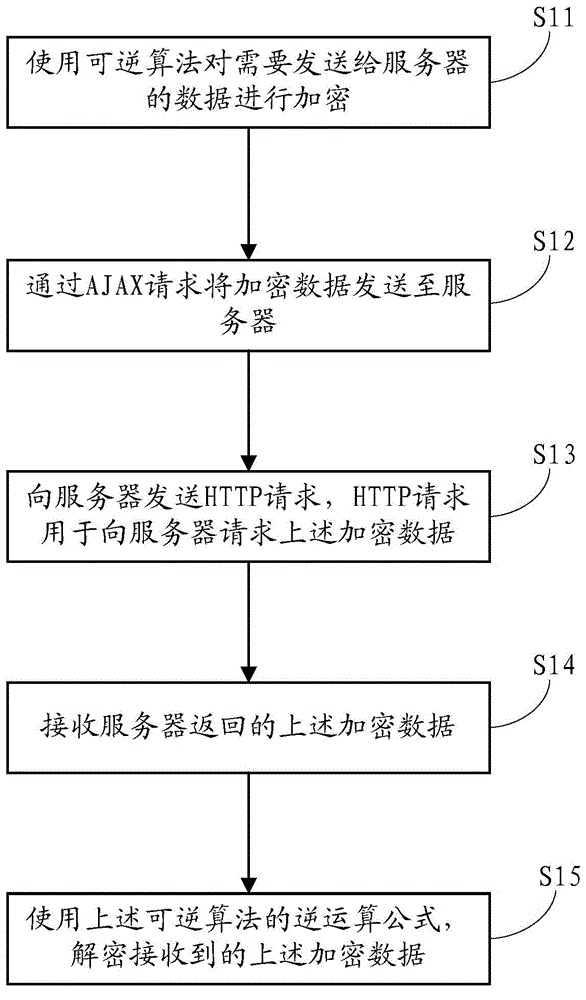
[0064] figure 2 It is a flow chart of another data interaction method based on the HTTP protocol shown according to an exemplary embodiment on the basis of Embodiment 1 of the present disclosure, as shown in figure 2 As shown, the data interaction method is used in the client of the above-mentioned web browser or other WEB applications, and the above-mentioned data interaction method may further include the following steps after the above-mentioned step S12:
[0065] In step S13, an HTTP request is sent to the server, and the HTTP request is used to request the encrypted data from the server.
[0066] When the client needs to request the encrypted data stored on the server, the client sends an HTTP request to request the server to return the encrypted data.
[0067] In step S14, the above-mentioned encrypted data returned by the server is received.
[0068] Using AJAX, the above encrypted data returned by the server is received.
[0069] In step S15, the received encrypte...
Embodiment 3
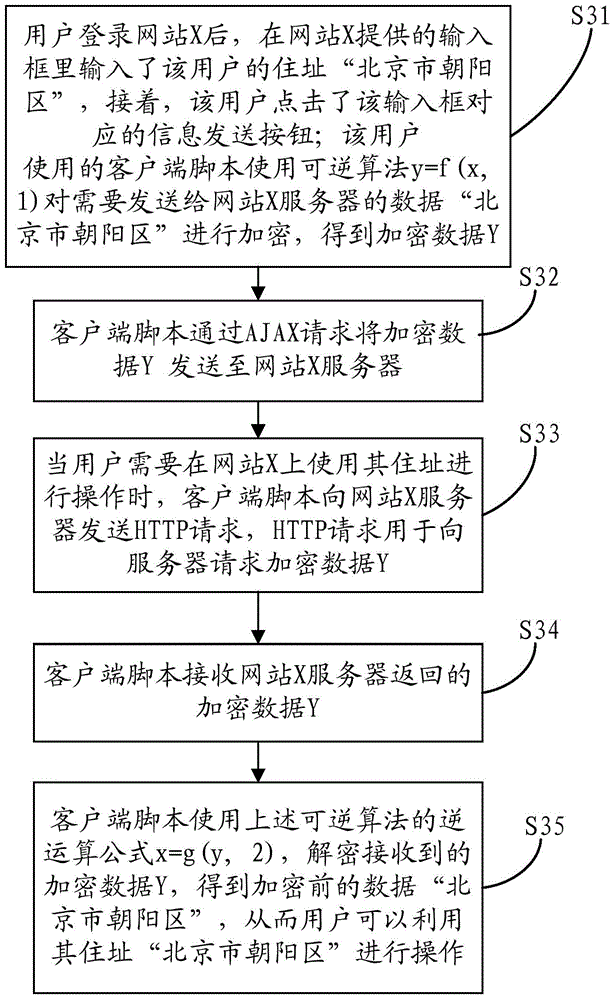
[0076] image 3 It is a flow chart of a data interaction method based on the HTTP protocol according to an exemplary embodiment based on the second embodiment of the present disclosure. The data interaction method is used in the following scenario: the user provides the user to the website X The address of the user is "Chaoyang District, Beijing". When the user uses the website in the later stage, the website will automatically display the user's address to the user for the user's convenience, without the need for the user to fill in the address repeatedly. Such as image 3 As shown, in this scenario, using the data interaction method based on the HTTP protocol provided by the embodiment of the present disclosure for data interaction includes the following steps:
[0077] In step S31, after the user logs in to website X, he enters the user's address "Chaoyang District, Beijing" in the input box provided by website X, and then, the user clicks the information sending button co...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com