URL detection method and device
A detection method and network technology, applied in the computer field, can solve problems such as insecurity and inability to accurately judge the safety of the network to be detected, and achieve the effect of avoiding economic losses
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
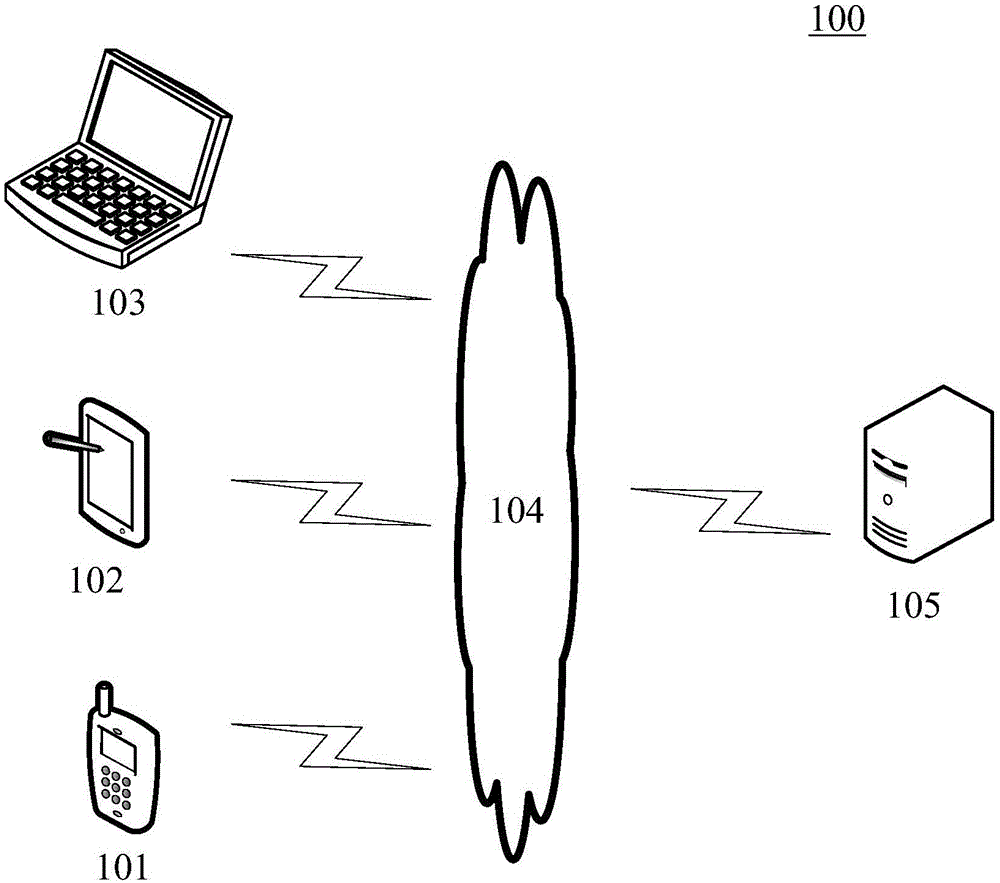
[0042] figure 1 An exemplary system architecture 100 to which embodiments of the method and device for detecting a website address of the present application can be applied is shown.
[0043] Such as figure 1 As shown, the system architecture 100 may include terminal devices 101, 102, 103, a network 104, and a server 105. The network 104 is used to provide a medium for communication links between the terminal devices 101, 102, 103 and the server 105. The network 104 may include various connection types, such as wired, wireless communication links, or fiber optic cables.
[0044] The user can use the terminal devices 101, 102, and 103 to interact with the server 105 through the network 104 to receive or send messages and so on. Various communication client applications may be installed on the terminal devices 101, 102, 103, for example, web site detection applications, shopping applications, search applications, instant messaging tools, email clients, social platform software, etc....
Embodiment 2
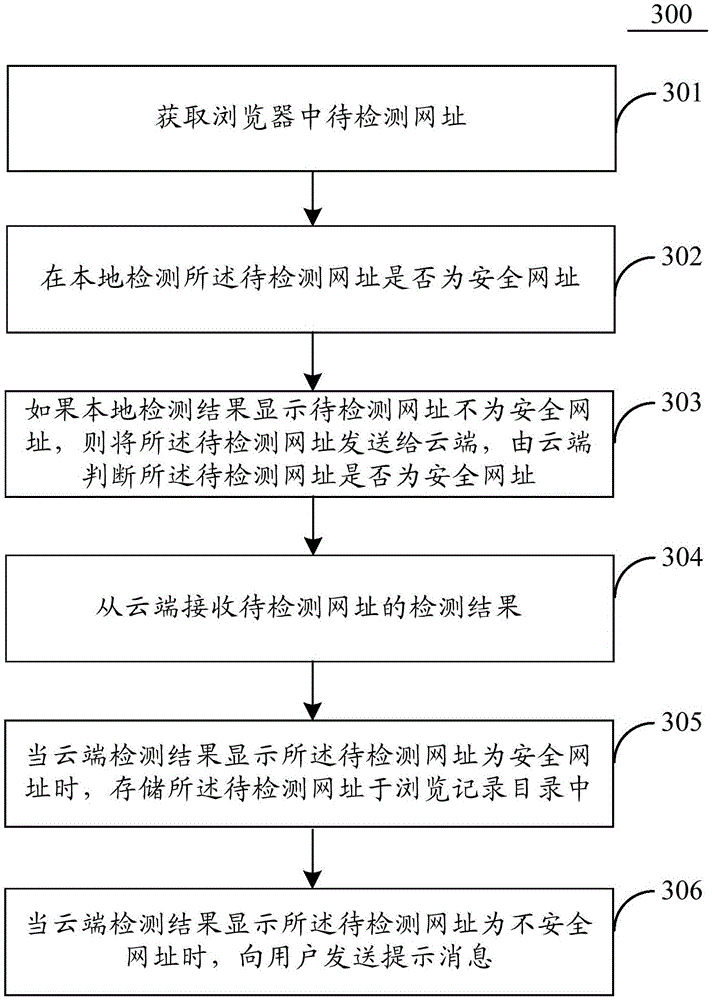
[0079] Figure 5 This is a flowchart of a method for detecting a website address provided by another embodiment of this application. The execution subject is the server 105 (the server may be a cloud server), see Figure 5 , URL detection method 500 specifically includes the following steps:
[0080] Step 501: Receive the URL to be detected sent by the client;
[0081] Step 502: Determine whether the URL to be detected is a secure URL;
[0082] Specifically, see Image 6 , Which shows a schematic diagram 600 of still another embodiment of detecting a secure or unsafe web address, and the cloud determines whether it is a secure web address specifically through the following steps:
[0083] Step 601: Pre-store a white list of secure web addresses and a black list of unsafe web addresses in the cloud;
[0084] Step 602: Match the URL to be detected with any unsafe URL in the blacklist, and when the URL to be detected matches any unsafe URL in the blacklist, determine the URL to be detected...
Embodiment 3
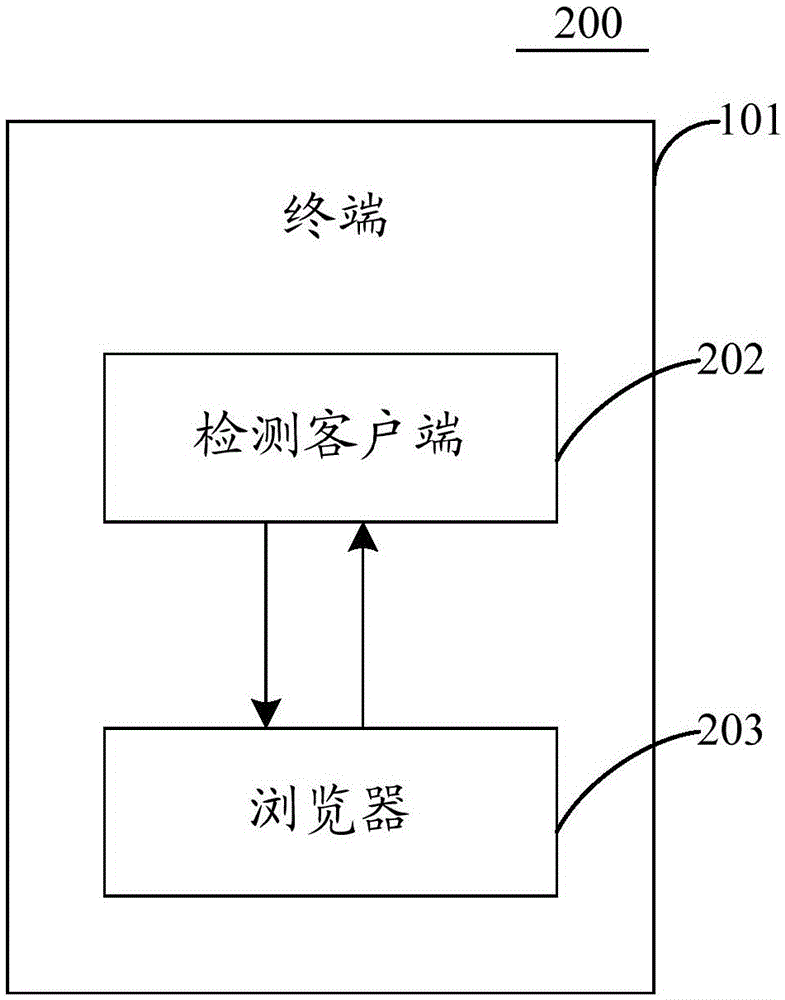
[0096] Corresponding to the method for detecting a website address provided in Embodiment 1 of the present application, an embodiment of the present application also provides an apparatus for detecting a website address. The execution body may be a detecting client, see Figure 7 As shown in the schematic diagram of the device for detecting a website address, the device 700 may specifically include: an acquiring unit 701, a detecting unit 702, a sending unit 703, a receiving unit 704, a storage unit 705, and a prompt unit 706.
[0097] The obtaining unit 701 is configured to obtain a web address to be detected in the browser;
[0098] The detecting unit 702 is configured to locally detect whether the web address to be detected is a safe web address;
[0099] The sending unit 703 is configured to send the to-be-detected website to the cloud if the local detection result shows that the to-be-detected website is not a safe website, and the cloud determines whether the to-be-detected webs...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - Generate Ideas
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com