K-anonymization based motion track data privacy protection method and system
A technology of data privacy and movement trajectory, applied in digital data protection, electronic digital data processing, instruments, etc., can solve the problem of single generalization attribute, and achieve the effect of strong scalability and adaptability
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0034] In order to better understand the technical content of the present invention, specific embodiments are given together with the attached drawings for description as follows.
[0035] Aspects of the invention are described in this disclosure with reference to the accompanying drawings, which show a number of illustrated embodiments. Embodiments of the present disclosure are not necessarily intended to include all aspects of the invention. It should be appreciated that the various concepts and embodiments described above, as well as those described in more detail below, can be implemented in any of numerous ways, since the concepts and embodiments disclosed herein are not limited to any implementation. In addition, some aspects of the present disclosure may be used alone or in any suitable combination with other aspects of the present disclosure.
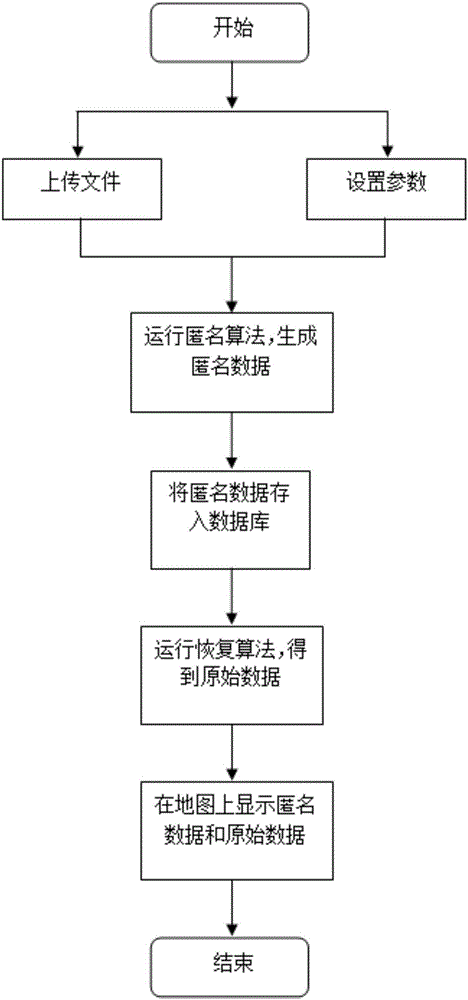
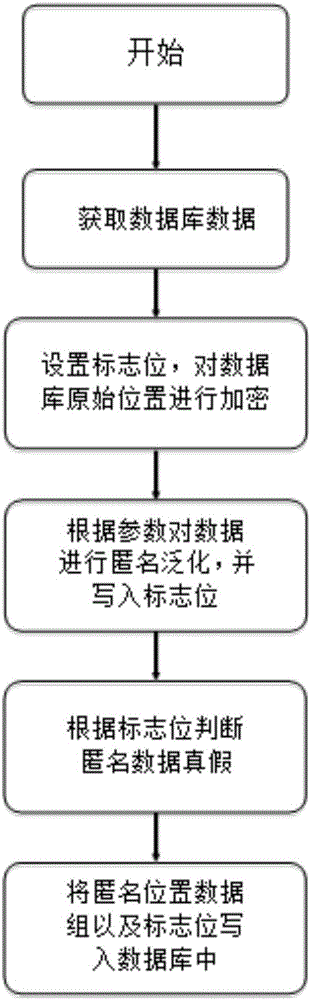
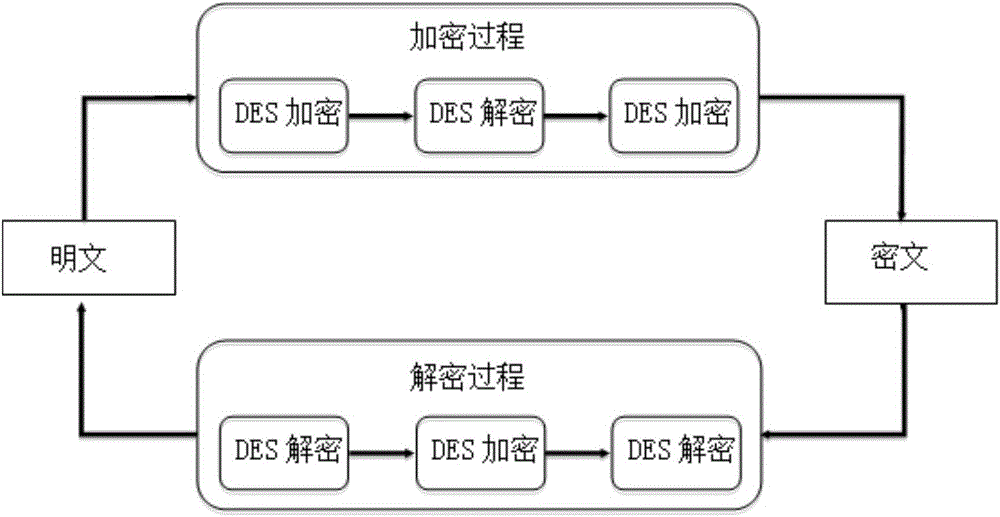
[0036] Such as figure 1 The flow chart of the K-anonymity-based motion trajectory data privacy protection method according ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com