Multi-dimensional spam message filtering method and system
A technology of spam text messages and filtering methods, which is applied in wireless communication, advanced technology, security devices, etc., and can solve problems such as wireless network resource shortage, only spam text messages, congestion, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0022] The specific implementation of the present invention will be described below in conjunction with the accompanying drawings, so that those skilled in the art can better understand the present invention. It should be particularly noted that in the following description, detailed descriptions of known functions and designs will be omitted when they may obscure the gist of the present invention.
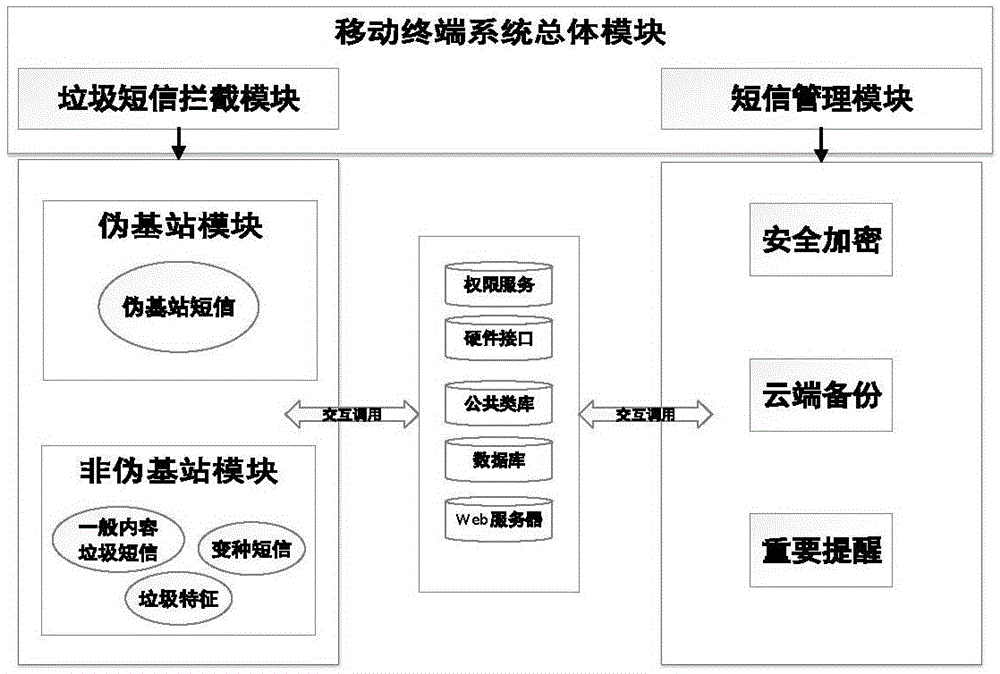
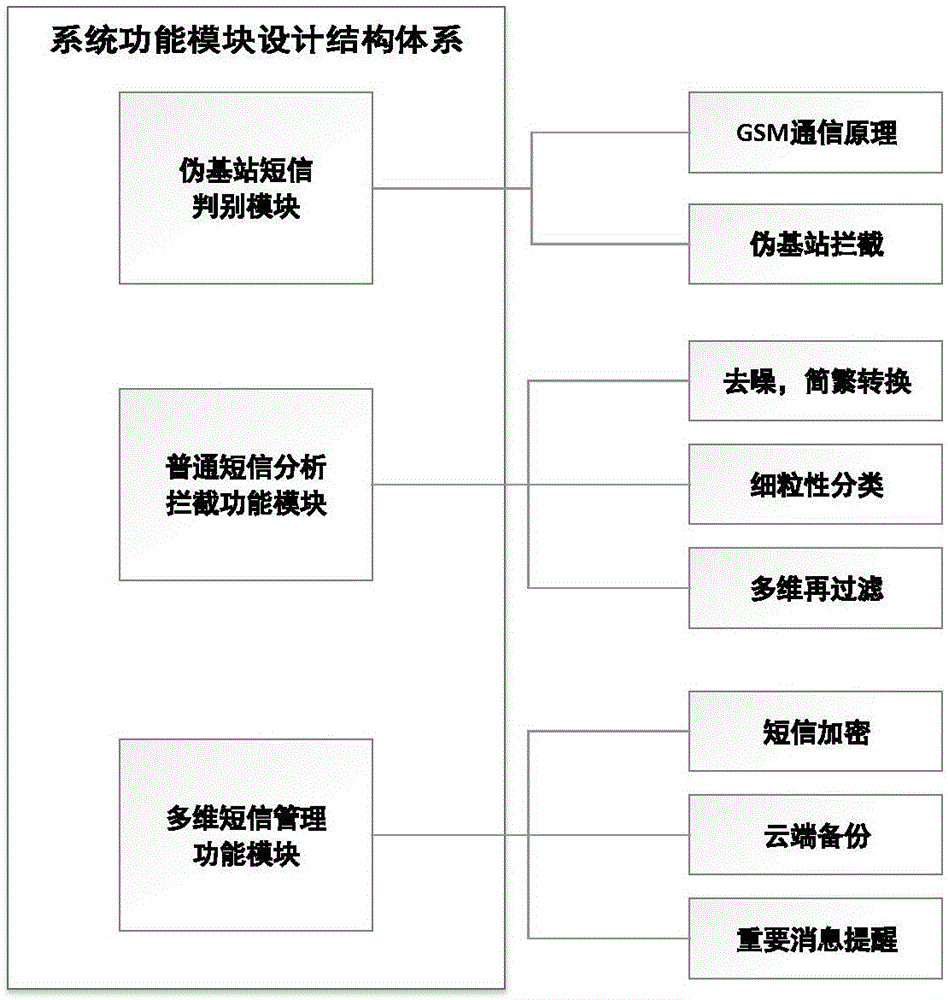
[0023] figure 1 , figure 2 It is the overall architecture and module relationship diagram of this protection system, which illustrates the main functions of each module and the control relationship between modules.
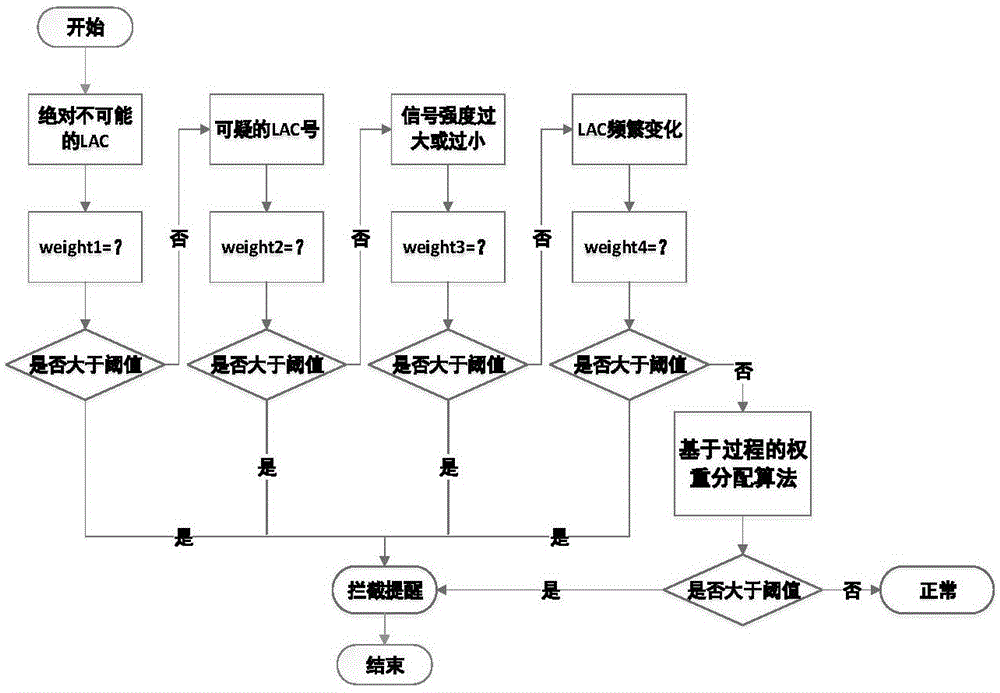
[0024] Turn on the pseudo-base station module, and first obtain the signal status of the mobile phone. If it remains stable for a period of time, the system will stay in the waiting state and will not execute the pseudo-base station discrimination algorithm; when the signal changes, the pseudo-base station discrimination algorithm will be executed, as follows:
[0...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com