Weak signature algorithm
An algorithm and hash algorithm technology, applied in electrical components, transmission systems, etc., can solve the problem of low success rate of digital signature communication, and achieve the effect of improving the success rate of communication and simplifying the public and private key signature algorithm.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0018] The beneficial effects of the present invention will be described in detail below in conjunction with the embodiments of the accompanying drawings, aiming at helping readers better understand the essence of the present invention, but not limiting the implementation and protection scope of the present invention.
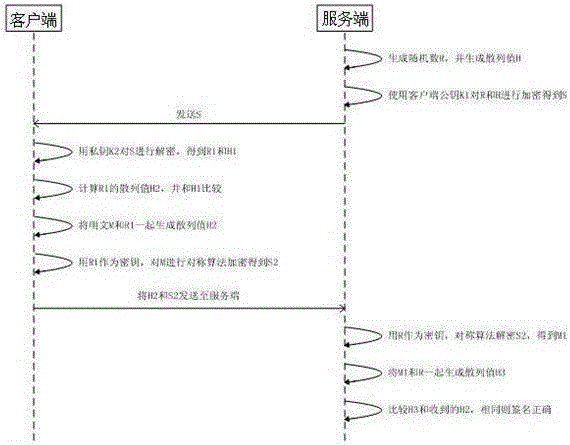
[0019] refer to figure 1 , the concrete steps of the present invention are as follows:
[0020] 1. The server generates a 128-bit random number R, and performs a sha1 hash operation on R to obtain a 20-byte H;
[0021] 2. The server uses the RSA public key K1 of the client to encrypt R and H to generate ciphertext S. The encryption algorithm is the RSA algorithm, and the key length is 1024 bits;
[0022] 3. The server transmits the ciphertext S to the client;
[0023] 4. The client decrypts S with its own private key K2, decrypts R1 and H1, and calculates the sha1 hash operation value H2 of R1, and compares H1 and H2. If they are different, the ciphertext S i...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com