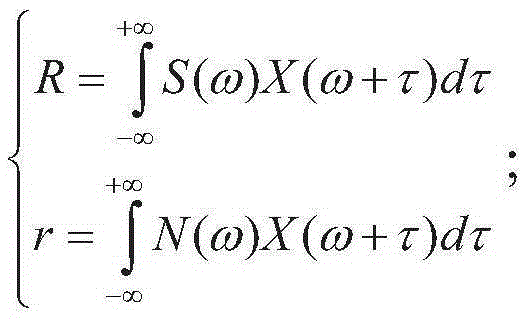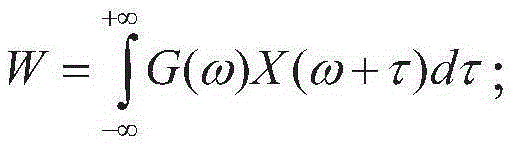Position spoofing attack detection method for frequency modulation signal indoor positioning system
An FM signal, indoor positioning technology, applied in the field of communication, can solve the problem of position information acquisition error, positioning system position determination error and other problems
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0042] The present invention will be further described below in conjunction with the accompanying drawings. It should be noted that this embodiment is based on the technical solution, and provides detailed implementation and specific operation process, but the protection scope of the present invention is not limited to the present invention. Example.
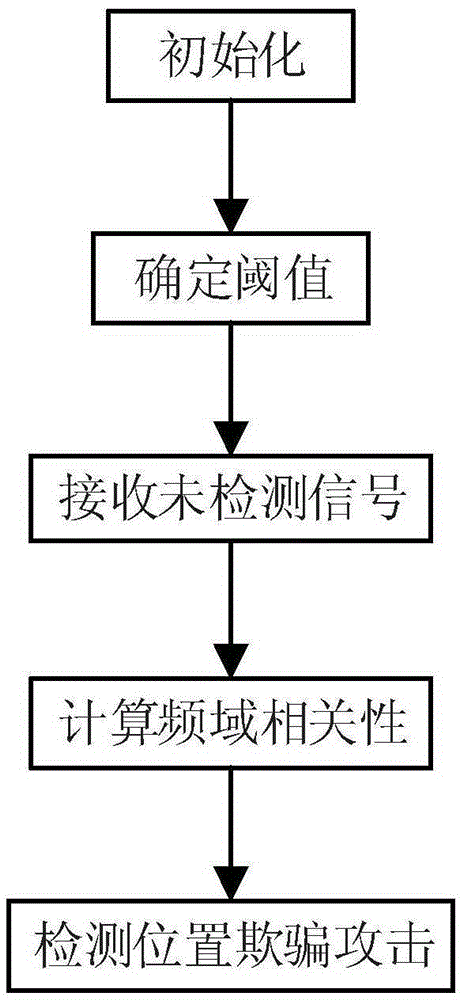
[0043] The application scenario of the present invention is an FM signal indoor positioning system, and the system includes a FM signal base station, an attacker and a normal user. The user calculates the cross-correlation between the received undetected signal and the FM carrier signal spectrum, uses the upper and lower thresholds to determine the signal type, and obtains the detection result of the location spoofing attack.
[0044] Such as figure 1 Shown, concrete steps of the present invention are as follows:
[0045] Step 1, initialization.
[0046] 1.1) The user uses his own antenna to receive 100 times of natural noise...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com