Method and device for realizing safe interaction and pairing authentication between Bluetooth devices
A bluetooth device, safe technology, applied in the field of information security, can solve problems such as wrong device connection, cumbersome pairing operation process, and low security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
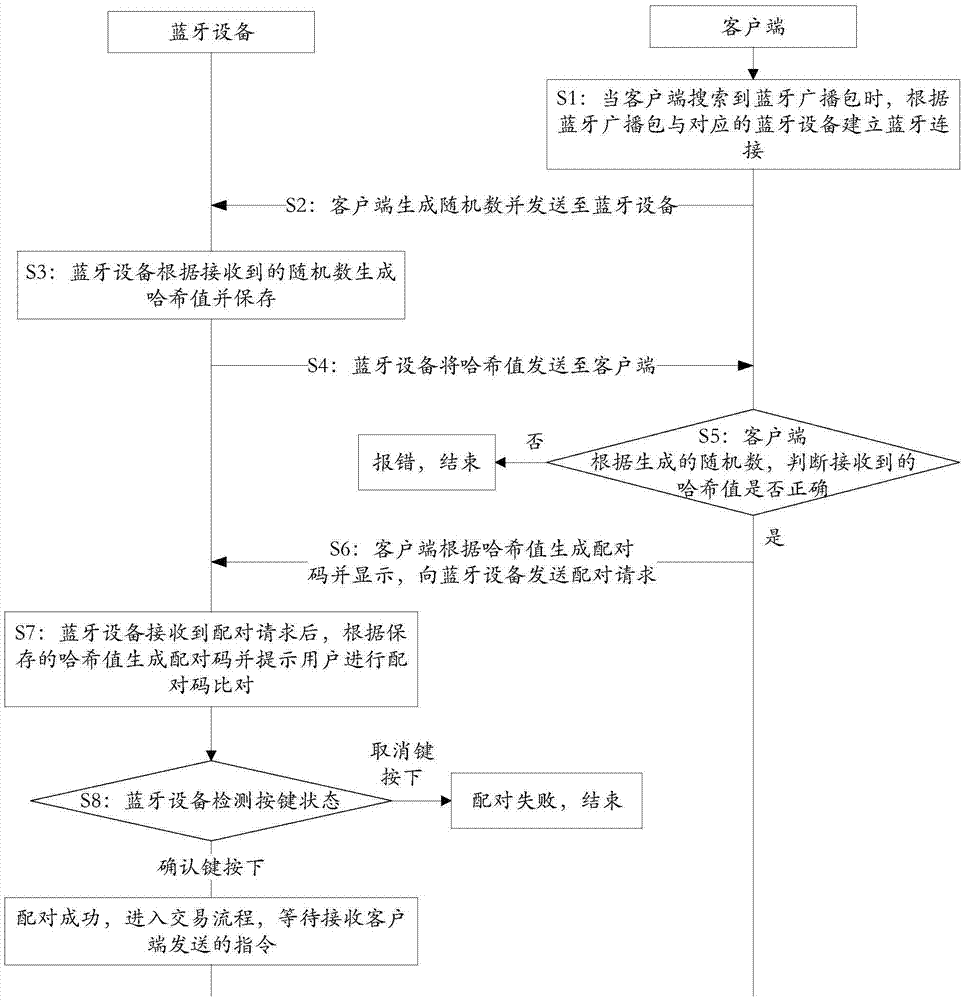
[0215] Embodiment 1 of the present invention provides a method for implementing secure interactive pairing authentication between Bluetooth devices, which is applied to a system composed of Bluetooth devices and clients, such as figure 1 shown, including:
[0216] Step S1: When the client searches for the Bluetooth broadcast packet, establish a Bluetooth connection with the corresponding Bluetooth device according to the Bluetooth broadcast packet;
[0217] Step S2: The client generates a random number and sends it to the Bluetooth device;
[0218] In this embodiment, after the Bluetooth connection is established, it further includes: the client negotiates a session key with the Bluetooth device;
[0219] Specifically: the client generates a session key, encrypts the session key with the pre-saved public key, and sends the encrypted result to the Bluetooth device, and the Bluetooth device uses the pre-saved private key to decrypt the received encrypted result to obtain the se...
Embodiment 2
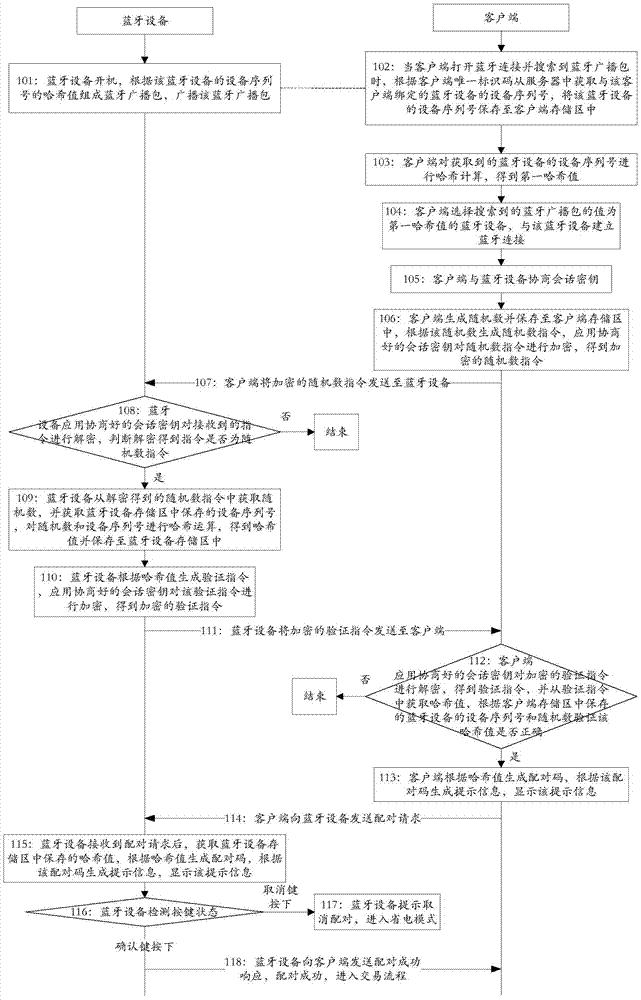
[0242] Embodiment 2 of the present invention provides a method for realizing secure interactive pairing authentication between Bluetooth devices, which is applied to a system composed of Bluetooth devices and clients, wherein the Bluetooth device is specifically a smart key device with Bluetooth functions, and the client is Application programs for transactions installed on mobile devices (mobile phones, pads and other Bluetooth-enabled terminal devices), such as figure 2 As shown, when the client enters the need to connect the Bluetooth device to sign the transaction, perform the following operations:
[0243] Step 101: Start the Bluetooth device, form a Bluetooth broadcast packet according to the hash value of the device serial number of the Bluetooth device, and broadcast the Bluetooth broadcast packet;
[0244] In this embodiment, the Bluetooth broadcast packet is composed according to the hash value of the device serial number of the Bluetooth device, specifically:
[0...
Embodiment 3
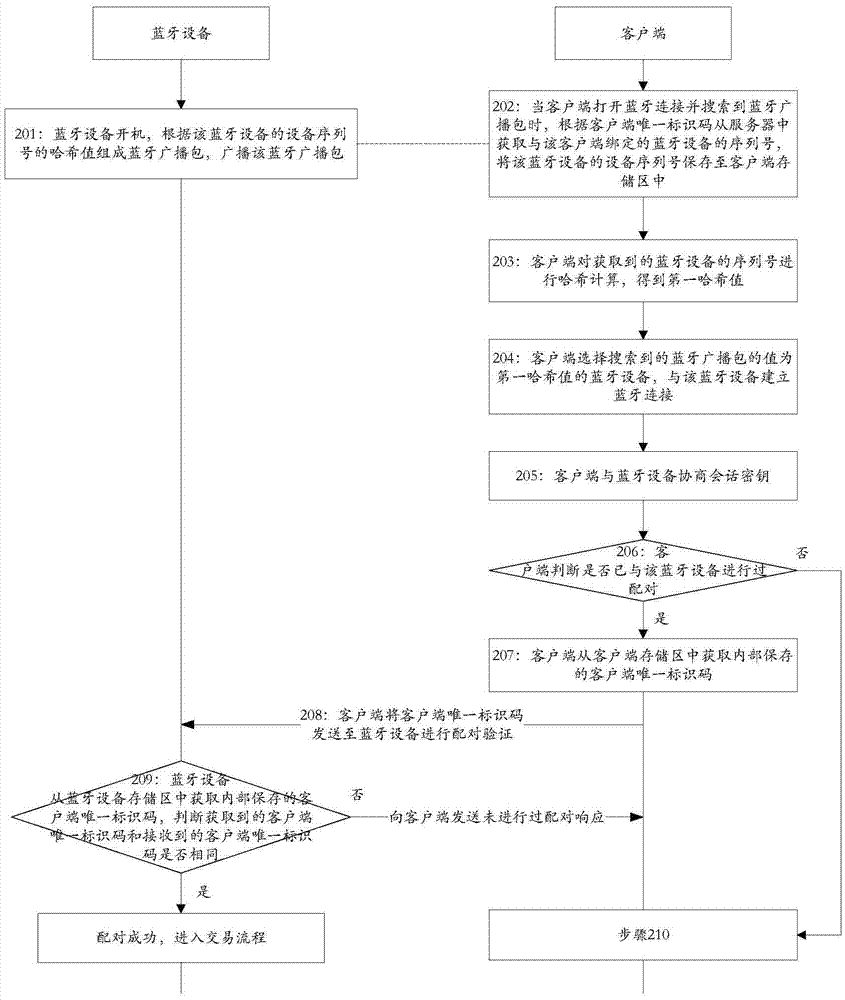
[0299] Embodiment 3 of the present invention provides a method for implementing secure interactive pairing authentication between Bluetooth devices, which is applied to a system composed of Bluetooth devices and clients, wherein the Bluetooth device is specifically a smart key device with Bluetooth functions, and the client is Application programs for transactions installed on mobile devices (mobile phones, pads and other Bluetooth-enabled terminal devices), such as image 3 and Figure 4 shown, including:
[0300] Step 201: Start the Bluetooth device, form a Bluetooth broadcast packet according to the hash value of the device serial number of the Bluetooth device, and broadcast the Bluetooth broadcast packet;
[0301] In this embodiment, the Bluetooth broadcast packet is composed according to the hash value of the device serial number of the Bluetooth device, specifically:
[0302] The Bluetooth device obtains the hash value of the internally stored device serial number fro...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com