Fake-locus-based location privacy protection method for use in recommendation system
A recommendation system and trajectory technology, applied in the field of mobile social networks, can solve problems such as service quality limitation, location leakage, and failure to consider the semantic attributes of location data, so as to reduce computational complexity and ensure security.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0037] specific implementation plan
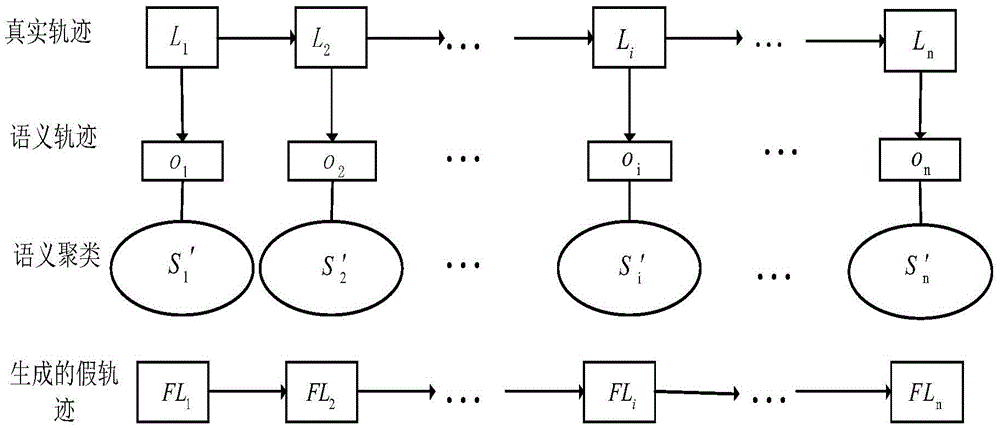
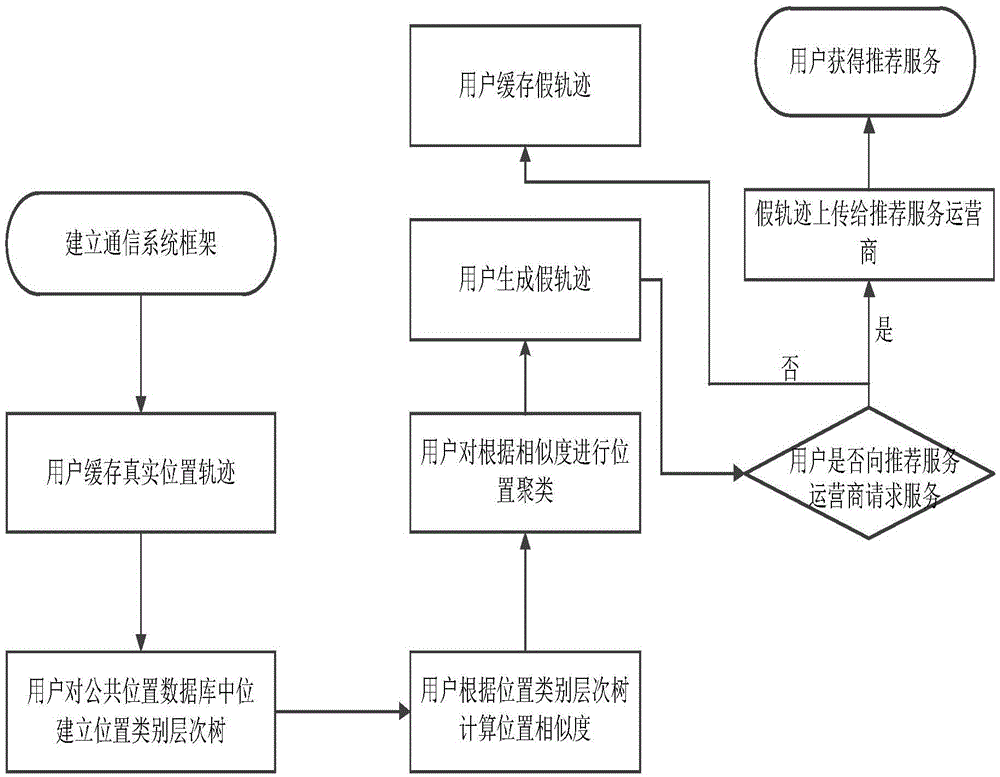
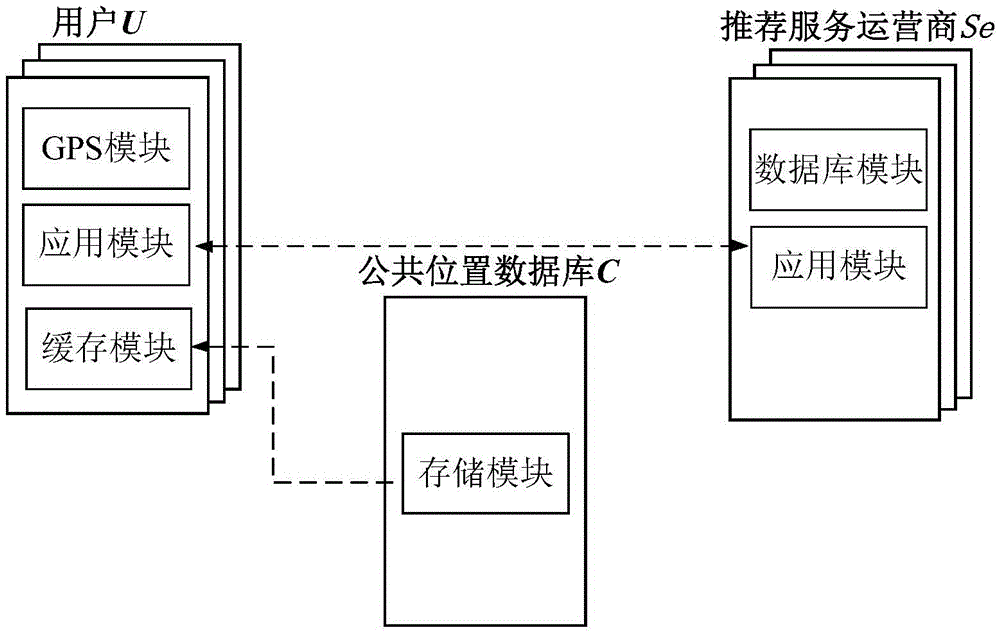
[0038] refer to figure 1 , the core idea of the present invention is that the user extracts the semantic attributes of each position in the real trajectory TR to form a semantic sequence O={o 1 ,o 2 ,o 3 ,...,o i ,o i+1 ,...,o n}, and then according to the semantic sequence O, the positions in the public location database are classified according to their corresponding semantic attributes, forming a semantic class S={S 1 ,S 2 ,...,S i ,S i+1 ,...,S n}, in order to protect the privacy of the user’s location, the location in the real trajectory TR is removed from the semantic class S to form a cluster S′=S-TR. False trajectory FL={FL 1 ,FL 2 ,...,FL i ,FL i+1 ,...,FL n} can be modeled as a Hidden Markov Model, where O={o 1 ,o 2 ,o 3 ,...,o i ,o i+1 ,...,o n} as the observable sequence in the hidden Markov model, and the position sequence in S′ as the hidden sequence in the hidden Markov model, the user uses the Viterbi...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com