Intelligent access control system and operation method thereof
An intelligent access control system, access control system technology, applied in instruments, time registers, individual input/output registers, etc., can solve problems such as increased after-sales maintenance costs, low safety factor, and loopholes in security mechanisms, reducing The effect of after-sales maintenance costs, reducing excessive dependence, and reducing communication links
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0029] In order to make the object, technical solution and advantages of the present invention clearer, the present invention will be further described in detail below in conjunction with the accompanying drawings.
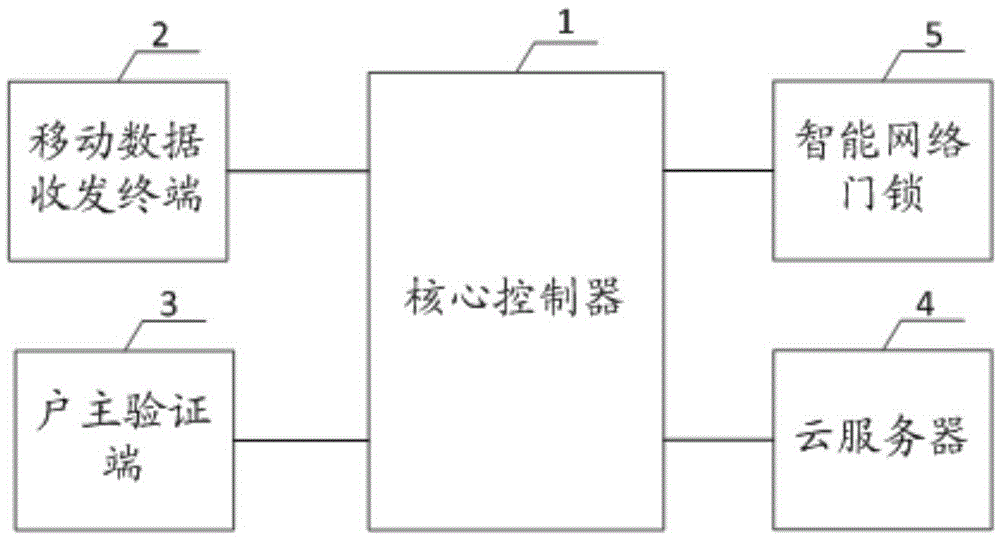
[0030] Such as figure 1 As shown, it is an intelligent access control system provided in the embodiment of the present invention. The access control system includes a core controller 1, and a mobile data transceiver terminal 2 connected to the core controller 1, a householder verification terminal 3, and a cloud server. 4 and intelligent network door lock 5; wherein,
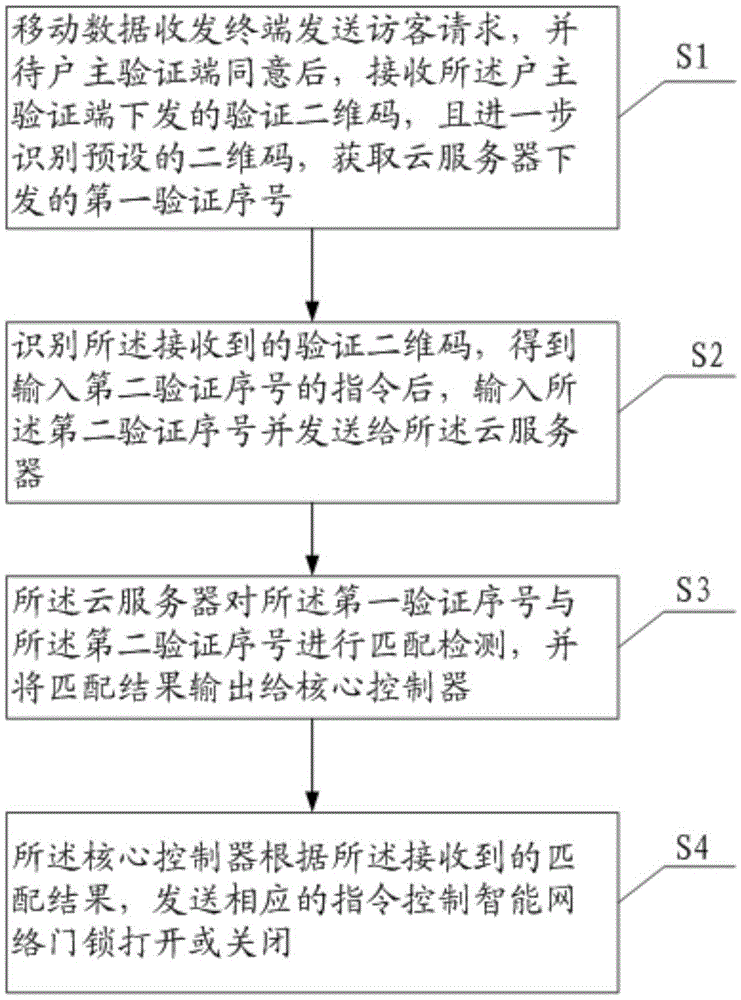
[0031] The mobile data transceiver terminal 2 is used to send visitor requests and receive the verification QR code issued by the owner verification terminal 3, and obtain the first verification serial number issued by the cloud server 4 by identifying the preset QR code, and further pass the identification After verifying the two-dimensional code issued by the verification terminal 3 of the househ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com