Password verification method and system
A password verification and command technology, applied in the field of communication, can solve problems such as the threat of USBKEY security use, achieve the effect of defending against higher-level attacks, improving user experience, and improving response speed
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0063]The following will clearly and completely describe the technical solutions in the embodiments of the present invention with reference to the drawings in the embodiments of the present invention.
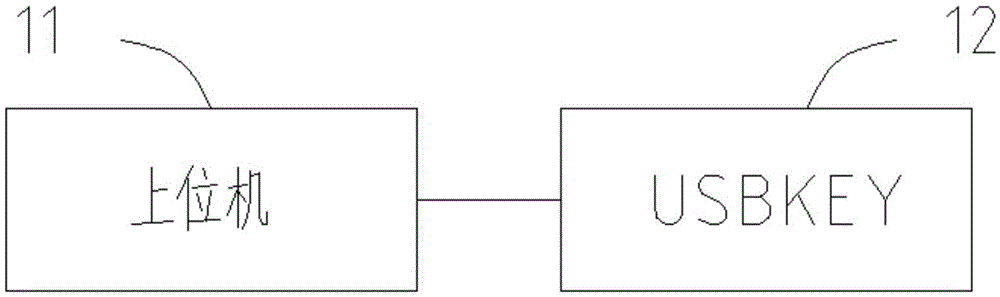
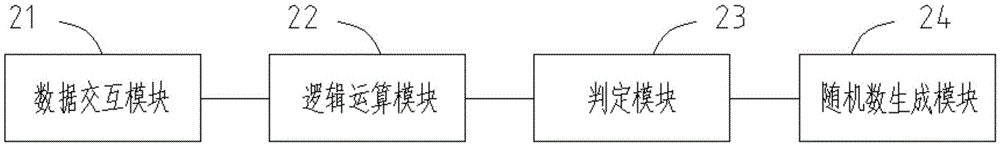
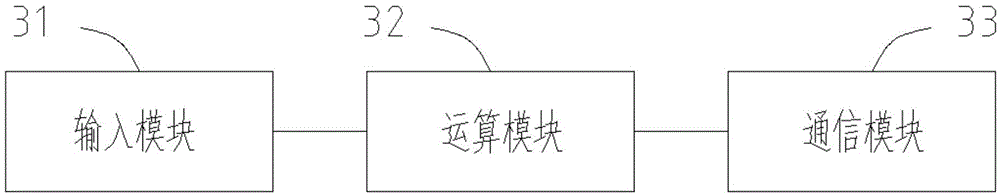
[0064] A kind of password verification system proposed by this application, such as figure 1 As shown, including host computer 11 and USBKEY12, specifically, as image 3 As shown, the host computer 11 includes:
[0065] The input module 31 is used for the user to input the PIN code.
[0066] More specifically, when the PIN code input by the user in the input module 31 personalizes the USBKEY 12, the bank center issues a bound personal identification code to the USBKEY 12.
[0067] The PIN code binding process specifically includes:
[0068] First, the bank host requests USBKEY12 information from the bank center server, and queries the PIN code status of the corresponding USBKEY12 according to the USBKEY12 information returned by the bank center server, and then the bank host...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com